A Proof of Concept Exploit for the “Windows Zerologon” Flaw is Out
- Researchers released a simple and easy to use way to exploit “CVE-2020-1472”, the Windows Zerologon flaw.
- This problem was addressed in the August 2020 Tuesday Patch, and the fix will be enforced in February 2021.
- There’s a testing script out to help system admins determine if they’re vulnerable to the PoC or not.
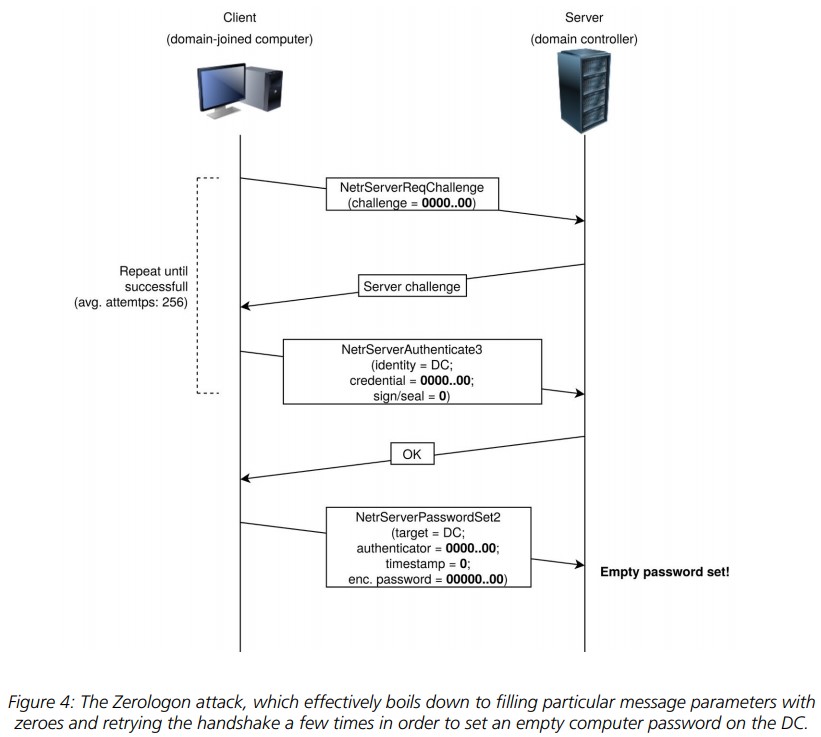
Researchers at Secura have released a proof of concept (PoC) exploit for the Windows Zerologon “CVE-2020-1472” vulnerability that was addressed by Microsoft with the August 2020 Patch Tuesday pack. This was a highly critical flaw that received a severity level of 10.0 in the CVSS scale and concerned the Netlogon Remote Protocol cryptographic authentication scheme. The flaw could potentially enable an attacker to impersonate a client computer and gain domain admin rights to remote systems without having the actual password.
Source: Secura
Having a PoC on how to trigger this vulnerability makes a huge difference from just having the mere knowledge of its existence, as malicious actors can now take the code and weaponize it. As soon as that happens, hackers will scan for vulnerable machines and will launch their attacks with absolute certainty about its success. The first compromise will be the takeover of the domain controller, which is a server that controls the network and the Active Directory services. From there, the attacker will gain domain admin rights, so more exploitation possibilities open up.
0-Domain Admin in 10 seconds with Zerologon (CVE-2020-1472)
Using @_dirkjan 's NetrServerPasswordSet2 commit to impacket 😀🥳 pic.twitter.com/PELfKJCQLV
— Rich Warren (@buffaloverflow) September 14, 2020
For such an attack to work, the hacker would first need to penetrate the corporate network, but we’ve recently covered this aspect discussing why it is a widespread security problem already. From there, the systems that could be hijacked are various Windows Server editions (2008, 2012, 2016, 2019), so this is not something that affects “regular” users who rely on Windows 10.
Microsoft had addressed this flaw back in August, and we had dedicated a paragraph on it due to its severe criticality. The patch plugged insecure RPC communications but didn’t enforce the new rules in order to allow system administrators some time to fix their devices or replace their equipment with one that supports secure RPC. From February 9, 2021, when the February 2021 Patch Tuesday is scheduled to land, the fix will be enforced. Even then, an administrator would be allowed to manually define exceptions for trusted devices.
If you’re wondering about whether your system is vulnerable to the “ZeroLogon” exploit, there’s a Python testing script that you may find on GitHub, and which attempts to perform the Netlogon authentication bypass. If it works against your system, it will terminate immediately without performing any malicious operations, and this will signify that you are missing the first stage of the patch. The authors of this testing tool warn about a false negative chance of 0.04%, so beware.