PROMETHIUM Expands Threat Reach via “StrongPity3”
- PROMETHIUM is expanding its targeting to more countries while deploying new malware as well.
- The actors are using trojanized apps as decoys to plant their payloads, and have updated their C2 infrastructure.
- The goal is to scan the infected systems for documents and exfiltrate them regularly.
Cisco Talos researchers are reporting about the latest signs of activity deriving from the PROMETHIUM group. It looks like the actors are expanding their victimology to even more countries from around the world. PROMETHIUM has been exposed multiple times in the last four years, but they are not the kind of hackers that will be deterred just because white-hat teams are after them. They are now deploying the next generation of the “StrongPity” malware, have set up at least four new “trap” files to act as trojans and use 30 new C2 domains.
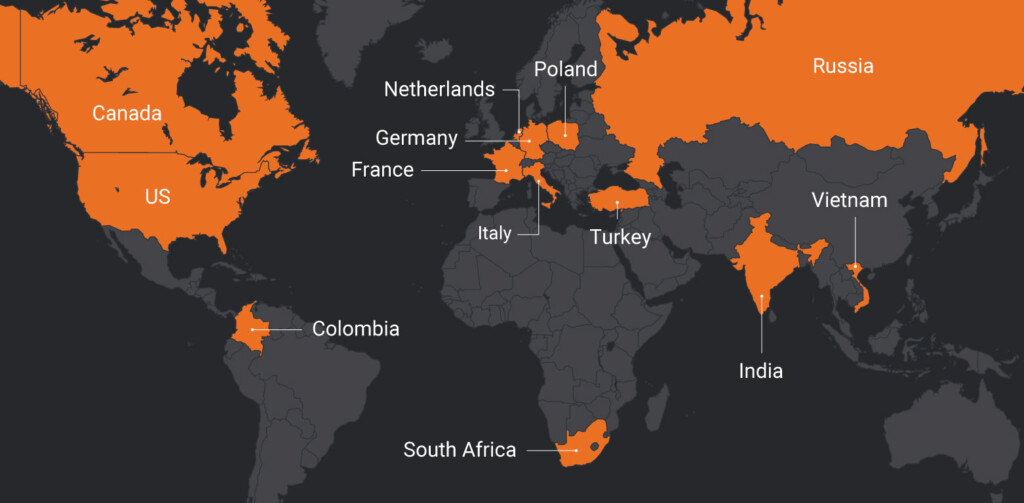
PROMETHIUM is a group that engages in espionage operations, and the StrongPity3 is a tool that can exfiltrate MS Office documents from the target system. The target countries are shown below, with India, Canada, Vietnam, and Colombia being targeted for the first time. The faux apps include a package that contains the Firefox installer, a “VPNpro” executable, a driver collection called “DriverPack,” and the “5kPlayer” media player. It is essential to point out that these apps will be installed on the system, but a trojan is also planted through a background process. In many cases, the trojanized setup will even reconfigure Windows Defender on the fly, to prevent detection.
Source: Cisco Talos
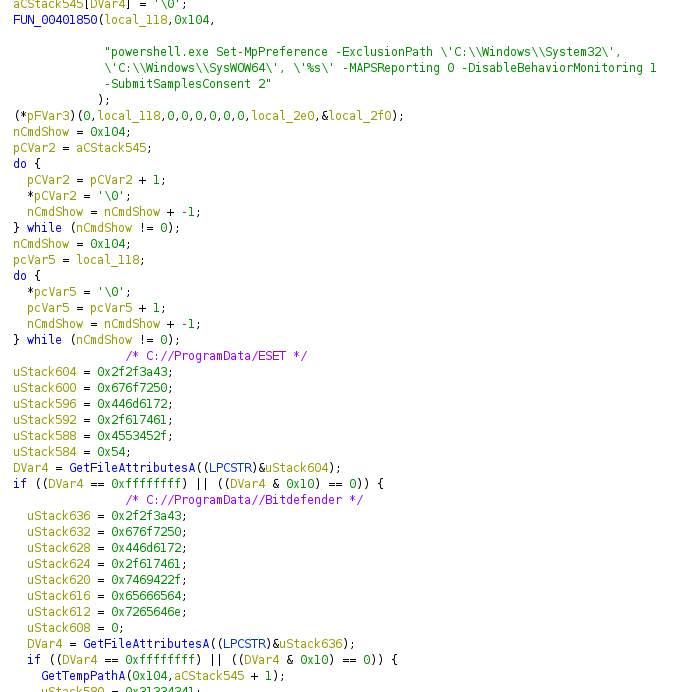
StrongPity3 is not a major upgrade compared to the second version of the malware, but it is an evolved piece of software nonetheless. For example, the use of libcurl to communicate with the C2 has been ditched in favor of winhttp. Moreover, the latest version has a new persistence mechanism that is based on the launching of a startup service, whereas previous versions were planting registry keys. Finally, the dropped files are now stored in a temporary folder buried deep in the user’s documents directory.
Source: Cisco Talos
The malware is initiating document scans on the system between intervals of 6,500 milliseconds of delay. The authors have done some work to hide the console window from the user, while the malware is also capable of ignoring files that have been located during previous scans. If the file to be exfiltrated is larger than 106KB, it is split into chunks and renamed by the tool automatically.
Cisco researchers believe that there’s a very good change the threat actor is part of an “enterprise service for hire” operation, as the malware samples retrieved from victims that were qualitatively different were all pretty much the same piece of software. To stay safe against this threat, deploy email security, malware protection, and network security solutions to protect the perimeter.