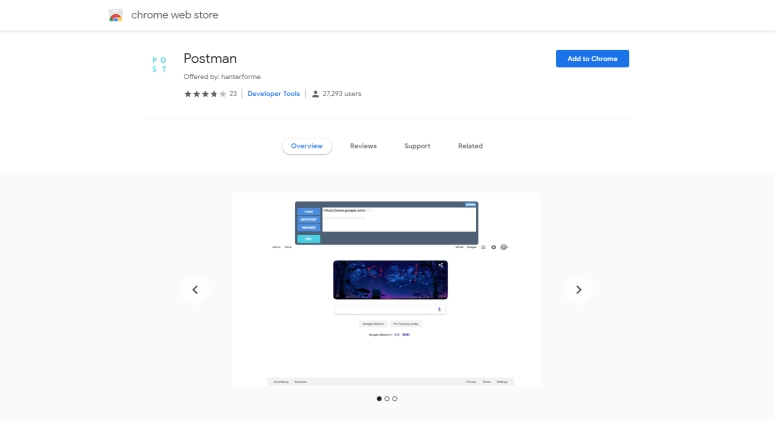
Postman Chrome Extension Stealing Crucial Browsing Data from Users
- Post extension found to be stealing browsing data by ExtraHop
- The type of data causes great concern to the IT analytics company
- Postman extension remains available for download in the Chrome store
Having Chrome extensions collecting browsing data from their users is not something new, as many are based on this practice to monetize installs and strengthen their analytics. When it comes to extensions that have a small user base though, you’ll have to go a step further than that in order to make a profit.
That’s what Postman developers may have thought apparently, as according to a public report made by the ExtraHop IT analytics firm, Postman is collecting critical browsing data that can be used maliciously against their users. This was almost accidentally discovered by ExtraHop when their “Reveal” threat detection tool indicated the existence of a persistent HTTP WebSocket connection to an external IP address on a suspicious port. Ironically, it was one of their employees who has been using Postman, not realizing the stealing of flow records. ExtraHop went to the trouble of doing reverse engineering and de-obfuscation to discover precisely how Postman works.
As Postman is a tool aimed to the web development sector, the people who use it are people who access information and databases that are quite possibly filled to the brim with undisclosed product information, API technical infrastructure, hidden features, intranet credentials, etc. That said, what Postman collects is not some YouTube viewing history that can be used for targeted marketing, but corporate secrets that can be sold to competitors for hefty amounts. In addition to this, Postman can also identify potential security gaps in a company’s network and allow others (or themselves) to orchestrate a targeted and effective cyber attack.
It is important to clarify that there’s another Postman Chrome extension that is also a web development tool, and in fact, it is much more popular than the stealing one. Considering the dates of the addition of the malicious Postman to the Chrome store, it is a copy of the original one that is named identically in an attempt to hook more web developers. Although over a month has passed since ExtraHop (and possibly others as well) has reported the “bad” Postman, Google is still keeping it in their store.
Do you trust browser extensions and are you using a packet sniffer to monitor their activity? Let us know in the comment section below, and don’t forget to hop to our socials on Facebook and Twitter to going discussions there as well.