New ‘Port Shadow’ VPN Flaw Allows Hackers to Spy and Redirect User Traffic
- Researchers have discovered a new flaw that allows attackers to intercept VPN data, inject malicious DNS packets, and cause denial of service.
- This vulnerability is present in OpenVPN, WireGuard, and OpenConnect protocols.
- High-end VPNs, such as NordVPN, Surfshark, and ExpressVPN, are immune to this vulnerability as they use more sophisticated server configurations.
A team of researchers led by Benjamin Mixon-Baca has discovered a new flaw in several VPN protocols that could allow malicious actors to compromise VPN services. Called “port shadow,” this vulnerability allows third parties to act as a network router, representing a new threat model affecting VPN users.
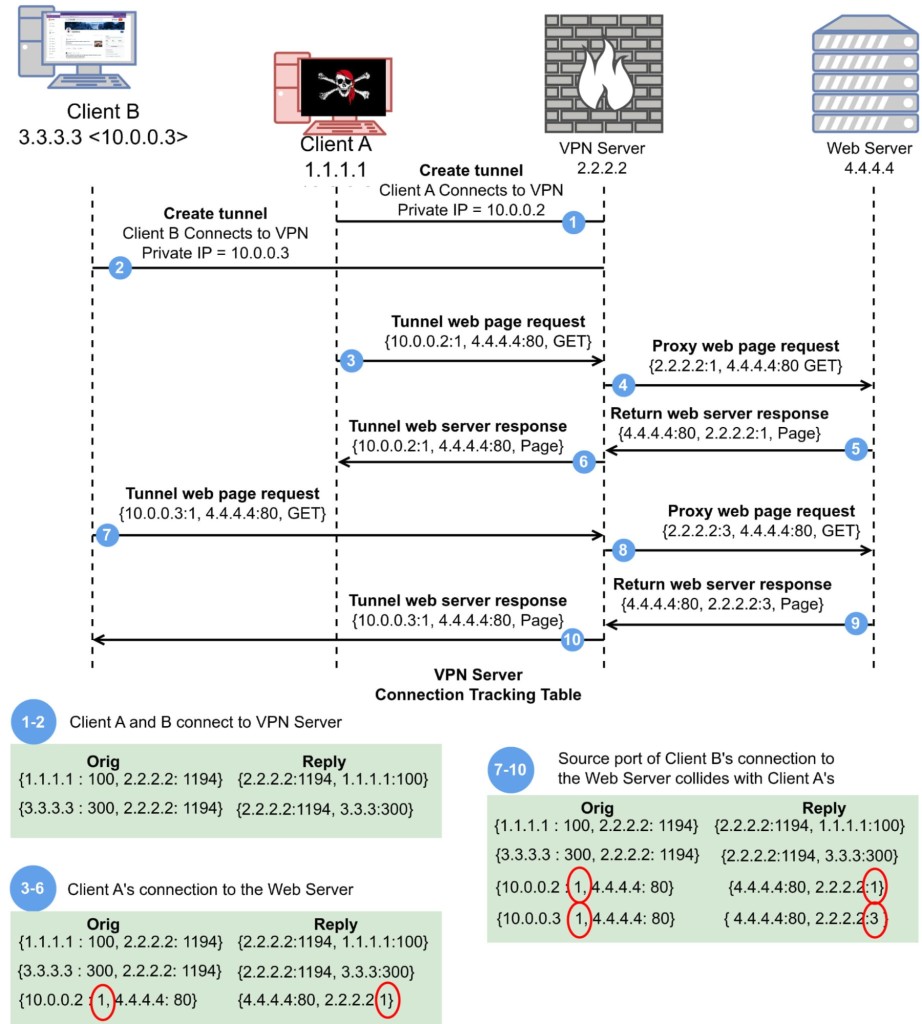
More precisely, the port shadow vulnerability is possible in a specific scenario only. When a user connects to a VPN server, they share a public IP address and ports with other users, which creates a possible exploit. A hacker could take advantage of this situation only by knowing the target’s public IP address and the VPN server’s IP address and only if the VPN server’s entry and exit IP addresses are the same.
As a result, malicious actors can use the port shadow to intercept and reroute a victim’s packets, inject DNS packets into the target, deanonymize connections, cause denial-of-service (DoS), and port-scan the target through the VPN server.
The above-said applies to VPN servers that use OpenVPN, WireGuard, and OpenConnect on Linux and FreeBSD systems, which are used by a significant fraction of commercial VPN services. Linux is more vulnerable than FreeBSD, regardless of client platform (PC, Mac, Android, or iOS).
The good news is that most of the top-rated VPN services are immune to these attacks. For example, NordVPN, Surfshark, and ExpressVPN already use server configurations that don’t match their servers' entry and exit IP addresses. Since ports and IPs don't collide, malicious actors cannot exploit the port shadow flaw.
As noted by PCMag, ExpressVPN’s representatives have said: “Our VPN servers use different entry and exit IP addresses, preventing the key conditions necessary for the attack described in the report. This is industry best practice—it enhances user privacy by preventing websites or ISPs from tying activity to specific individuals.”
In addition, NordVPN said: “We appreciate the work authors do to make an industry safer. However, we believe that generalizations are undermining the trust of VPN industry, especially meaning that not all services are affected by the vulnerability as noted in the paper.”
When it comes to end users, there’s not much they can do, as the port shadow flaw is found on the server and not the client app. If you use a less popular VPN provider, you should contact them to ask whether their software is safe against CVE-2021-3773, which is how this vulnerability has been officially categorized.