Popular Voice Assistant Companion Apps Are a Hazard for User Privacy
- The ecosystem of voice assistants is so stretched and intrusive, user privacy hangs on a thin thread.
- Researchers found a multitude of revealing sensitive user information stored on local devices.
- Companion apps on Android are another point of concern, as they ask the user to grant requests for several dangerous permissions.
Multiple privacy concerns arise from the use of voice assistants in smart devices, ranging from shady “accidental activations” to recording conversations and sending them to human reviewers for analysis. A team of Greek scientists has decided to dive deeper into discovering what sensitive data could be hiding in the ecosystems of three popular voice assistants, Amazon’s Alexa, Google’s Assistant, and Microsoft’s Cortana. According to their detailed report, there are numerous reasons to be wary if you’re using one.
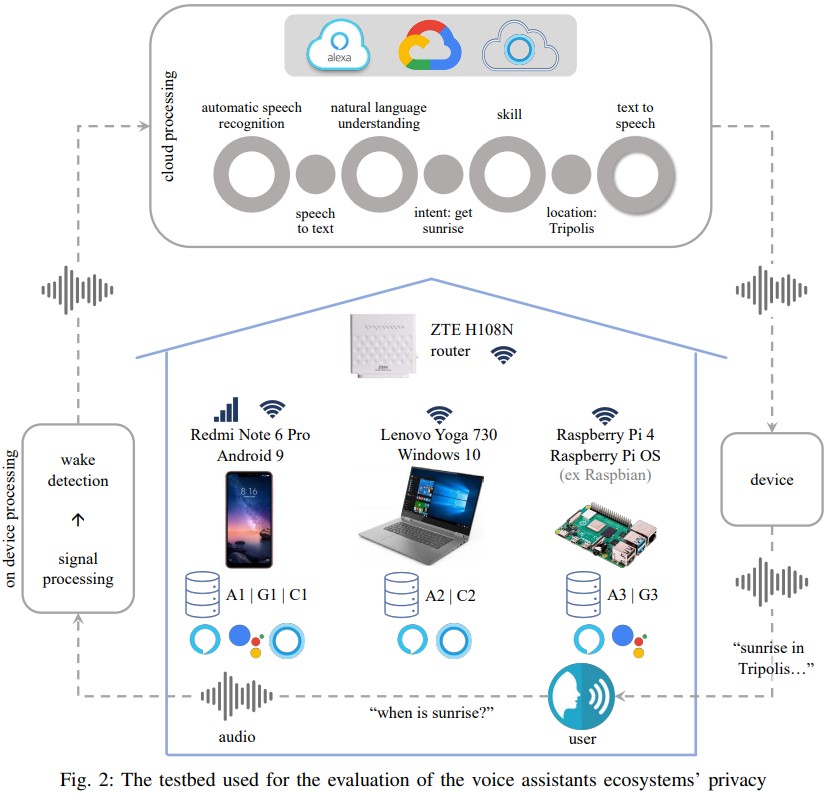
The team set up their testbed that is outlined in the diagram below, trying to figure out what data is received from the user, where it’s stored, how well it’s protected against unauthorized access, and what else can be deduced from it about the user. The accounts were created on the corresponding web interfaces.
Then, the team used a smartphone, laptop, and a Raspberry Pi to interact with the voice assistants so as to get a complete idea of what happens across the ecosystem. The commands used covered everything from listening to music to adding items on the calendar and from opening private images stored locally on the device to creating to-do lists.
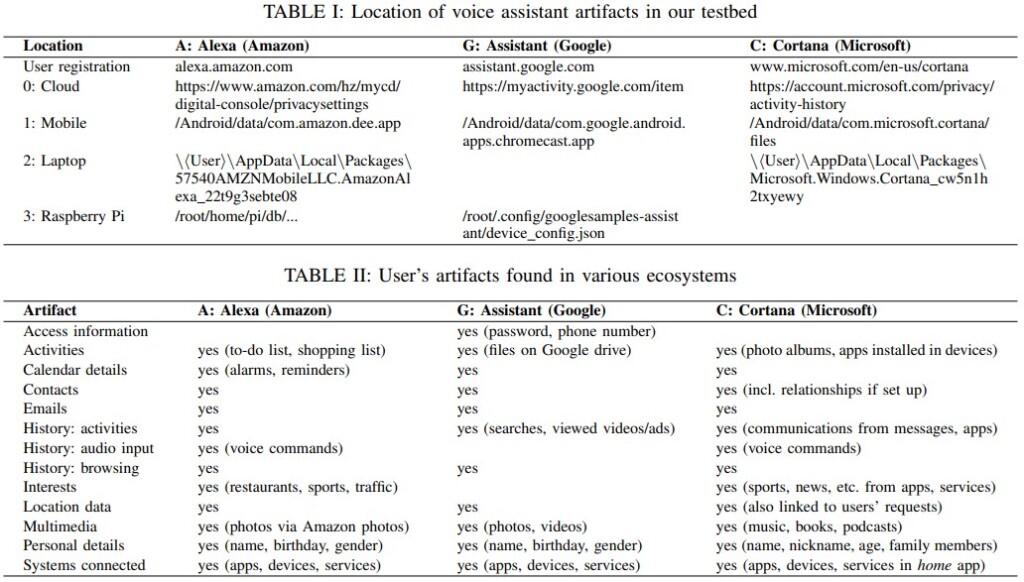
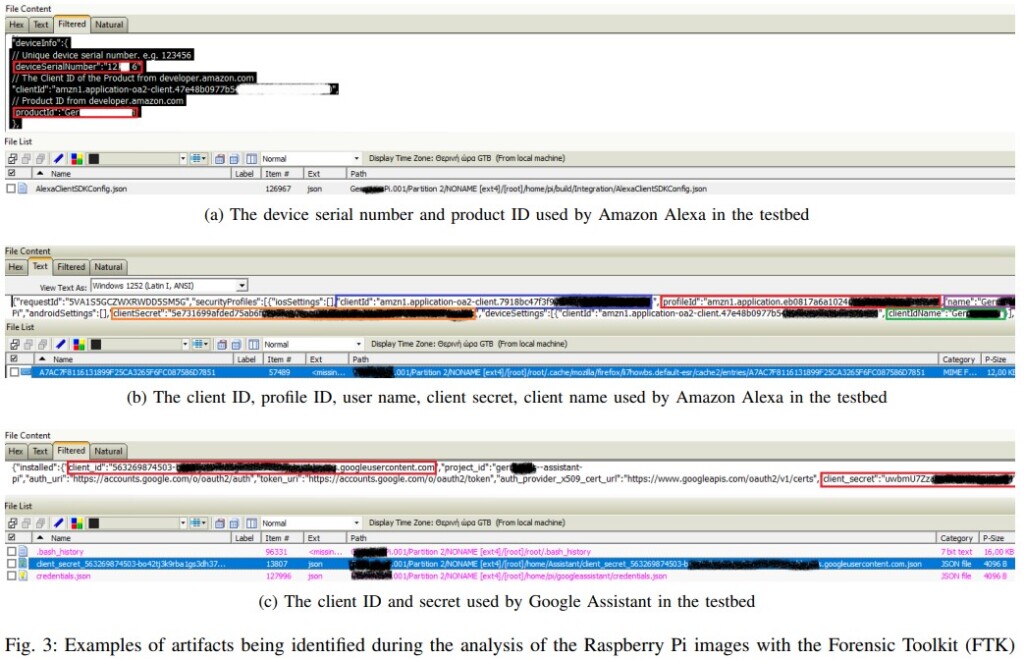
After the testing was over, the scientists looked into the devices and attempted to locate and retrieve data through the APIs, assuming that access to the user account is open and there’s physical access to an active device. The set of user artifacts maintained on the voice assistant platforms is quite rich, including profile IDs, account secrets, search histories, voice command logs, location, email address, etc. Among the three, Alexa was maybe the one that held the most limited amount of user-exposing information.
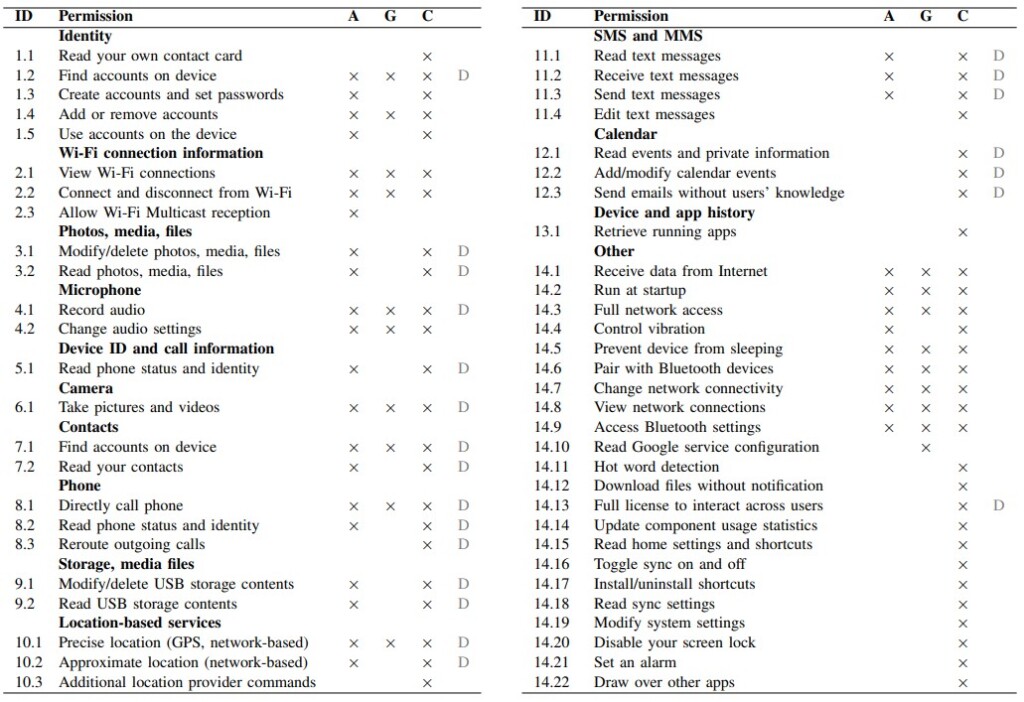
On Android, where the assistants have dedicated companion apps, the situation is far worse. These apps ask permission to find accounts on the device, record audio, take pictures and video, make calls, get the precise location (GPS + network), read and send SMS, read and modify USB contents, and more. The potential for abuse by exploiting a zero-day on these apps is dire, and these apps would make excellent targets for sophisticated adversaries and spyware companies.
In the case of Google, where the number of permissions requested is noticeably smaller compared to the other two, the researchers believe it’s just a case of having a dominant presence on the Android OS through various other Google apps, so the Assistant just doesn’t need to request for as many permissions because it can get what it needs from other components.