PlushDaemon Exploits South Korean VPN IPany
- Researchers found a new APT group that was exploiting a South Korean VPN provider, IPany
- The exploitation allowed cyber espionage, recording audio and data collection among others.
- The malicious activities were conducted in 2023 and were detected in an installer for Windows in 2024.
A new China-aligned APT group, PlushDaemon has been found to have exploited South Korean VPN company IPany. The attack took place in 2023 however the group remained undiscovered until a recent report published by ESET.
Researchers detected malicious activities in an NSIS installer for Windows in 2024. The hackers replaced the legitimate installer on Windows with a malicious one named SlowStepper. The backdoor contained a toolkit of over 30 components and was programmed in C++, Python and Go language.
In the recently detected supply chain attack against IPany, PlushDaemon managed to deploy both the legitimate software and the malicious backdoor.
The installer was removed by the South Korean company when they were notified about the findings.
Although there was no malicious code on the page, the victim downloaded a malicious ZIP archive with the NSIS installer. The URL detected was, “https://ipany[.]kr/download/IPanyVPNsetup.zip.”
Based on the recorded incident, it was concluded that several IPany VPN users might have fallen victim to the scam aimed to conduct cyber espionage. Several users installed the infected software with the first few users traced to Japan in November 2023 and China in December, however, the latter could be a test target.
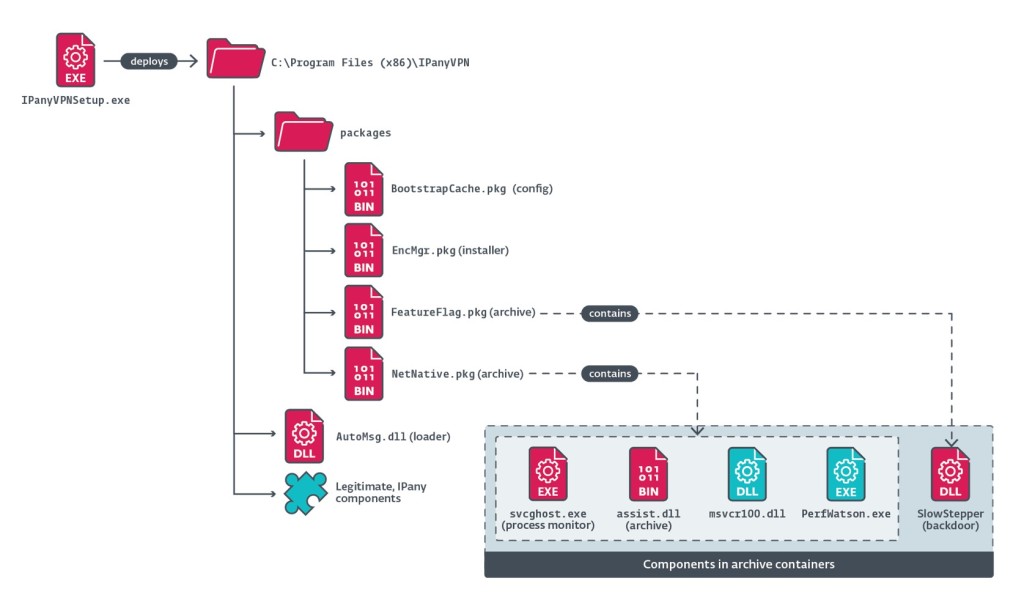
A detailed analysis of the malicious IPanyVPNsetup.exe file showed the following results:
- It created several directories.
- It maintained persistence by including the entry named IPanyVPN to a Run key, with %PUBLIC%\Documents\WPSDocuments\WPSManager\svcghost.exe value.
- The above step enabled the component svcghost.exe to launch at each start up.
- The first loaded malicious component would be installed in the AutoMsg.dll loader.
During the exit process of the IPany VPN, the patched bytes would redirect to the shellcode loading EncMgr.pkg in the memory. Following this it would create two directories namely WPSDocuments and WPSManager that would not create any suspicion among users.
It would go under %PUBLIC%Documents where the components would be extracted from the custom archives NetNative.pkg and FeatureFlag.pkg.
SlowStepper had two versions – full and lite; both capable of spying, recording audio and video and stealing data. The oldest version of the SlowStepper backdoor, 0.17 was compiled in 2019, based on the PE timestamp.
And the newest version, 0.2.12 was developed in 2024. Detailing on the findings of the tool, the report added, “The tools were stored in a remote code repository hosted on the Chinese platform GitCode, under the LetMeGo22 account; at the time of writing, the profile was private.“
It did not carry a command and control IP address and instead crafted a DNS query for the domain 7051.gsm.360safe[.]company.
PlushDaemon, active since 2019 has been known for cyber espionage against entities in the United States, New Zealand, and South Korea. Oddly enough, the group has also targeted China. The cybercriminal group gains access to systems by exploiting vulnerabilities, and updates.