Pidgin Messenger’s Official Plugin Used for Deploying DarkGate Malware
- Pidgin Messenger removed its official third-party plugin, ScreenShareOTR, due to the dissemination of malware.
- Users reported the malicious plugin installed keyloggers and infostealers.
- Security researchers’ analysis revealed it actually spread the powerful DarkGate malware.
Popular open-source instant messaging app Pidgin removed the ScreenShareOTR plugin from its official third-party plugin list, which was promoted as a screen-sharing tool for secure Off-The-Record (OTR) protocol for Windows and Linux clients and led to DarkGate malware, according to ESET Security.
Among the multi-protocol messaging app’s over 200 add-ons was the malicious ScreenShareOTR, which also installed various malware.
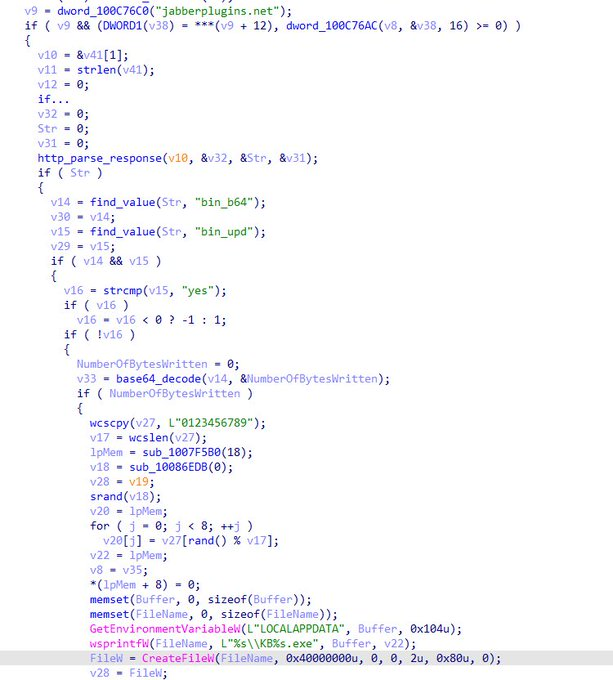
The plugin bundles malicious code with the advertised functionality of screen sharing, which can download and execute a PowerShell script from an attacker-controlled command and control (C2) server.
The installation files have a valid digital certificate issued to a Polish company, which also signs the downloaded payload – the DarkGate malware.
The attackers’ “jabberplugins” website is not currently operational, but it contained a fake plugin repository that included OMEMO, Pidgin Paranoia, Master Password, Window Merge, and HTTP File Upload.
According to Pidgin, only OSI-approved open-source license third-party plugins will be accepted in the future.
DarkGate malware uses advanced evasion techniques, like code obfuscation, encryption, and anti-debugging measures, and it can execute multiple payloads, including data exfiltration, cryptocurrency mining, crypto stealing, ransomware, keylogging, credential theft, and remote access.
The most recent DarkGate malware campaign targets Windows machines supported by a reactive C2 system and has evolved into a malware-as-a-service (MaaS), spreading via malicious torrent files, social engineering, phishing emails, compromised websites, and DLL sideloading.
Security researchers have recently observed a surge in the use of the DarkGate malware, which was seen in north of 14,000 malicious campaigns after the FBI disrupted the rival QBot (aka Qakbot) malware in August 2023.