Phone Hacking Tool Maker ‘Cellebrite’ Hacked by Signal’s Creator
- Signal’s CEO stumbled upon a Cellebrite machine, fiddled with it, and cracked it.
- The smartphone data extractor is apparently vulnerable to arbitrary code execution.
- One could make it generate false reports, exfiltrate store data, or change the results of previous reports.
‘Cellebrite’ is an Israeli digital forensics firm that develops phone hacking tools like UFED, which can unlock devices that are particularly hard to break, like the iPhone or the Samsung Galaxy, and law enforcement investigators extract valuable data from these devices. In December 2020, the company announced its ability to break Signal, the private e2ee communications IM tool used by many people who have reasons to protect their privacy, like journalists, activists, and political opponents to authoritarian regimes.
Signal wasn’t happy with its inclusion onto Cellebrite’s supported software list and dug deeper into the technical aspect of the feat to figure out how they can continue protecting their users. In the process, Signal’s creator and CEO, Moxie Marlinspike, has found a way to execute arbitrary code on a Cellebrite machine simply by including a specially formatted but seemingly innocuous file in any app on a device that’s to be scanned by the specialized data extracting solution.
The relevant blog post that gives all the technical details also includes a sample video that demonstrates the hack and generates a mocking message. Obviously, the actual potential of the exploit goes well beyond just a message popping up on the user’s screen, like even altering saved reports, compromise the integrity of future reports, or even exfiltrate what data may be stored in the Cellebrite machine.
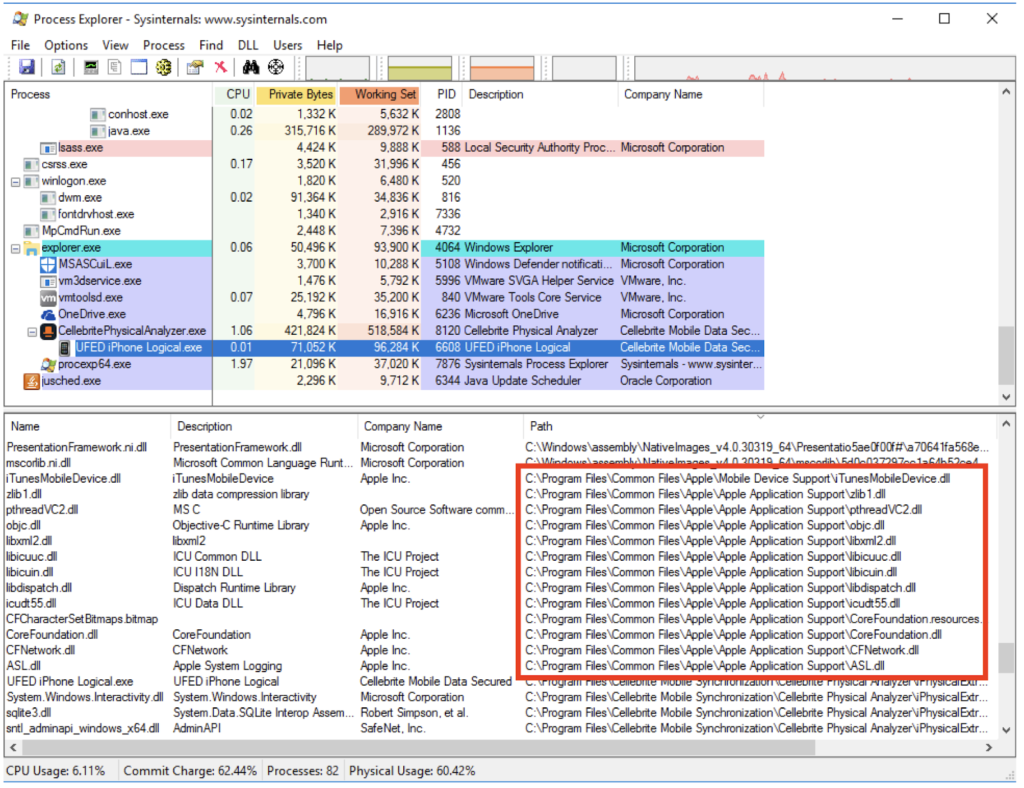
The post burns Cellebrite even more by presenting several cases of copyright infringement that could put them and their customers in trouble, like the presence of Apple DLLs that are being illegally redistributed with every machine. Also, there seems to be no doubt about their origin, as the Physical Analyzer of the tool contains two MSI packages that are digitally signed by Apple and appear to have been extracted from an iTunes installer for Windows.
And as for how Marlinspike got his hands on a Cellebrite machine in the first place, he claims he just stumbled upon one that fell off a truck ahead of him while he was out for a walk, calling it “a truly unbelievable coincidence.” We can’t help but think this is just something to protect a procuring insider and/or to make it more legally complicated to go after Signal’s CEO.
Maybe the most important element of this report is the fact that there’s a stealthy way to trick the software used by the police and various data forensic experts who work for law enforcement authorities, leading to the unjust incrimination of innocent individuals or the other way around. These agencies should have ways to verify the validity of the reports they’re getting from UFED or any other third-party tool of this kind, but it’s improbable they are doing that.