Fake ‘Google Safety Centre’ Phishing Scam Deploys Malware Disguised as Google Authenticator
- A new malicious site pretends to offer the legitimate Google Authenticator app.
- The phishing site downloads and installs two kinds of malware on the victims’ machines.
- One maintains persistence on the infected devices, and the other is an infostealer.
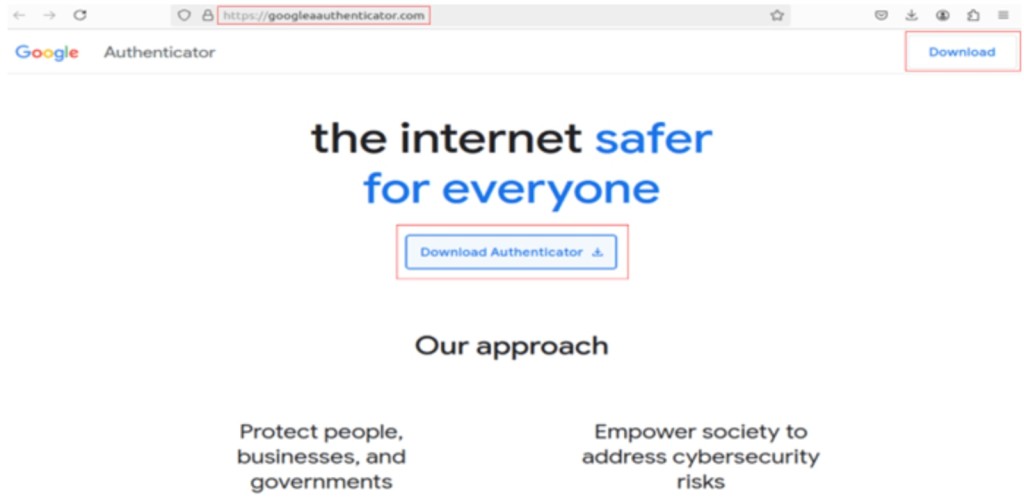
A phishing site masquerading as an official ‘Google Safety Centre’ page deploys malware like Latrodectus and ACR Stealer while pretending to let users download the trusted multi-factor authentication (MFA) app Google Authenticator, a report from Cyble Research and Intelligence Lab (CRIL) says.
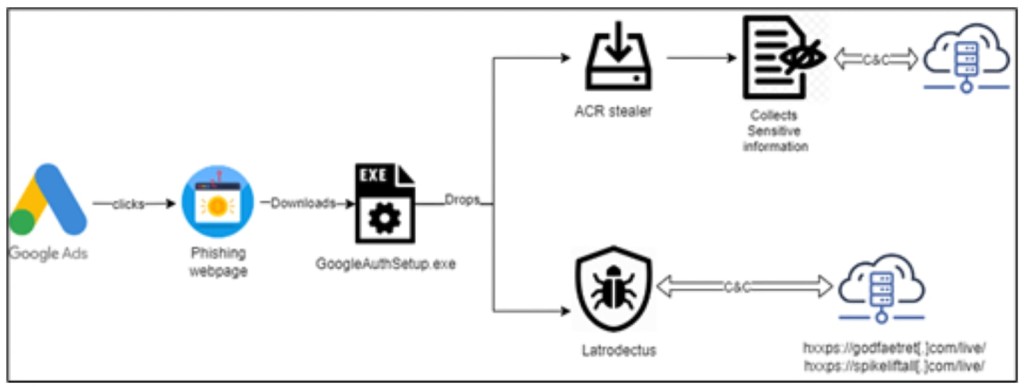
A loader with a valid digital signature, “GoogleAuthSetup.exe,” is downloaded instead of the legitimate Authenticator app. Once the user runs the executable, it pretends the installation was unsuccessful while covertly downloading and executing ACR Stealer and Latrodectus.
ACR Stealer obscures its Command and Control (C2) server details via Dead Drop Resolver (DDR) to evade detection, embedding this information within seemingly safe locations or platforms. In this case, the infostealer hides the C2 details on the Steam Community website.
The malware targets Web browsers, email and FTP clients, crypto wallets, messaging apps, VPNs like AzireVPN and NordVPN, and password managers, as well as MySQL Workbench, AnyDesk, snowflake-ssh, Sticky Notes, and more.
Latrodectus was made by the creators of IcedID and is actively developed, showing updates to its encryption key pattern and new commands.
This month, a fake advertisement for Authenticator that seemed to come from official sources appeared among Google search results, and the advertiser’s identity was even verified by Google. The ad led to a decoy website leading to a signed payload hosted on GitHub, where people actually downloaded the DeerStealer malware.