Phishing Campaigns and SEO-Poisoned Trojanized VPN Apps Distribute PLAYFULGHOST Malware
- Hackers deploy a novel malware strain via phishing emails and SEO poisoning for downloading compromised VPN installers.
- A malware-laced installer for LetsVPN drops a payload that retrieves backdoor components.
- PLAYFULGHOST leverages advanced techniques like DLL search order hijacking and side-loading and establishes persistence via multiple methods.
A new and sophisticated malware dubbed PLAYFULGHOST is equipped with an array of intrusive capabilities such as keylogging, screen and audio capture, remote shell access, and file manipulation.
PLAYFULGHOST is delivered through two primary vectors—phishing emails and SEO poisoning—to lure victims into downloading malware-laced versions of legitimate VPN apps like LetsVPN.
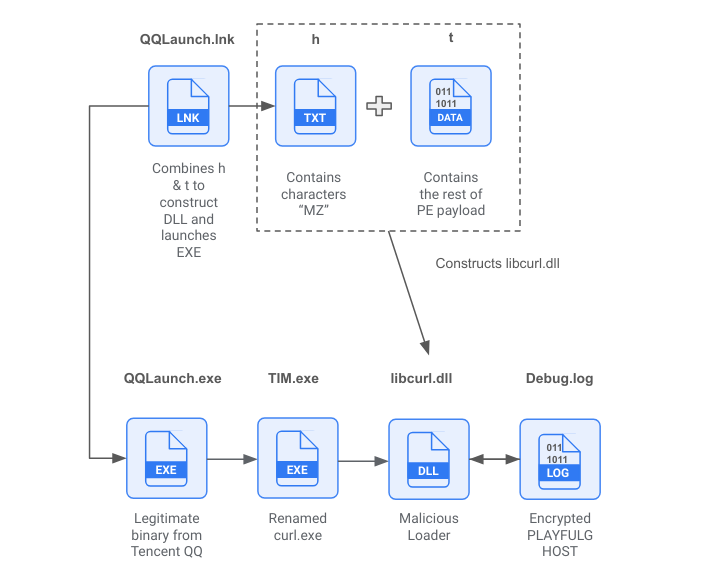
The SEO poisoning campaigns, meanwhile, aim to trick users into unknowingly downloading compromised LetsVPN installers. Once launched, these installers deploy an interim payload designed to retrieve the malware's backdoor components.
Google's Managed Defense team has identified significant overlaps between PLAYFULGHOST and Gh0st RAT, a legacy remote administration tool whose source code was leaked in 2008.
Sometimes, a RAR archive disguised as a JPG drops a malicious Windows executable that downloads PLAYFULGHOST from a remote server.
Furthermore, PLAYFULGHOST leverages advanced techniques like DLL search order hijacking and side-loading to load the malicious DLL files required to decrypt and execute the malware directly in memory.
The malware establishes persistence via multiple techniques, including modifications to the Windows Run registry key, scheduled tasks, the startup folder, and Windows services.
Once embedded, the malware can collect keystrokes, capture screen activity, record audio, and gather details such as QQ account information, clipboard content, installed security software, and system metadata.
It also has advanced destructive capabilities, such as injecting additional payload, disabling mouse and keyboard input, clearing Windows event logs, and deleting browser caches and profiles for applications like QQ, 360 Safety, and Google Chrome and local storage for messaging apps, including Skype and Telegram.
The deployment of complementary tools further enhances its functionality. These include Mimikatz, widely used for credential theft, and a rootkit capable of concealing registry entries, files, and processes. PLAYFULGHOST also deploys an open-source utility called Terminator to disable security processes using a Bring Your Own Vulnerable Driver (BYOVD) attack.
The focus on apps like Sogou, QQ, 360 Safety, and the reliance on LetsVPN strongly hint at targeting Windows users in Chinese-speaking regions.
Mimikatz is a tool commonly used to extract sensitive information, such as passwords and credentials. Recently, the returning hacktivist group Twelve used it, and it is also a favorite of the Scattered Spider ransomware group.