New Phishing Campaign Delivering the Quasar RAT via Email
- A new phishing campaign is distributing unsolicited job application messages that come with a malicious resume document.
- The document contains macros that eventually download the open-source Quasar remote access tool.
- The actors have incorporated quite a few techniques to strengthen the anti-analysis protection of their campaign.
As reported by Cofense Intelligence, there’s a new ongoing phishing campaign that tries to infect victims with the Quasar RAT (Remote Access Tool). Quasar is an open-source RAT that is widely used by malicious actors as it offers a rich set of capabilities and it’s freely available on public repositories. To avoid detection from AV tools, the phishing actors are locking down the document that they send as an attachment on the phishing email message, and which contains the malicious encoded macros. This creates a problem for organizations as the defense lies in the understanding and response of the recipient.
image source: https://cofense.com
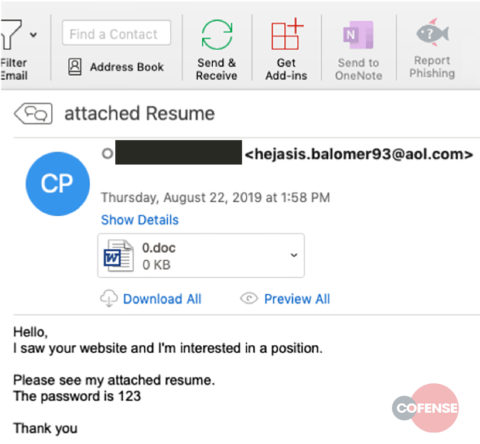
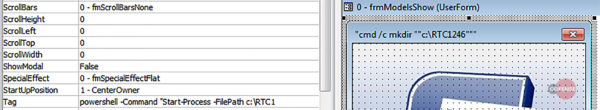
As Cofense researchers report, the email that is currently used by the phishing actors is supposedly an unsolicited job application, while the attachment serves as a resume. The password to open the file is given in the message body and the user is urged to activate macros by "enabling content" and "enabling editing". Besides the locking of the document file with a password, the actors are also employing a “garbage code” approach, adding 1200 lines of base64 encoded code to the script which essentially causes most analysis tools to crash after getting overwhelmed by the amount of decoding required. Even if a researcher finds a way around this, the payload URLs will still be missing, or be partially available. The remaining data that pertains to the payload URL is hidden as meta-data for embedded images and objects inside the document.
image source: https://cofense.com
The images are displayed as they are parsed when the macro is executed, which finally leads to the unpacking of the Quasar RAT binary. The significant size of 401MB isn’t easy to hide for the malicious actors, so they try to hide the relevant information from the user. In this particular campaign, the filenames that are used are “0.doc” for the document that contains the malicious macro code, and “Period1.exe” and “Uni.exe” for the executable files.
Because of the anti-analysis techniques that are incorporated into this campaign, protection against this threat relies on the response of the recipient. If you receive an unsolicited job application, treat it as any unsolicited email message and avoid downloading and executing any attachments that come with it. It doesn’t matter if the content of the message is a blatant sign of fraud or if it is seemingly benign. If you receive a message that you weren’t expecting, treat it with care. Finally, keep your office suite’s macros functionality disabled, and only open these documents on sandboxed environments.
Have you received a message from this or any other similar campaign? Can you share any details with us? Feel free to do so in the comments down below, or on our socials, on Facebook and Twitter.