Phishing Campaign Compromises Microsoft Azure Cloud Infrastructures of European Entities
- Threat actors targeted thousands of institutions and companies in Europe with a phishing campaign using geographic customization.
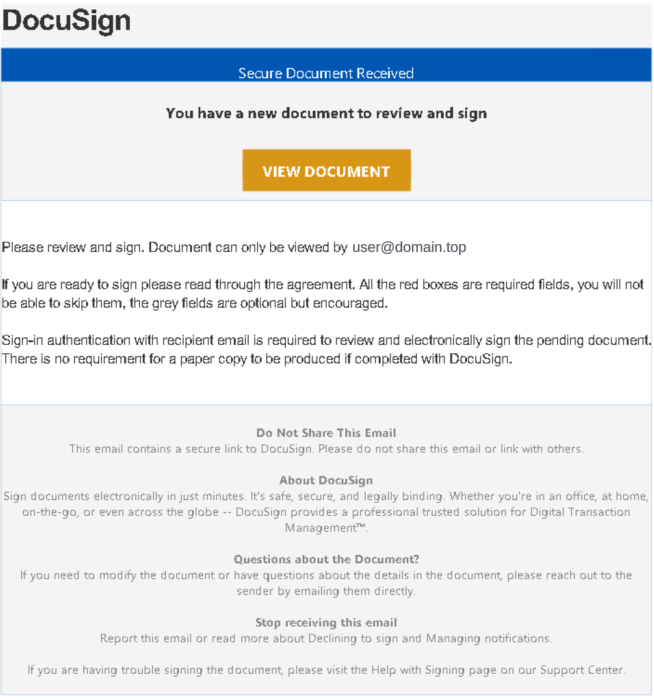
- Via DocuSign-enabled PDF files or embedded HTML links, they harvested credentials and compromised Microsoft Azure cloud infrastructures.
- The hackers gained persistent access via VPN proxies-enabled login spoofing and adding unauthorized devices to compromised accounts.
An active and sophisticated phishing campaign targeted over 20,000 users across European companies from automotive, chemical, and industrial compound manufacturing industries.
The threat actor, active since at least June 2024, utilizes advanced techniques to harvest user credentials, compromise Microsoft Azure cloud infrastructures, and conduct lateral movement operations, per the latest security report from Palo Alto Networks’ Unit 42 research team.
The campaign leveraged phishing emails with attached DocuSign-enabled PDF files or embedded HTML links. These led victims to fake forms created using HubSpot’s Free Form Builder service. These emails created a false sense of urgency and exploited user trust through thematic branding that mimicked targeted organizations.
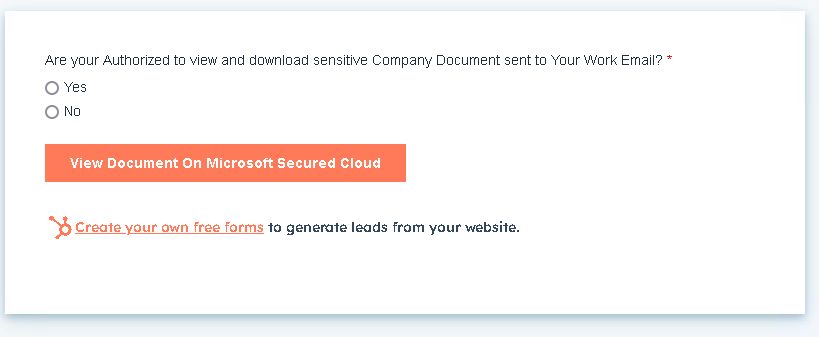
In one example, threat actors used organization-specific file names such as CompanyName.pdf and included phrasing like “View Document on Microsoft Secured Cloud” within the malicious forms.
Victims were directed to credential harvesting pages designed to steal Microsoft Azure login credentials. The attackers then added unauthorized devices to accounts for persistent access.
Evidence suggests the threat actor employed highly targeted phishing attempts, even tailoring content to match specific brand dialogue and email formatting. An example includes targeting notaries in France with phishing websites designed to exploit their workflows.
The campaign relied heavily on Bulletproof VPS hosting services, chosen for their ability to resist takedown efforts. Evidence from Unit 42’s analysis revealed 17 active Free Forms redirecting users to domains hosted on top-level domains such as .buzz, structured to resemble Microsoft Outlook Web App landing pages.
During account takeovers, the attackers used VPN proxies and bot-controlled devices to imitate trust signals, making login attempts appear from familiar geographical regions. The persistent addition of unauthorized devices allowed attackers to regain control, creating a continuous battle between them and the compromised organizations’ IT teams.
The researchers confirmed that neither HubSpot’s infrastructure nor its Free Form Builder service was compromised, though the latter was exploited to generate phishing links. Similarly, DocuSign has implemented additional preventative measures to reduce fraudulent signature request attempts significantly.
Last month, a novel phishing kit developed by a Chinese-speaking threat actor was used by at least 2,000 websites in the U.S., the U.K., Spain, and more for attacks that used RCS messages to simulate fake scenarios for harvesting sensitive data and Telegram to exfiltrate credentials, avoiding detection by leveraging Cloudflare's anti-bot and hosting obfuscation techniques.