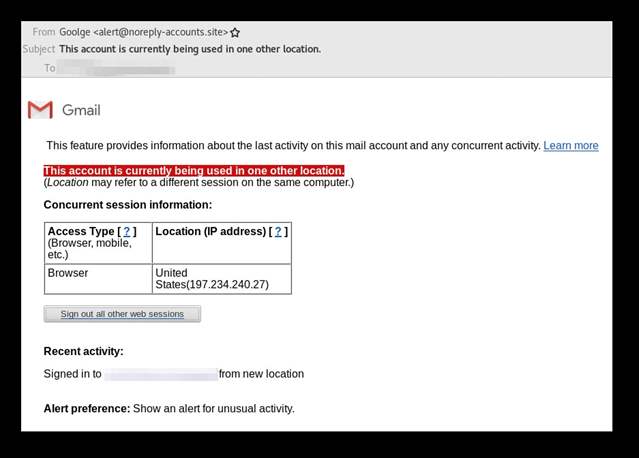
Phishing Attacks Target Google, Yahoo, and ProtonMail Accounts
- A new wave of phishing attacks has been discovered that can bypass two-factor authentication.
- A report by Amnesty International revealed that the attacks targeted towards accounts in North Africa and the Middle East.
- Google, Yahoo, and ProtonMail are three of the major companies whose users are being targeted.
According to a report by Amnesty International, a number of hackers have been able to come up with a new phishing attack that can bypass two-factor authentication. A number of companies are being targeted including Google, Yahoo, and ProtonMail with users having their accounts infiltrated. The attacks are successful against common 2FA methods like SMS protect and email-based two-factor authentication methods.
Image Courtesy of Amnesty International
Amnesty International has been monitoring the phishing attacks since 2017, and most of the identified victims are from the Middle East and North Africa. According to the report, the attacks are most likely based in UAE, Egypt, Palestine, and Yemen. Human rights defenders, political actors, journalists, and other potential victims are the interest to the attackers.
A Yahoo spokesperson responded to the attacks saying "The threat landscape is continually evolving, and we are committed to evolve with it to help keep our users secure. In 2015, we launched Yahoo Account Key, which does not utilize SMS, and encourage users to adopt this form of authentication."
Google’s phone-based authentication method that requires users to enter two different numbers that show up on their mobile devices along with U2F key authentication were not affected. Users who use traditional two-factor authentication methods like SMS or email should move towards app-based authentication or physical authentication keys for added security.
According to Amnesty International, the phishing attacks are completely automated, and the people behind the attacks trick users into resetting their passwords while having access to the two-factor authentication codes. Some of the attackers also created fake websites with slight changes to the URLs which is one of the oldest methods of phishing for passwords.
What do you think about the phishing attacks targeting internet users in North Africa and the Middle East? Let us know in the comments below. Don’t forget to join the discussion where our online community also likes to hang out, on Facebook and Twitter.