Phishing-as-a-Service Platform ’Morphing Meerkat’ Uses Advanced DNS MX Record Abuse
- A 5-year-long phishing operation uses DNS and phishing-as-a-service techniques to target email users globally.
- Advanced phishing tools target over 100 brands, including major email and financial services.
- The malicious content is based on the DNS MX records of victims’ email domains.
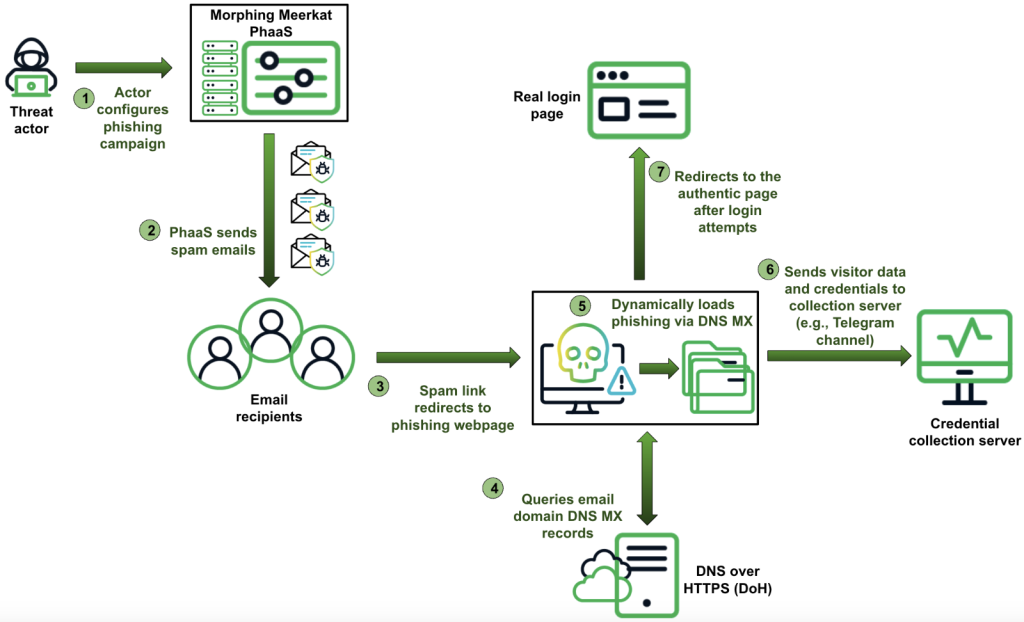
A stealthy phishing campaign, Morphing Meerkat, leverages DNS mail exchange (MX) records to dynamically generate tailored phishing pages, leveraging email spoofing and advanced obfuscation.
Threat actors are becoming increasingly innovative in their exploitation of DNS, particularly within phishing campaigns, recent research from Infoblox Threat Intelligence highlights. This phishing-as-a-service (PhaaS) operation has been active since at least 2020.
The Morphing Meerkat PhaaS platform provides a robust toolkit for cybercriminals, enabling them to deploy malicious pages that mimic over 100 brands, including major email and financial services.
The platform tailors its phishing content based on the DNS MX records of victims’ email domains, using Cloudflare DNS over HTTPS (DoH) or Google Public DNS to find the MX record of a domain.
Many email service providers configure DNS MX records with the same second-level domain (SLD) value for multiple email domains, enabling hackers to accurately determine the service provider of an email domain using its MX record SLD at scale.
It deploys phishing pages based on DNS MX records to align designs with victims' email providers, adapting to victims' browser language to cover over a dozen languages, including English, Russian, Chinese, and German.
It also sends a high volume of sophisticated phishing emails, using scare tactics to lure victims into clicking malicious links, and obfuscates code to evade detection by researchers and security systems while redirecting suspicious users to legitimate websites.
Early campaigns in 2020 targeted just five email brands, with content displayed solely in English. By 2023, the PhaaS platform had expanded to target 114 email brands and incorporated real-time language translation capabilities to broaden its global reach.
Its operations rely heavily on compromised WordPress websites and adtech open redirect vulnerabilities to distribute phishing URLs. By exploiting legitimate infrastructure like Google's DoubleClick advertising network, Morphing Meerkat is able to bypass security systems that trust these widely recognized domains.
The researchers identified thousands of spam emails originating from Morphing Meerkat. Interestingly, nearly half of these phishing emails were routed through servers owned by two prominent ISPs, iomart (UK) and HostPapa (US).
This centralized infrastructure strongly suggests the attacks are orchestrated by a single entity rather than disparate threat actors.