Phishing Actors Still Abusing ‘Google Translate’ to Evade Detection
- Phishing actors are still abusing Google Translate to steal people’s credentials without raising security flags.
- The tricking system works excellently, even though the actors didn’t bother to take care of all details.
- Google appears unable to close the loophole and internet security solution vendors don’t do much about it either.
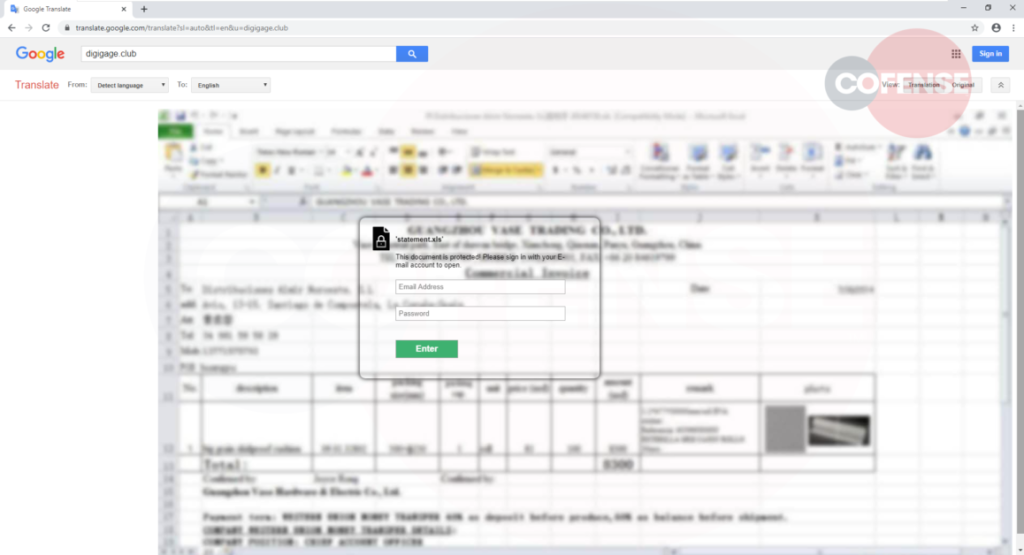
Phishing actors are back to abusing Google Translate to help them spread crimeware without being detected while also increasing the chances of tricking their targets with a “sprinkle of legitimacy.” The latest campaigns of this kind were spotted and recorded by Cofense, reporting that it all starts with an email arriving on the victim’s inbox. The message mentions a document that was allegedly shared with the recipient on Google Drive, claiming that the sender is someone using a seemingly legitimate website address.
However, the hyperlink embedded in the content instead takes the victim to a Google Translate link, which is actually an image made to spoof whatever email address was used for the sender. There, the victim sees a blurred-out MS Excel document in the background and is urged to enter their credentials to access the file.
None of this makes sense for those who are careful enough and look at the details, as MS 365 documents shouldn’t have a place in Google Drive’s viewer. Still, many would get tricked nonetheless due to the false sense of urgency.
Whatever account credentials are entered on the login prompt are sent to the website contains in the Google Translate URL, in this case, “digigage[.]club” (hxxps://translate.google[.]com/translate?hl=&sl=auto&tl=en&u=digigage[.]club). These URLs and IP addresses (142.250.217.78, 192.64.117.42) have already been reported and taken down, but nothing is stopping the actors from using a new one and returning to their malicious operations.
Cofense has even created an example of their own website and how someone could deliver a replica of it through Google Translate. What the user would see on the URL bar is a Google.com domain, so the deception possibility is great. Of course, the same goes for internet security tools that would never flag such a domain.
The first time we reported about cases of Google Translate abuse was back in February 2019, and yet it seems that phishing campaigns can still leverage Google’s online services. This is notable, and since Google appears unable to do something about it, it should be vendors of security tools who will take additional measures to detect and block threats of this type. Sure, scrutinizing everything that comes from all sources and using no whitelists whatsoever can make things cumbersome. Still, this practical dead-end is precisely what crooks have been exploiting all this time.