Phishing Actors Spoofing ‘WeTransfer’ to Steal ‘Office 365’ Credentials
- Actors are spoofing 'WeTransfer' notifications to lead recipients to an 'Office 365' phishing page.
- The page carries some subtle signs of fraud, but they're easy to go unnoticed for careless users.
- The campaign is still ongoing, using a known and previously reported IP address for the dissemination of the emails.
There's a new credentials phishing campaign going on out there, with the actors using a spoofed 'WeTransfer' notification to convince their targets to enter their 'Office 365' usernames and passwords on a phishing page. The discovery is the work of researchers at ArmoBlox, who have shared their report with TechNadu prior to its publication. The campaign is still ongoing, so users of 'Office 365' are advised to remain vigilant against incoming WeTransfer notices they weren't expecting.
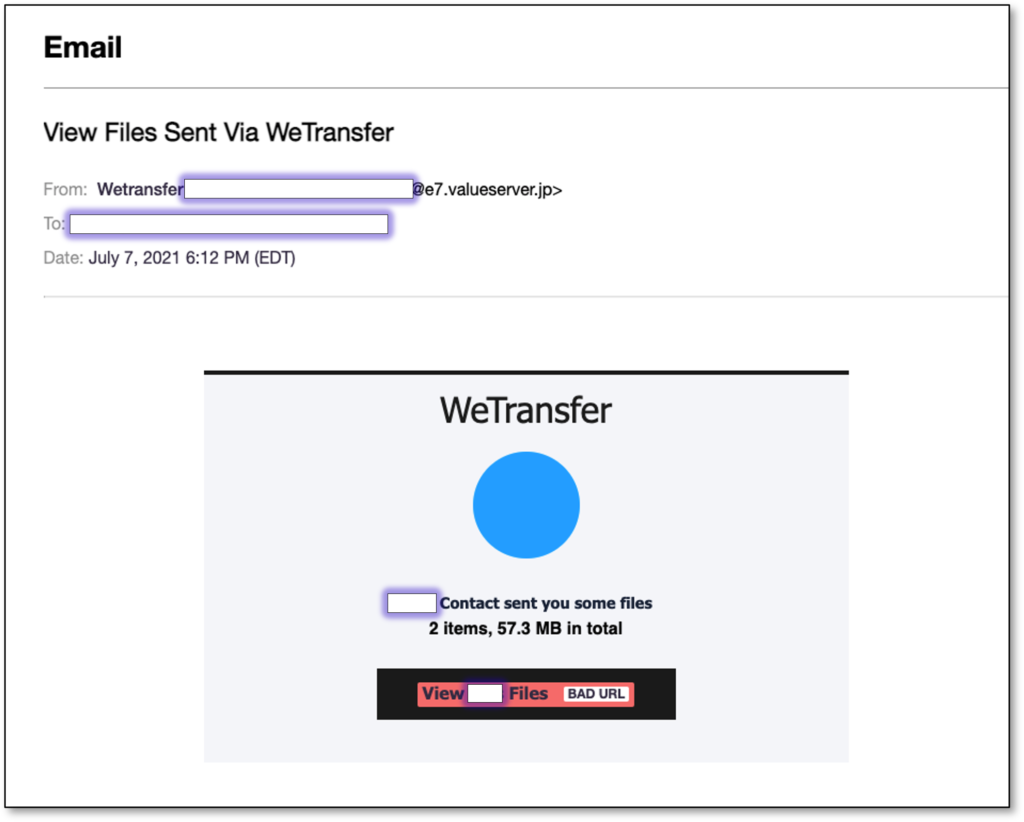
The attack begins with the reception of an email that claims to be a WeTransfer notice, informing the recipient of two files that were sent to them by a colleague. The email theming is similar to that of a genuine WeTransfer notice so that it would pass as a real one for most people. The email body also includes the recipient's real name to increase the sense of legitimacy.
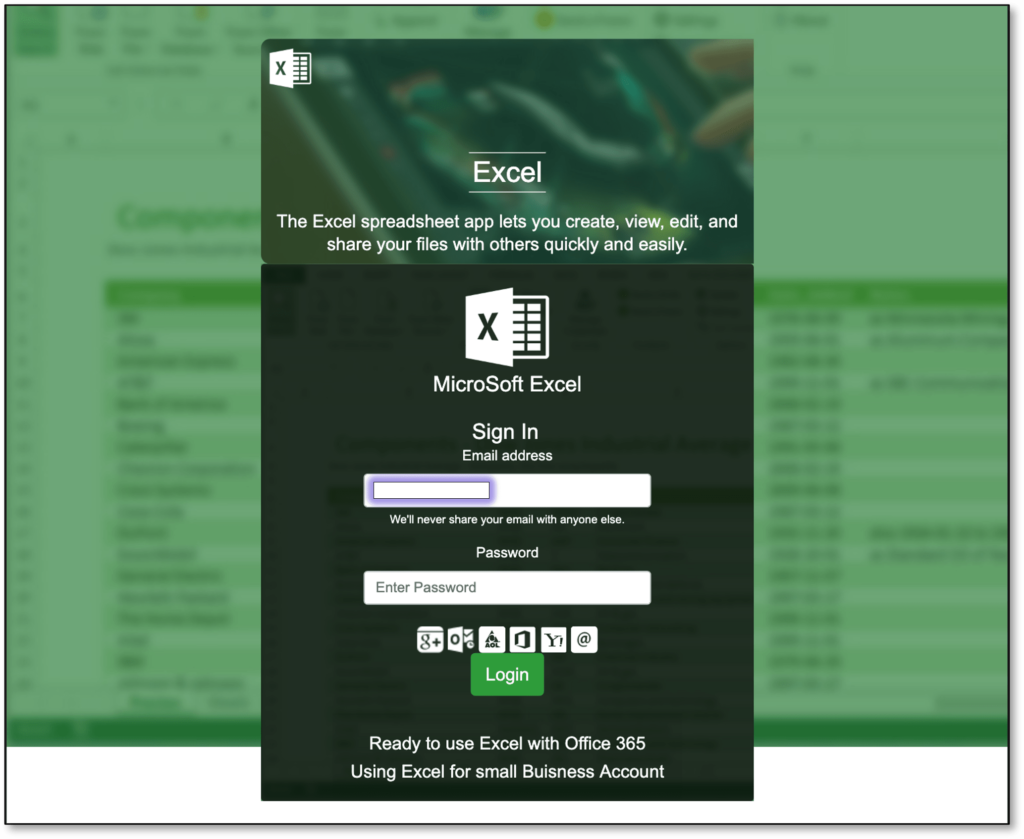
If the recipient clicks on the 'View Files' button embedded in the message, they will be taken straight to a phishing page that pretends to have some form of a relation to Microsoft Excel, so the victim thinks they've got two spreadsheet files through WeTransfer. To view the spreadsheet that is shown as blurred in the background, the victim is prompted to enter their 'Office 365' credentials.
For anyone who has used WeTransfer before, the above step would be an obvious giveaway of something being totally off. WeTransfer never asks for any credentials whatsoever, doesn't feature an online document viewer, and won't redirect you elsewhere depending on the type of file you've received through the service. Non-experienced users or those drowned in the sense of the fake urgency created by the actors may regularly enter their credentials on the phishing page to see what happens.
If you're an impulsive person who could get tricked by things that closely resemble their daily workflows, make sure to secure your Office 365 account by setting up a multi-factor authentication step. This way, even if you happen to give away from username and password to phishing actors, they still won't be able to access and take over your account.
In general, avoid using the same password on more than one account, always pick something unique and strong like a long passphrase, use a password manager to help you manage the various credentials you're juggling, and always treat incoming communications with composure. Take it slowly and look for the signs of fraud, as they're always there. Even in this case, the actors used the word "MicroSoft," a telltale sign of trickery on the phishing page.