Phishing Actors Are Now Engaging in Malicious Utilization of reCaptcha
- Phishing campaigns are now using the actual reCaptcha API to stop automated scanning tools.
- This makes the work of white-hat researchers harder and creates a confusing fake legitimacy setting for the victims.
- Internet users should stop treating reCaptcha as a sign of trustworthiness, as this is clearly no longer the case.
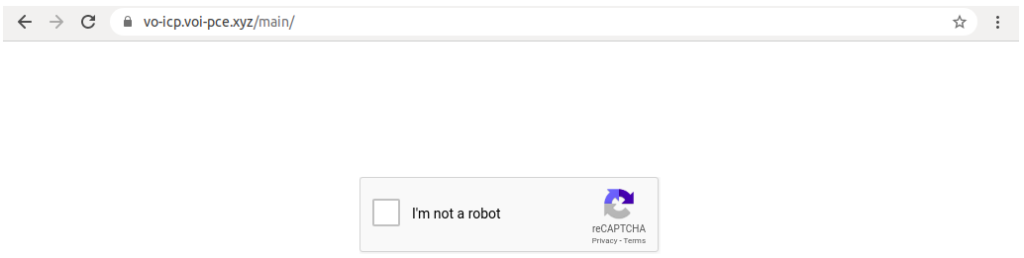
According to the latest reports from Barracuda researchers, phishing actors are now deploying "reCaptcha" to protect their platforms from detection and content analysis. This is a popular human verification system that is generally used to help websites stay clear from bot content scraping, so seeing it on malicious websites is something new. The reason for this move is that white-hat researchers are deploying scanning bots to spot phishing campaigns and report the domains to their respective registers. This is obviously causing trouble to the phishing actors, so they figured that a reCaptcha wall would help them keep automated analysis systems out.
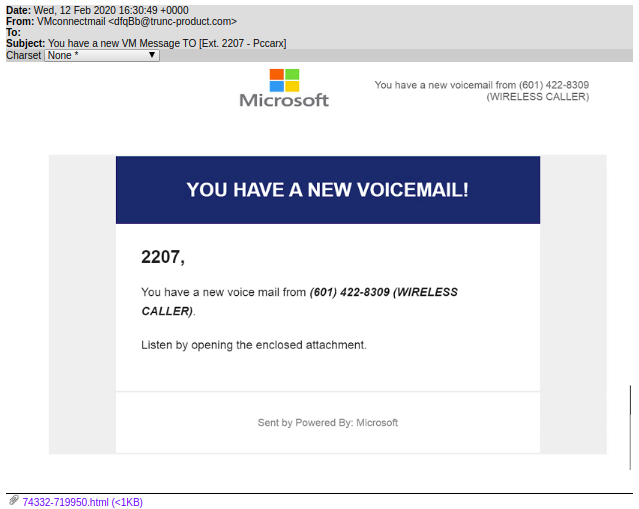
They are not spoofing the reCaptcha box, as we've seen before, but it is an actual deployment of the verification system's API. Barracuda reports that the phenomenon has gotten so extensive now that only one out of 100,000 phishing emails is spoofing reCaptcha, with all of the rest using the real API. One of the most recent examples given in the report is that of a phishing campaign using fake Microsoft login pages, informing the user that they have voicemail messages to review. It is also something that we have seen in the recent past, but this time, there's a reCaptcha wall in place.
Source: Barracuda
The HTML attachment is the re-direction point, and it is important to point out that the reCaptcha wall isn't serving only as a defense against researchers. When a victim follows an email link and gets a reCaptcha page, a false sense of legitimacy is created. People are used to seeing these walls on legitimate websites, so they are further convinced by the claims of the phishing actors.
Source: Barracuda
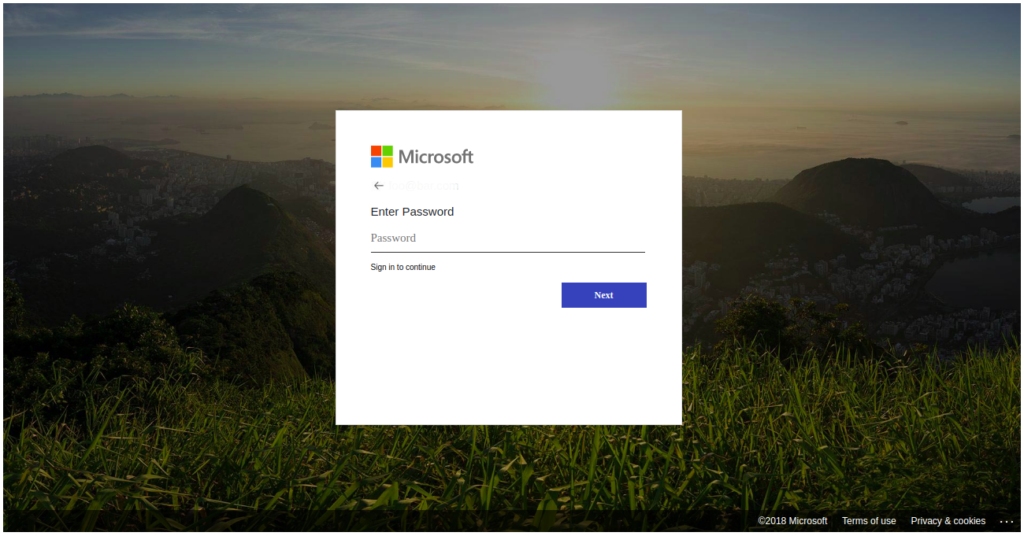
Of course, those who are convinced would end up giving away their Microsoft Account credentials to the phishing actors, and they would soon realize that there were no voicemail messages pending for review.
Source: Barracuda
This is to bring the current methods of trickery to your attention and to convince you to be careful, even when you are face to face with a reCaptcha wall, as it means absolutely nothing in terms of safety and legitimacy. And as for the detection, Barracuda confirms that the addition of the human validation step is making it harder for researchers to spot malicious websites. However, most email protection solutions should still be able to identify the phishing attempt, no matter the "cheap" tricks that come next.