PayPal Confirms that User Authentication Tokens have Leaked
- Users of PayPal could have had their accounts taken over by malicious actors on specially crafted websites.
- The method of attack involves a series of deliberate erroneous authentication attempts and the stealing of user tokens.
- PayPal blundered by leaving the user’s credentials in plaintext form in the browser’s cache.
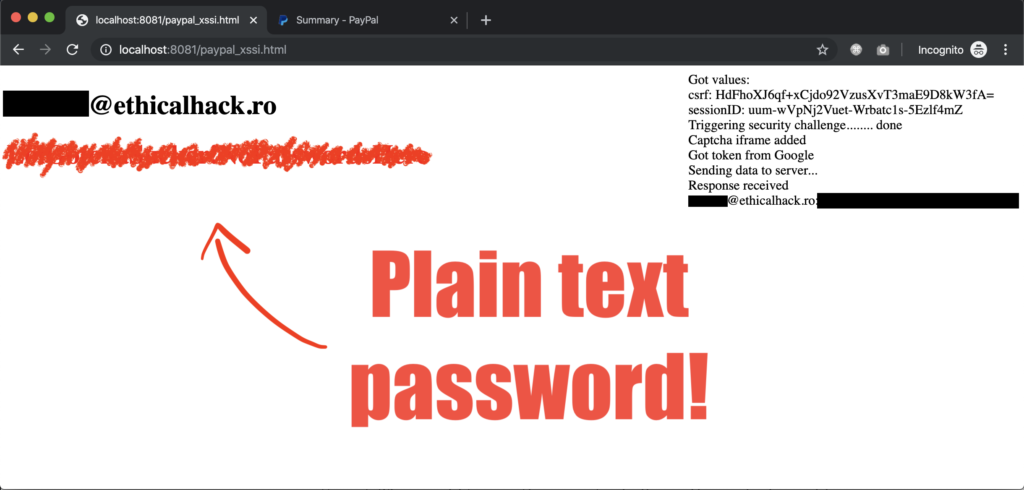
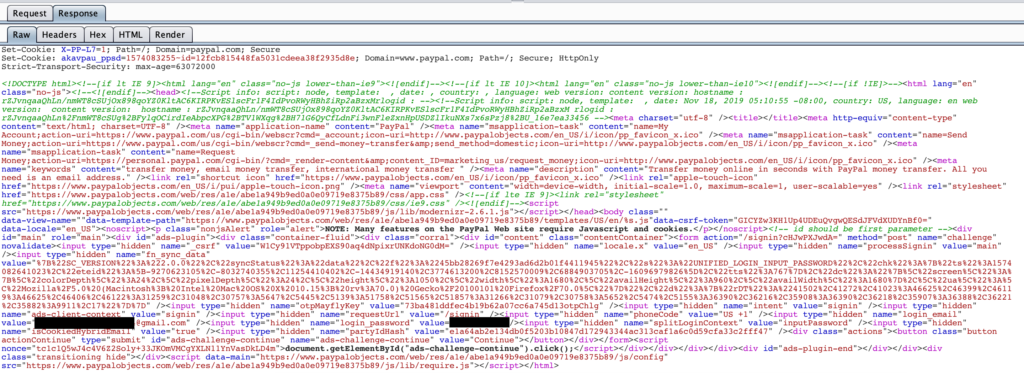
Researcher Alex Birsan has found a bug in PayPal which enables an attacker to retrieve CSRF tokens and session IDs and to perform XSSI attacks against users of the platform. The repercussions of this include the stealing of authentication tokens, and although cross-site forgery attacks are still not possible, there’s another way in. The researcher discovered that after a few failed login attempts, you are required to solve a reCAPTCHA on PayPal. This can be used by the attacker to tap onto the authentication flow and using the token, one could read the victim’s email and password in plain-text form.
Source: Medium
Birsan earned $15300 for this discovery which occurred back on November 18, 2019, and PayPal patched the bug on December 11, 2019. However, the fact that some unique tokens have been leaked, which could have led to account takeovers. A common method to trick someone into falling victim to this would be to convince them to follow a login link from a malicious website, something similar to a standard phishing web page. If the victim lands there, the website could simulate a brute force attempt by launching a series of random authentication requests, triggering the reCAPTCHA step, obtaining a fresh token, and finally retrieving the plaintext credentials.
Source: Medium
All that said, what the users had to do in order to stay safe was avoid following a PayPal login link from a malicious website. If they did, they should at least avoid entering their PayPal credentials on the landing page. Considering that malicious websites are hard to identify sometimes, and with the bug fixed now, that’s all there is to this story for now. Whether or not there has been actual exploitation of this in the real world has not been clarified. As the researcher points out, PayPal could have mitigated the risk by simply never storing the password in plaintext form in the cache, which is a basic precautionary measure really.
PayPal is continuously running bug bounty programs on HackerOne, paying $20000 for critical vulnerabilities, $10000 for high severity bugs, $1000 for medium, and $100 for low. The vulnerability that is described above came into light thanks to bug bounty programs like this, which highlights the importance of providing incentives for security experts to dig deeper and figure out potential ways to attack the users of the platform. So far, PayPal has paid over two million US dollars for 856 researcher reports.