New PayPal Phishing Campaign is Asking for People’s Full Identities
- A dangerous new PayPal phishing campaign is underway and asking for everything they can steal.
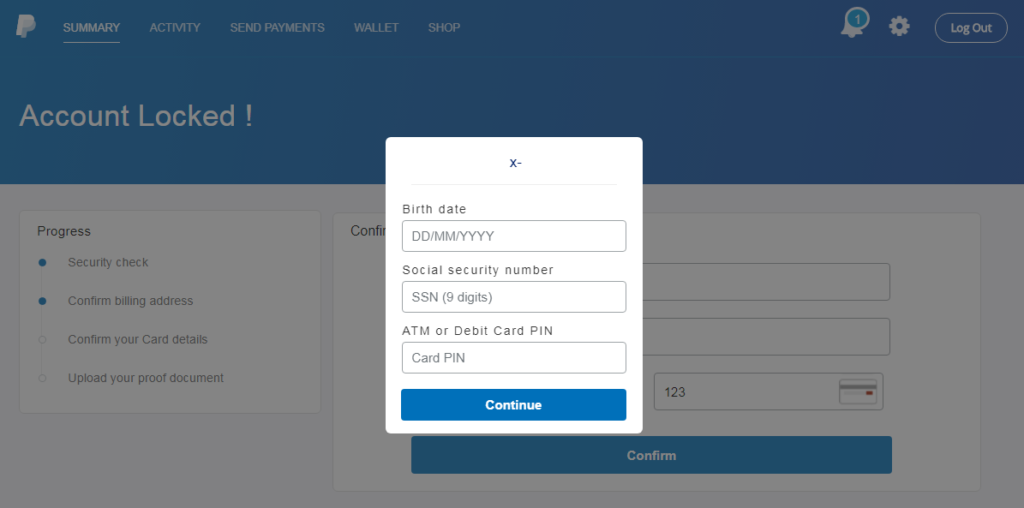
- The actors request credit card numbers, CSCs, PINs, ID cards, passports, SSNs, phone numbers, and more.
- Although the campaign has been reported to PayPal, the malicious domains remain online.
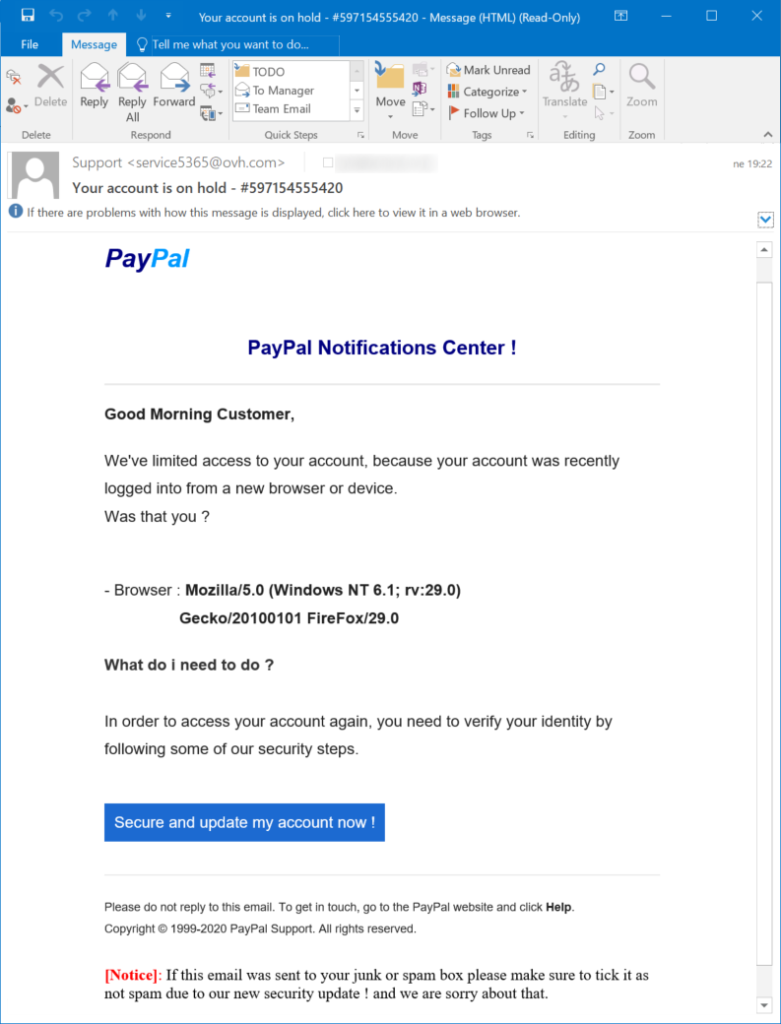
Many internet users report that they have received a new phishing email that informs them about a lock that has been imposed on their PayPal account. The reason given is that someone has supposedly tried to log in to the holder’s account from an unrecognized browser or device, and the message even includes the associated details of this attempt, which are obviously fake. As it happens in these campaigns, the recipient is urged to click on a button which leads to the phishing page, and in this case, the button writes “Secure and update my account now!”.
Source: isc.sans.edu
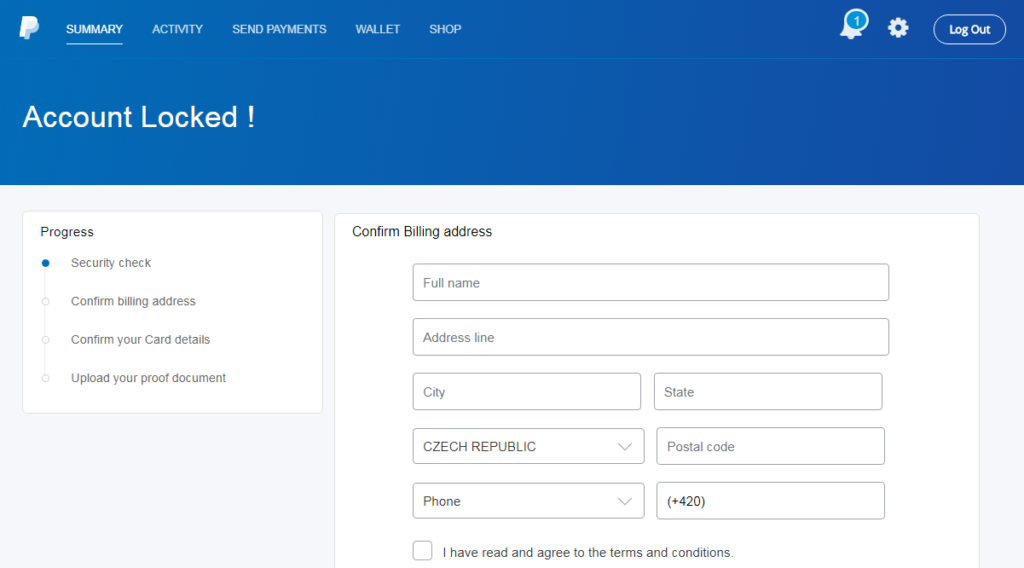
Pressing this button activates a series of redirections which eventually lead to the phishing page. The involved URLs are “bit[.]ly/2SwO61R”, “nadhirotultaqwa[.]com/usrah/redirect.php”, and “leemou[.]com/files/selector/”. As expected, the landing page features PayPal’s logo, theme, and colors, so it looks convincing enough to do the trick in most cases.
Source: isc.sans.edu
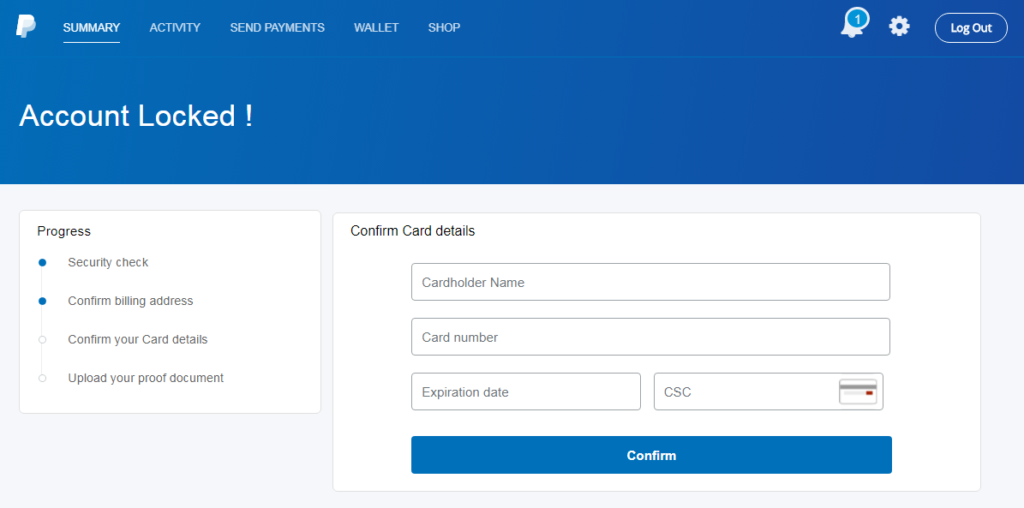
The actors are asking for a galore of data from the victim, like their full name and phone number, and their full credit card details including the CSC security code and even the PIN number.
Source: isc.sans.edu
Source: isc.sans.edu
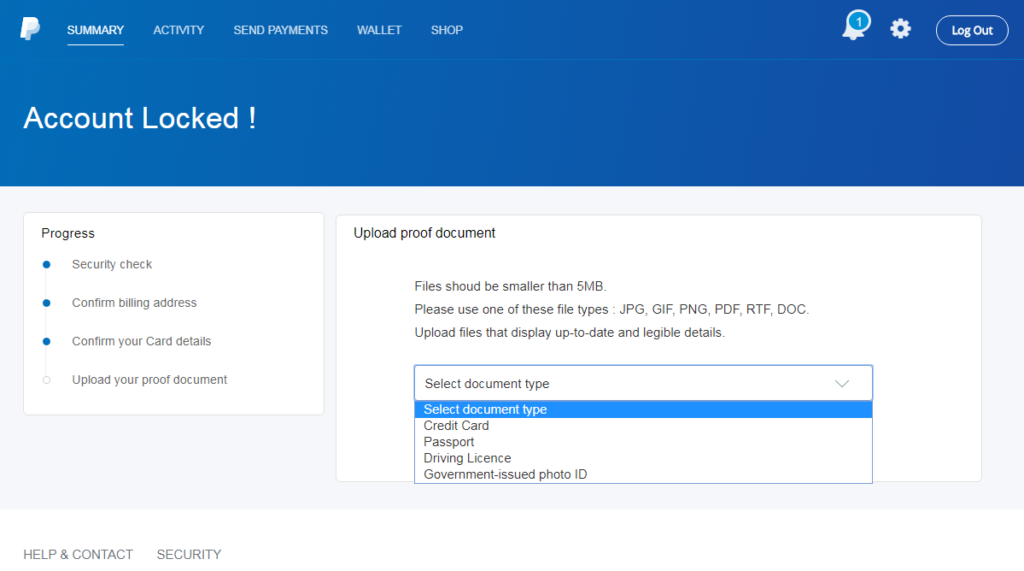
On the next step, the victim is requested to upload their ID, Social Security Number (SSN), or passport. These documents are supposedly asked in the context of identity authentication and must be uploaded by the victims in the form of a PDF, PNG, JPG, or DOC file type. As there is no confirmation of the upload, the victims may try to upload more documents in the hope that they will get accepted.
Source: isc.sans.edu
So, the actors of this campaign are following a very aggressive approach thinking that if the victim is gullible enough to believe that their account has been locked, why not try to steal everything from them. Sure, asking for more information increases the chances of losing some victims along the way, but maybe it is worth it for what you’ll get from those who are willing to give it all.
Jan Kopriva who prepared a detailed post about this campaign has reported it to PayPal, but the malicious domains are still up and running, so it may be a while before the online payments giant acts. Until then, remember, when you receive messages of this type, never click on the embedded buttons on these messages. Instead, head directly to the platform that supposedly sent you the message, log in on the official portal, and check if there are any pending alerts or messages that require your attention.