Patch Your Linux System Now to Shut the Door to “FreakOut”
- A new malware called FreakOut is spreading rapidly across Linux systems that use unpatched software.
- The particular tool has several features, including coin-mining, lateral movement, and DDoS.
- Patching is the best way to deal with the FreakOut risk right now.
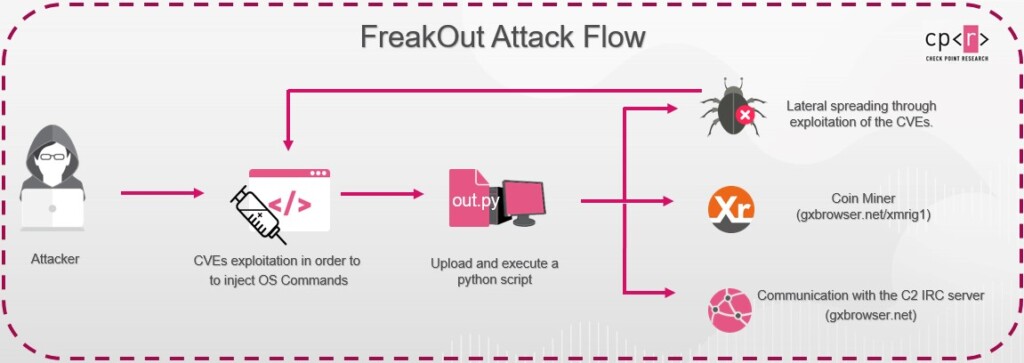
There’s a new malware in circulation right now called FreakOut, which is capable of exploiting three vulnerabilities, all fixed by recent patches but largely non-applied. The attackers spread FreakOut to infect systems with Monero crypto-miners, move laterally across corporate networks, and even launch DDoS (distributed denial of service) attacks against other organizations.
According to the detailed report compiled by researchers of Check Point, the FreakOut campaign is quite active at the moment, counting over 380 attack attempts against its customers alone between January 8 and 13, 2021.
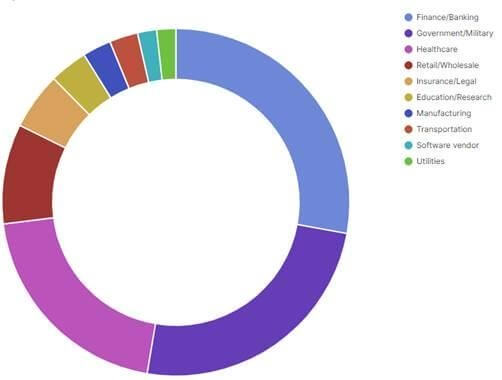
To dive into some demographics, about a quarter of all attacks target U.S.-based entities, while the rest are mostly in Europe. As for the industry sectors that are targeted by FreakOut, the top three are finance/banking, government/military, and the healthcare sector. These three account for almost 70% of all attacks.
The malware exploits the following three vulnerabilities:
- CVE-2020-28188: TerraMaster TOS 4.2.06 and older – Lack of input validation in the “makecvs” PHP page leading to the injection of OS commands to gain control of the target server.
- CVE-2021-3007: Zend Framework 3.0.0 – Unsecured deserialization of an object leading to the abuse of the Zend3 feature and the subsequent code execution in the server via the “callback” parameter.
- CVE-2020-7961: Liferay Portal 7.2.1 CE GA2 and older - Java unmarshalling flaw that leads to remote code execution through the provision of a malicious object.
The capabilities of FreakOut are the following:
- Port Scanning utility.
- Collecting system fingerprint (device address MAC, IP, memory information, TerraMaster TOS version).
- Creating and sending packets.
- Brute Force – using hardcoded credentials.
- Handling sockets.
- Sniffing the network through “ARP poisoning.”
- Spreading to different devices, using the “exploit” function.
- Gaining persistence by adding itself to the rc.local configuration.
- DDoS and Flooding – HTTP, DNS, SYN.
- Opening a reverse-shell – shell on the client.
- Killing a process by name or ID.
- Packing and unpacking the code using obfuscation techniques to provide random names to the different functions and variables.
To stay safe and protected against FreakOut infections, all you need to do is apply the available patches on the three aforementioned tools. If you’re infected already, you will notice some performance hiccups due to the coin-mining activity and the FreakOut DDoS botnet’s participation. If that’s the case, you will find the associated processes running silently in the background.