‘ParkMobile’ Data Stolen Two Weeks Ago Now Offered for Purchase Online
- The ‘ParkMobile’ data that was stolen in March has now appeared on a popular hacking forum.
- The stolen database was already for sale on Russian-speaking forums but for a much higher price.
- The samples show that some things the firm claimed to not have been exposed are present in the pack.
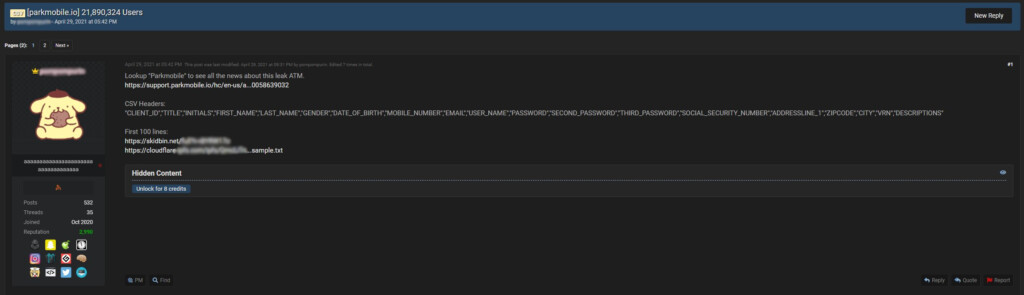
It didn’t take long before someone offered the entire ‘ParkMobile’ data set for a lower price on hacking forums, and it certainly won’t be long until someone leaks it for free. The seller has even provided 100 entries as a sample, and they appear to be a direct database extraction.
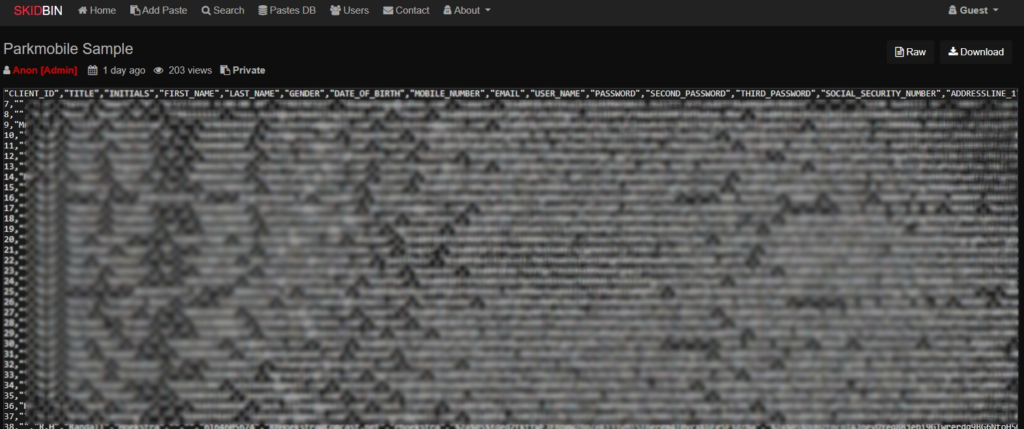
The contents, which allegedly contain details of 21,890,324 users, include the following:
"CLIENT_ID","TITLE","INITIALS","FIRST_NAME","LAST_NAME","GENDER","DATE_OF_BIRTH","MOBILE_NUMBER","EMAIL","USER_NAME","PASSWORD","SECOND_PASSWORD","THIRD_PASSWORD","SOCIAL_SECURITY_NUMBER","ADDRESSLINE_1","ZIPCODE","CITY","VRN","DESCRIPTIONS".
On April 13, 2021, Gemini Advisory discovered the data pack on a Russian-speaking cybercrime forum, listed as a fresh offering resulting from a March 2021 incident. The seller placed a price tag of $125,000, which was quite high for this type of data. This time though, the price is set much lower on the new offering, so access to the leaked data can be considered widespread now.
The service responded with an additional security notice and then returned two days afterward to assure the clients that no credit card information was accessed. Similarly, transaction histories, encrypted passwords, social security numbers, driver license numbers, and dates of birth couldn’t have been compromised, according to ParkMobile.
As we see now from the samples, social security numbers are unfortunately included. Also, the "first password" appears to be hashed (bcrypt), but the others (second, third) are shown in cleartext form. All in all, the data that has been leaked isn’t insignificant by any means and definitely requires the attention of the exposed customers. The exploitation may have begun two weeks ago, but it is now going to explode to new proportions.
If you are a user of the ParkMobile services, beware of incoming SMS or email messages, scamming attempts, and phishing. Resetting your passwords anywhere where you may have used the same credentials should also be a priority now. The particular encryption used for the passwords isn’t uncrackable, especially if the users have chosen a weak password, to begin with.