Pakistani Software Firm ‘We Code Solutions’ Linked With Underground Spam Operations
- A company named ‘We Code Solutions’ was linked with years-long spam kit selling operations.
- The owners and employees of the firm weren’t even bothering to hide their underground activities.
- The U.S. prosecution has been gathering evidence on the spammers for two years now and is still at it.
The Karachi-based software firm ‘We Code Solutions’ has been linked with massive underground operations such as selling spam kits and advanced tools to a large number of actors since 2015. The evidence is laid out by investigative journalist Brian Krebs who has found out that the Pakistani firm and its employees are not even trying to hide the fact as they are proudly posting clues on social media, registered domains that have been used for the dissemination of spam with their real identities, and host seemingly legitimate and obviously malicious websites on the same servers.
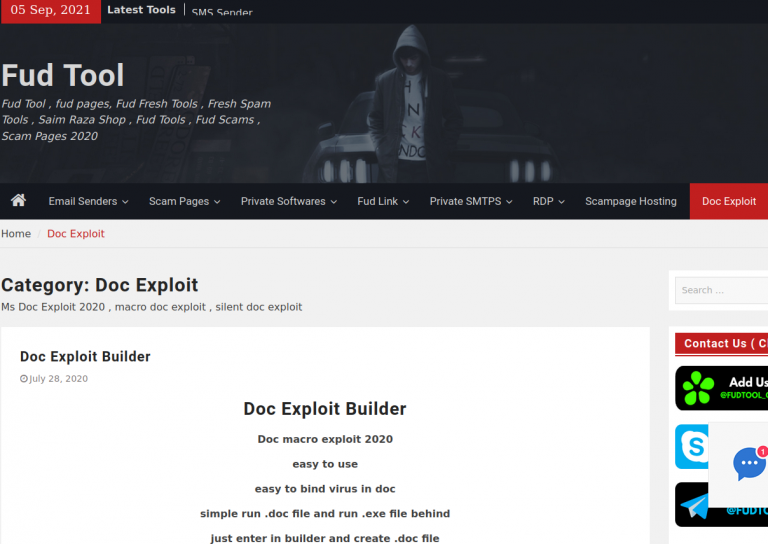
Krebs has been following the group he named “The Manipulaters” for years now and connected them with underground identities such as “Saim Raza,” “Fudtools,” “Fudpage,” and “Fudsender.” The “FUD” part that is often used is an acronym that stands for “Fully UnDetectable,” supposedly reflecting the low anti-virus and anti-spam detection rates that one can enjoy by using the “Fud Tool.”
A characteristic example of the fact that the employees of ‘We Code Solutions’ were not even trying to hide their underground operations is an image of a cake from an office party writing “FudCo” in the center, posted on the firm’s Facebook page.
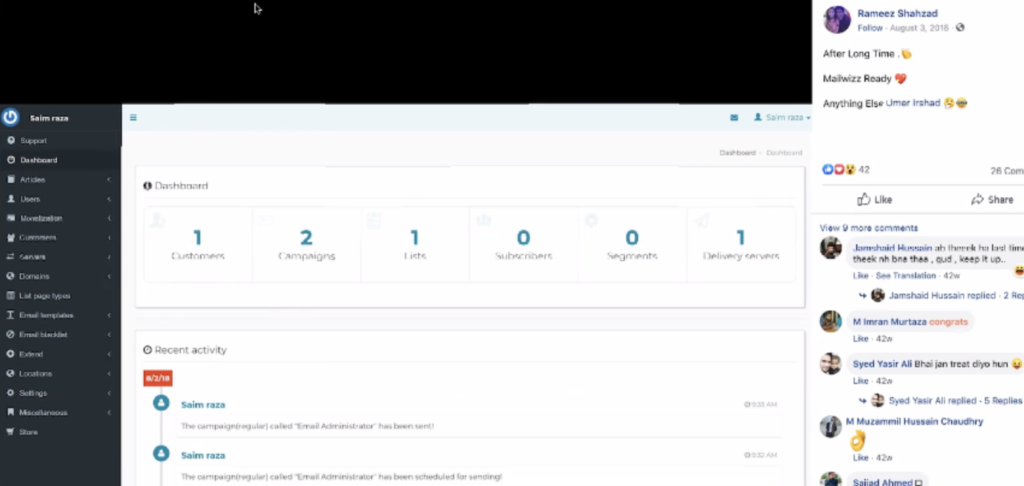
In another case, Rameez Shahzad, a team leader in the firm, has posted a screenshot from his work on a WordPress site to demonstrate something that’s coming soon, exposing the username Saim Raza. Not bothering to use a different username is indicative of the person’s general stance, as Krebs reports that the actor is using the same password (“lovetears”) across a number of email addresses the journalist was able to link to him.
The event that caused the most catastrophic exposure for the actors is when the manipulaters[.]com expired, giving the opportunity to ‘Scylla Intel,’ a cyber intelligence firm, to hop in and grab it. This opened the way for accessing the email accounts and gather very revealing information about the owners and their clients.
Right now, U.S. federal investigators are gathering information and evaluating all the pieces of incriminating evidence, preparing a case against the spamming firm, its owners, and even some of its employees. Such is the volume of evidence that even the U.S. law enforcement authorities have been overwhelmed.