Pakistani Government Website Compromised Using ScanBox Keylogger
- Trustwave’s SpiderLabs Research team identified an instance of the ScanBox keylogger tool on a Pakistani passport application tracking website.
- Authorities were notified about the breach earlier this month, and the vulnerability has been patched.
- The researchers have been unable to identify the number of affected users so far.
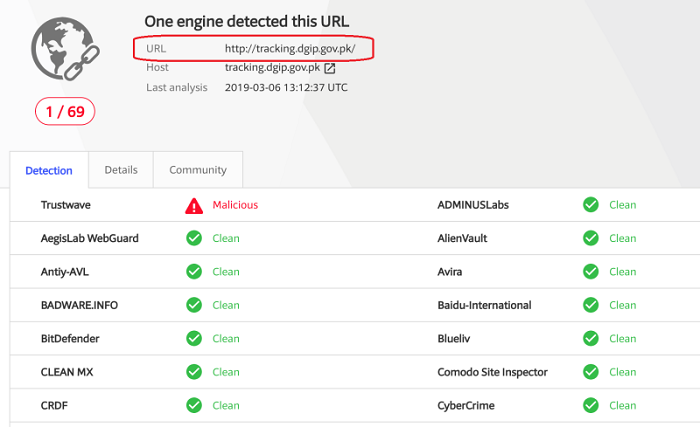
A Pakistani website that allowed citizens to track the status of their passport applications has been compromised according to a report by Trustwave's SpiderLabs Research team. Security researchers at AlienVault conducted two examinations of the ScanBox framework payload that was first seen during 2014 and 2015. The self-contained payload was found to be capable of logging all keyboard activity when browsing a website.
The ScanBox framework payload resurfaced in 2017, which was allegedly used by the Stone panda APT group. Last year, the payload was seen yet again in connection with LuckyMouse, and the researchers have noted that the tool evolved every time. Trustwave researchers discovered the intrusion on the Pakistani website recently, which has potentially allowed hackers to steal keystroke data on the website.
The latest version of the ScanBox framework scans for security products, decompression tools, and virtualization tools. The ScanBox tool is deployed by hackers to steal information on a web site's visitors, and the collected data can be used for targeted attacks.
The Pakistani website did have detection methods in place, but the ScanBox malware is listed as safe by most popular scanning tools. The compromised website was first detected on March 2, and it is unknown how long the keylogger was active.
After the Pakistani website was found to be compromised, tracking user data revealed that hackers were able to collect information from at least 70 unique visitors and about a third of them entered sensitive credentials. After the Trustwave researchers started digging deeper for malicious content, the server storing the stolen data was taken down on March 7. The domain is no longer marked as malicious, but it is unknown how many users have been affected till date.
What do you think about the Pakistani Government website being compromised by ScanBox? Let us know in the comments below. Also, join us on our TechNadu’s Twitter handle and Facebook page for instant updates.