Over 77 Million Nitro PDF User Records Shared Online for Free
- The products of last year’s Nitro PDF massive breach are now being shared online for free.
- The 14GB database includes over 77 million unique email addresses, along with IPs, names, and bcrypted passwords.
- The widespread exposure will now bring a spike in phishing and scamming attempts against millions of people.
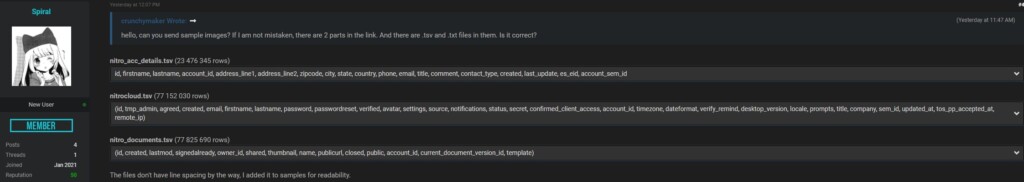
Former and current users of the ‘Nitro PDF’ software are getting notices of a data leak affecting them from ‘have I been pwned?’. Apparently, someone claiming to be part of the “Shiny Hunters” data broker ring has decided to leak a 14GB database containing 77,159,696 records.
They shared it for free on hacking forums, potentially introducing security risks for a large number of people. Reportedly, Nitro PDR was breached back in September 2020, so a limited team of hackers has been exploiting the data set privately for about five months already.
The widespread leak now adds more problems to the compromised individuals, as many more actors will now scrutinize the large volume of the data, and the targeting spectrum will open up to cover everyone. The records in the database include the following details:
- Full names
- Email addresses
- Passwords (bcrypted)
- Company and title
- IP addresses
- System information
Judging from the amount of the records, the database must concern the entire userbase of Nitro PDF. People are using the software to create, edit, sign, and secure PDF files, so several corporate clients are included in the database, like Apple, Citi, Google, Microsoft, Amazon, and more.
Possibly, these have been already targeted by the original actors, who were most likely cherry-picking their targets among the massive dataset. Also, Cyble had discovered that the database was being sold to anyone interested for $80,000 when the breach happened.
Nitro PDF had disclosed the security incident back in October, about a month after it happened. As they stated back then, the incident didn’t expose sensitive financial data nor actual documents. From what appears to be the case now, this was an accurate statement, although the incident was still wrongfully categorized as “low impact.”
Having full names, email addresses, IP addresses, and job details exposed creates a high-quality basis for phishing actors and scammers to act. Also, credential stuffing is always a possibility, even if the passwords were bcrypted, as this wouldn’t help much in cases of small and weak selections.
If you have received a notification from ‘have I been pwned?’, go ahead and reset your passwords and use something strong and unique this time. Ideally, just pick a password manager and generate “ridiculously” secure passwords everywhere.