Over 3,000 GitHub Accounts Used by ‘Stargazers Ghost Network’ to Distribute Malware
- A network of GitHub accounts distributes malware or malicious links via phishing repositories.
- Stargazers Ghost Network uses north of 3,000 accounts for malware distribution that mostly focuses on infostealers.
- This Distribution-as-a-Service is operated and maintained by the Stargazer Goblin threat actor.
A network of multiple GitHub accounts named ‘Stargazers Ghost Network’ was seen distributing malware and malicious links via phishing repositories. The network acts as a Distribution-as-a-Service (DaaS) and is operated by the ‘Stargazer Goblin’ threat group, as per a new report from Check Point Research.
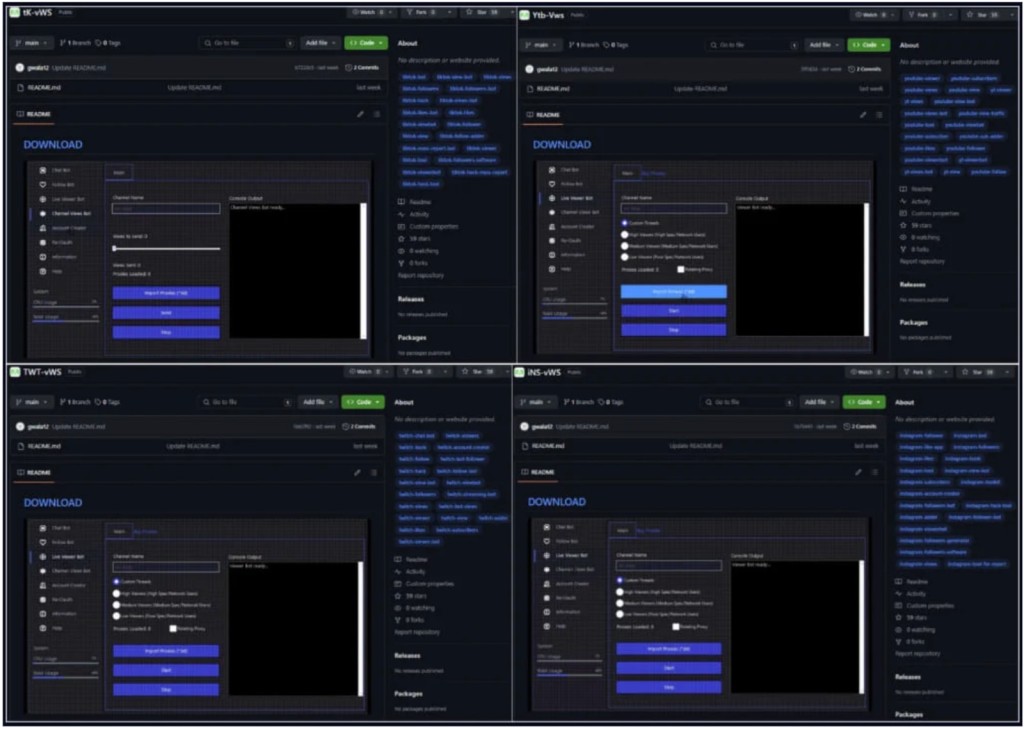
The over 3,000 active Ghost accounts mostly distribute info stealers such as Lumma Stealer, RedLine, RisePro, Rhadamanthys, and Atlantida Stealer. These are also used to star, fork, and subscribe to malicious repositories to create the illusion they are legitimate.
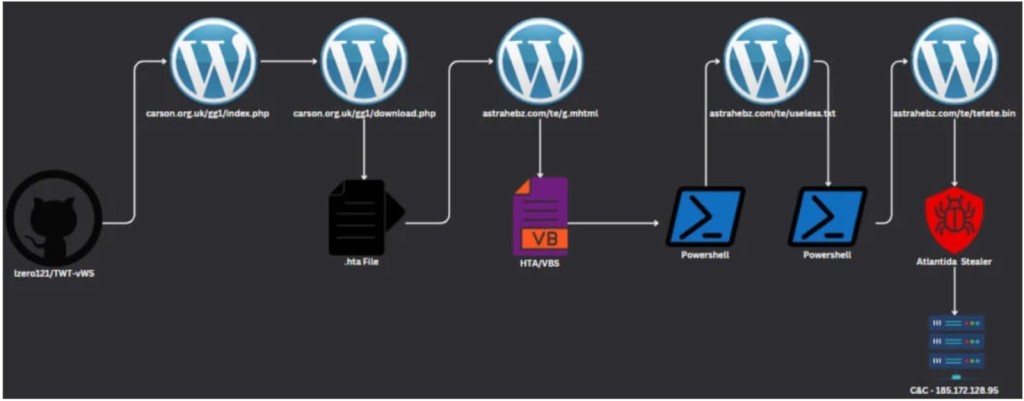
Some of the Ghost accounts appear to have been created by their operators. However, others seem to be compromised standard GitHub user accounts. These could belong to victims who got infected with an info-stealer by clicking a malicious download link directing to a script download on a compromised WordPress website.
More than 1,300 victims installed software from more than 2,200 seemingly harmless repositories across four days of monitoring in January 2024, when the network distributed Atlantida Stealer. This new malware family exfiltrates user credentials, cryptocurrency wallets, and other personally identifiable information (PII).
In the monitoring period, the malicious links to GitHub repositories were possibly distributed via Discord channels, targeting people who wanted to increase their follower numbers on Twitch, Instagram, YouTube, Twitter, Trovo, and TikTok or use other tool-related features for Kick Chat, Telegram, email, and Discord.
Around 380 Ghost accounts were used in a campaign of approximately 30 repositories also containing phishing templates for cracked software and other crypto-related activities. The attack chain utilized malicious scripts hosted on compromised WordPress websites.
The network evades GitHub’s scanning solutions by using password-protected archives and minimizes and recovers any damage resulting from GitHub disruptions by utilizing multiple accounts and profiles performing different activities.
Network development or testing on a smaller scale may have started around August 2022, security experts believe, who discovered on Dark-Web forums an advertiser for this exact GitHub operation, with its first post in July 2023.
Security researchers estimate Stargazer Goblin earned approximately $8,000 from May to June 2024 and approximately $100,000 during the operations’ lifespan. Other Ghost accounts were seen activating on different platforms as part of the DaaS operation.