Operation “Transparent Tribe” is Back Online Targeting Indian Officials
- Pakistani actors have brought operation “Transparent Tribe” back online, sending malicious documents to Indian military agents.
- The documents run a macro that drops a RAT, which then fetches additional payloads that can run commands remotely.
- The operation may have been alive in the previous years too, but researchers first noticed it four years ago.
Back in February 2016, Proofpoint researchers warned about an APT group targeting Indian diplomatic and military resources by deploying custom RATs (Crimson and Peppy), malware, watering hole websites, phishing email campaigns, and a large variety of data-exfiltration tools. Back then, it was discovered that the attacks originated from IPs in Pakistan, which made sense considering the tensions between the two countries. Now, researchers from the Cybaze-Yoroi ZLab have discovered similar activity which first appeared during the past month, indicating that the operation “Transparent Tribe” has returned.
Source: blog.yoroi.company
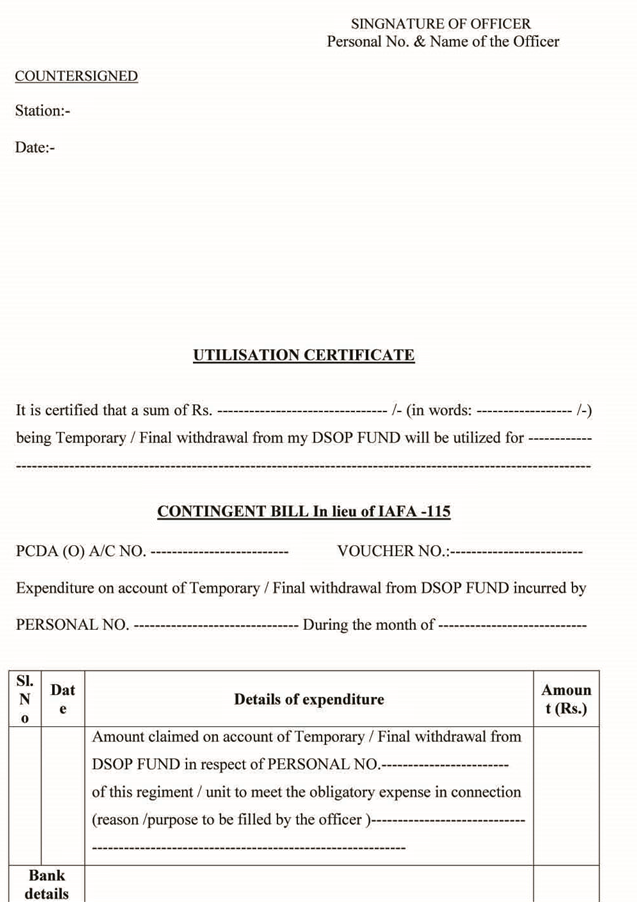
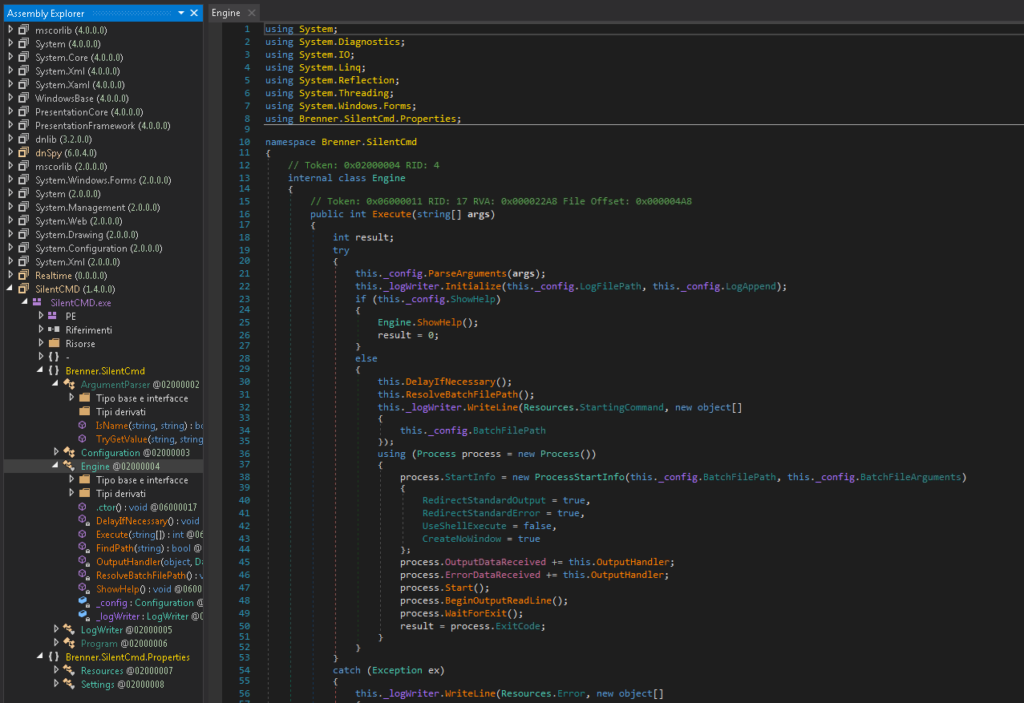
The infection begins with the reception of a malicious email attachment (document) that supposedly comes from the “Defense Services Officers Provident Fund”. This is the organization responsible for handling the deposits of money meant to support a mandatory “welfare” savings fund for Indian military personnel. Thus, the targeting is very specific, and the bait is quite alluring for the recipients. The document contains a self-extracting macro which features light obfuscation, and which creates two folders and extracts several files inside them. One of them is the “SilentCMD” remote code execution tool that listens to commands from the C2 and runs them on the infected machine. Another malicious file is the “Realtime.cs” which can fetch more payloads from the C2.
Source: blog.yoroi.company
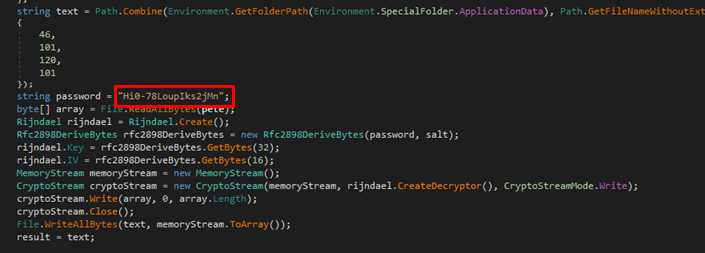
The main malware used in “Transparent Tribe” is a modular RAT that was written in .NET and has a creation date of January 29, 2020. It can list the running processes on the machine, and send them back to the C2 server. The communication between the two is encrypted, based on an RSA key that is provided by the malicious infrastructure (“hxxp://www.[awsyscloud[.com/”, “hxxp://www.[awsyscloud[.com/x64i[.scr”). When requested to download additional payloads, the code is being encrypted through the Rijndael algorithm using a key that’s hard-coded into the malware.
Source: blog.yoroi.company
Four years after the “Transparent Tribe” was first noticed, it is likely that the actors were still playing the game, but were more stealthy and careful. The tensions in the relations between India and Pakistan have returned to a regressive state since August 2019, when the Indian Parliament passed the “Jammu and Kashmir Reorganization Bill”. Since then, everything followed a downward spiral of deterioration, as the two states became one, their semi-autonomous status was nullified, and even the internet in the area was shutdown (remains heavily restricted). With all that is going on, cyber-warfare between the two may intensify, although other international leaders call for a resolution.