Operation Magnus Disrupts RedLine and Meta Infostealer Networks
- The notorious RedLine and Meta infostealers were disrupted thanks to a coordinated international operation.
- Dubbed Operation Magnus, the joint effort dismantled the prominent malware networks’ infrastructure.
- The authorities also revealed a list of VIP clients of these malware-as-a-service models.
Operation Magnus has successfully disrupted the operations of two prominent infostealer malware networks, RedLine and Meta. This coordinated international effort, led by the Dutch Police and supported by the FBI and authorities from the UK, Australia, Portugal, and more, marks a major blow against cybercriminal activities worldwide.
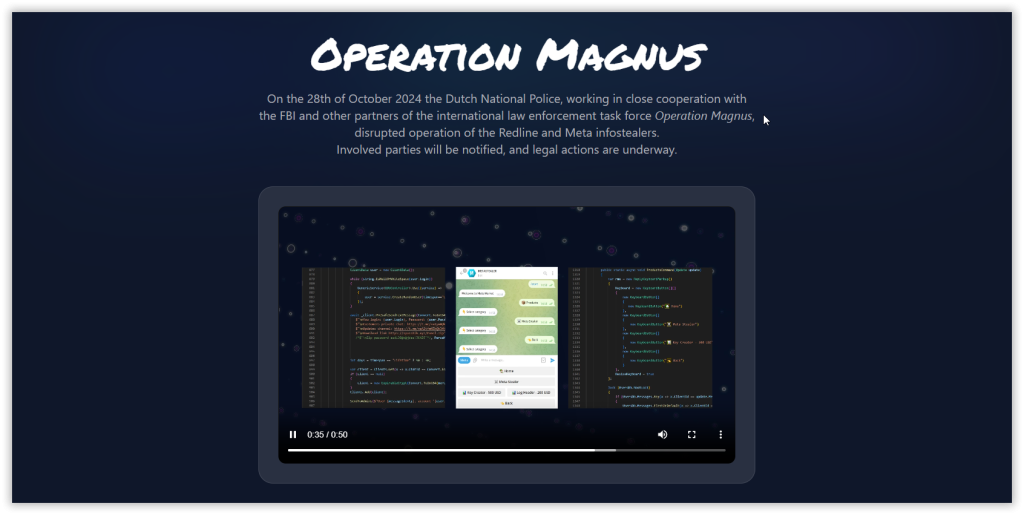
A 50-second video released by the authorities highlights the commonalities between RedLine and Meta stealers, underlining the operation's success in dismantling their infrastructure. The video also showcased a list of "VIP clients," though it remains unclear if these individuals have faced legal repercussions.
According to the official notice posted on the takedown's dedicated website, law enforcement agencies have gained full access to the servers of both RedLine and Meta infostealers. Authorities have identified critical data, including usernames, passwords, IP addresses, timestamps, and registration dates linked to these infostealers' dark web clientele.
The sophisticated takedown involved breaching the mainframe infrastructure, licensed servers, REST-API servers, and even the Telegram bots that facilitated the malicious network's operations across social networking and messaging channels.
The operation's impact is substantial, providing unparalleled insights into users of the malware-as-a-service (MaaS) model, which has been a growing concern in cybersecurity circles.
Further information is expected to be released soon, as indicated by a countdown timer on the operation's website. A joint statement from the involved international law enforcement partners is expected to shed light on additional outcomes and future actions related to Operation Magnus.
The manner of revealing details through a dedicated website and video announcements parallels past operations like "Operation Endgame," which targeted significant botnet infrastructures associated with various notorious malware droppers.
This October, FIN7’s latest malware campaign was seen leveraging public interest in AI tools that turn pictures into nudes by promoting online and Windows tools that only deliver infostealers like the notorious Lumma Stealer and Redline Stealer.
In August, compromised WordPress websites were observed displaying a fake issue to lure victims into installing malware on their machines, which included the RedLine Stealer.