Opera Browser Fixes Critical Data-Exposing Security Flaw in Recent Update
- A now-patched critical security vulnerability in the Opera browser allowed the exposure of user data.
- A malicious browser add-on permitted access to private APIs, posing serious privacy and security concerns for users.
- This security hole could enable an attacker to tamper with browser settings and steal accounts and screenshots.
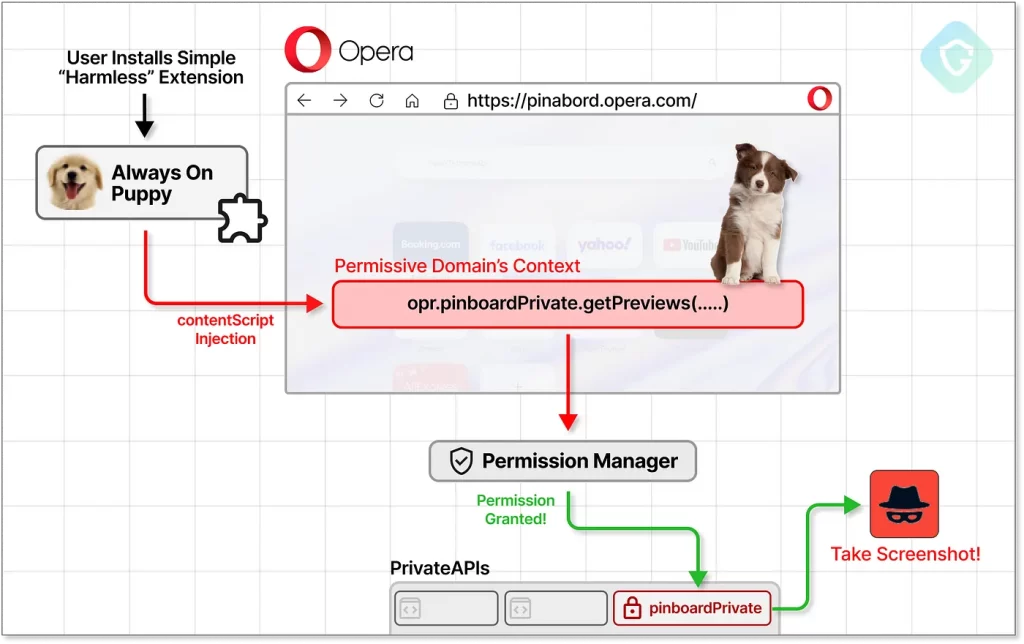
Opera has recently patched a severe security vulnerability that could have exposed user data through a malicious browser extension. Known as CrossBarking, this vulnerability allowed unauthorized access to private APIs, enabling attackers to capture screenshots, alter browser settings, and hijack accounts.
According to Guardio Labs, the flaw was exploitable via an extension disguised as harmless when available on the Chrome Web Store. Guardio Labs highlighted this in their report, authored by Nati Tal, emphasizing the need for vigilant monitoring of browser extensions.
The vulnerability has been thoroughly addressed as of September 24, 2024, thanks to responsible disclosure practices. The recent flaw exploited Opera's subdomains that had privileged access to private APIs supporting features like Opera Wallet and Pinboard.
Guardio's research revealed that content scripts within browser extensions could inject malicious JavaScript into permissive domains, posing significant risks. This access allows potential adversaries to conduct advanced attacks, such as redirecting users to malicious sites through manipulated DNS settings.
To mitigate these threats, Guardio Labs recommends enhancing the review process for browser extensions through increased manpower and continuous activity analysis, alongside enforcing real identity verification for developers.
This is not the first time Opera has addressed security concerns. A previous vulnerability, dubbed MyFlaw, surfaced in January, exploiting the My Flow feature to execute files on the operating system.
The findings from this case study serve as a crucial reminder for users to exercise caution with browser extensions, prioritizing transparency and security in their installation choices.
In other recent news, Lazarus hackers exploited a Google Chrome zero-day in a fake DeFi game attack that involved social media ads, spear-phishing, and LinkedIn to lure in high-value individuals in cryptocurrency.