OnlyFans Hack Infects Other Cybercriminals with Lummac Stealer Malware
- A malicious tool advertising mass verification for stolen OnlyFans credentials contained the vicious Lummac Stealer malware.
- The hack lured other cybercriminals with advanced verification capabilities.
- The hacker also conducted simultaneous campaigns targeting individuals who sought to compromise accounts with other services.
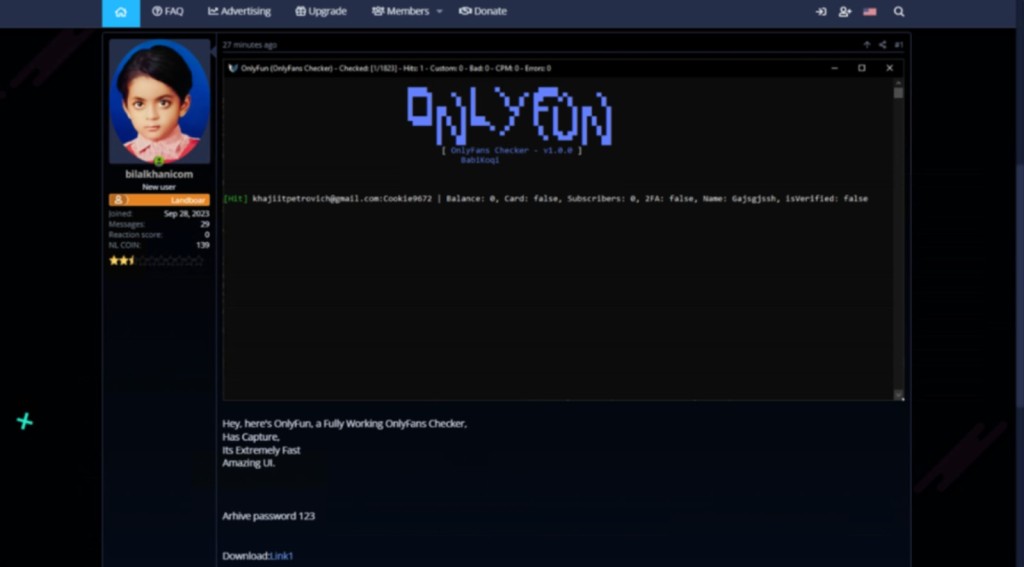
Hackers distributed an OnlyFans “checker” tool that helps bulk-test the validity of stolen credentials belonging to OnlyFans accounts but was laced with the Lummac Stealer malware, Veriti’s research team uncovered.
The OnlyFans tool ostensibly offers features like checking account balances, verifying linked payment methods, and identifying accounts with creator privileges.
This operation was attributed to threat actor Bilalkhanicom, whose parallel campaigns targeted cybercriminals attempting to compromise Disney+ and Instagram accounts and manage botnets.
Upon execution, Lummac Stealer connects to a recently established GitHub account named “UserBesty,” which is a repository for additional malicious payloads and creates exclusions against detection tools.
The malware's command-and-control (C2) communication was linked to newly registered .shop domains with high detection rates, such as caffegclasiqwp(.)shop and ponintnykqwm(.)shop.
Researchers identified potential geopolitical connections within the malware’s structure, as various folder names suggested East Asian, African, Celtic, and Indigenous Latin American influences.
Initially surfacing in August 2022, Lummac Stealer, also known as LummaC2 Stealer, was developed by a threat actor known by aliases Shamel or Lumma and functions as Malware-as-a-Service (MaaS).
The malware shows advanced functionalities and sophisticated loader capabilities, adapting and evolving its attack strategies.
In August, a novel widespread campaign was seen luring victims via fake download sites looking like Roblox FPS Unlocker, YouTube, VLC, or KeePass to distribute Trojans that install malicious web browser extensions to steal sensitive user data.
Also, malvertising campaigns targeting users who search for popular business software, such as Trello, Brave, KeePass, Notion, Steam, and Zoom, deploying a trojanized MSIX installer covertly bundled and distributed alongside legitimate software.