OnionCrypter Uses Three Individual Layers of Encryption
- A crypter that uses three layers of obfuscation has just been discovered and analyzed.
- The particular piece of software has been around since 2016, helping thousands of malware payloads find their way into machines.
- The crypter is very effective in evading AV detection and offers rich customization options.
Avast has discovered a malware crypter that uses an encryption technique that resembles Tor’s Onion network, and thus the researchers named it “OnionCrypter.” Crypters are indispensable parts of malware distribution campaigns. They help crooks obfuscate the wrap their payloads in anti-detection shells that can trick AV tools and dramatically increase the successful infection rates as a result. Oftentimes, these tools are very sophisticated, rotating or enriching their encryption methods to always stay ahead of AV companies.
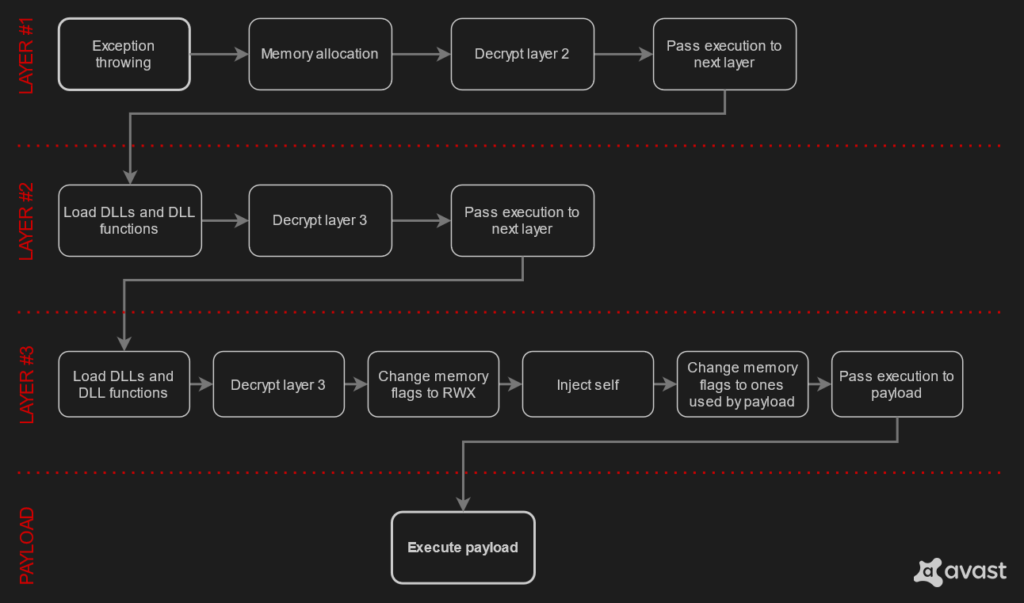
In the case of the OnionCrypter, we have multiple layers of code encryption that remind us of Tor’s Onion network. However, we should clarify that there is no relation or any form of abuse of the encrypted network.
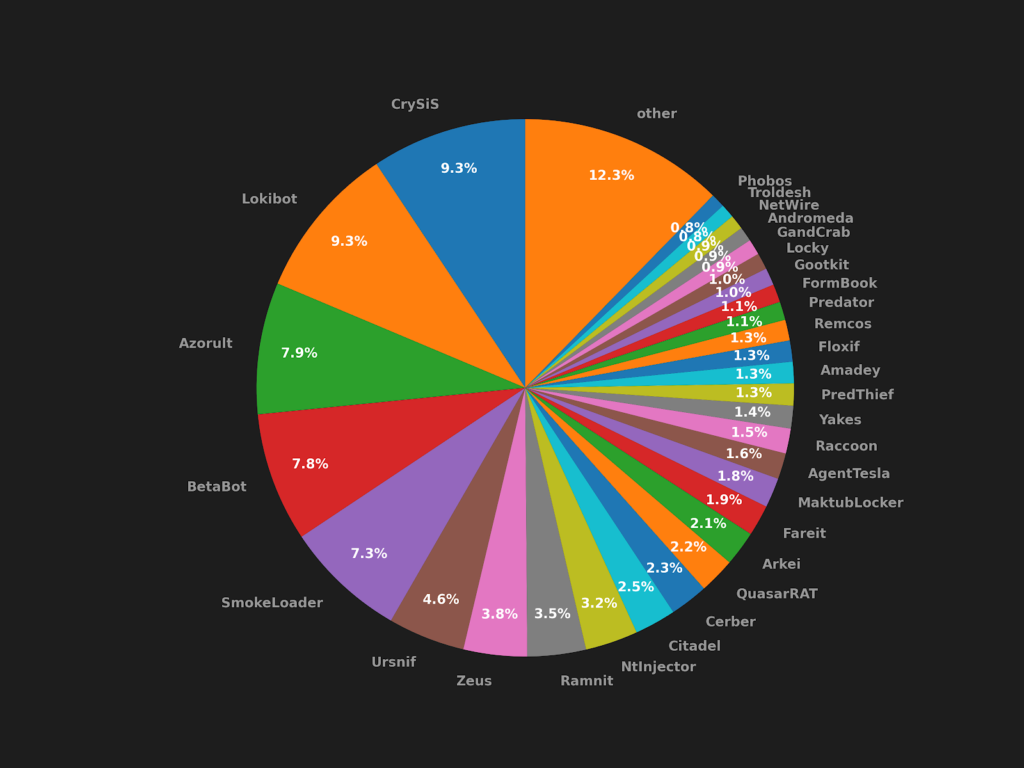
According to the researchers, OnionCrypter has actually been around since 2016, used by malware families such as Ursnif, Lokibot, AgentTesla, Zeus, Smokeloader, and at least another 25 strains. In total, Avast has detected and blocked about 400,000 cases of malware wrapped with the OnionCrypter, so it’s clear that its deployment is pretty extensive.
This tells us that OnionCrypter is almost certainly offered as a service to malware authors and campaigners, which is the case with almost all crypters out there. Avast also mentions some level of diversion in the various samples that they have analyzed, so it seems that OnionCrypter offers its customers the ability to customize it according to their needs, making it less detectable. So, while Avast’s AV solutions caught 400,000 instances, there could be a lot more flying around, which also explains why the particular crypter is still so widely used.
As explained in the relevant analysis, OnionCrypter is a 32-bit software written in C++ and which uses three layers of encryption, each with its own unique tricks. For example, the first layer relies a lot on junk code use, while layers two and three perform a lot of breaking-up in the code. There are several decryption, decompression, and assembly functions taking place when the malware is eventually deployed, but despite the complexity, everything works like clockwork.