Old Excel Macros Still Supporting Large-Scale MalDoc Campaigns
- Yet another MalDoc campaign that relies on obfuscation through old Excel macros has been uncovered.
- The actors are targeting several countries, including India, Cyprus, Italy, Ukraine, and the Vatican.
- The macros plant scheduled tasks that check for incoming commands and exfiltrate system info.
According to a report by the DomainTools Research team, there’s a large-scale MalDocs campaign that has been going on since December 2020 and has passed largely undetected. The actors are using old XLM 4.0 macros in MS Excel documents, creating documents in various languages to target Azerbaijan, Cyprus, India, Italy, Lithuania, Ukraine, and the Vatican. The researchers have named the campaign “Winter Vivern” due to the characteristics of the C2 infrastructure, which is hosted in northern Europe.
The malicious use of XLM 4.0 macros is neither new nor sophisticated in any way, but it remains an effective way for actors to evade detection. Such is the effectiveness of the obfuscation that comes with XLM 4.0 macros that we’ve seen the same trick being adopted by the "Avaddon" ransomware gang last summer - and also two French malware distributors in February 2021. The fact that “Winter Vivern” has been going on since December 2020 and nobody noticed or reported it says it all.
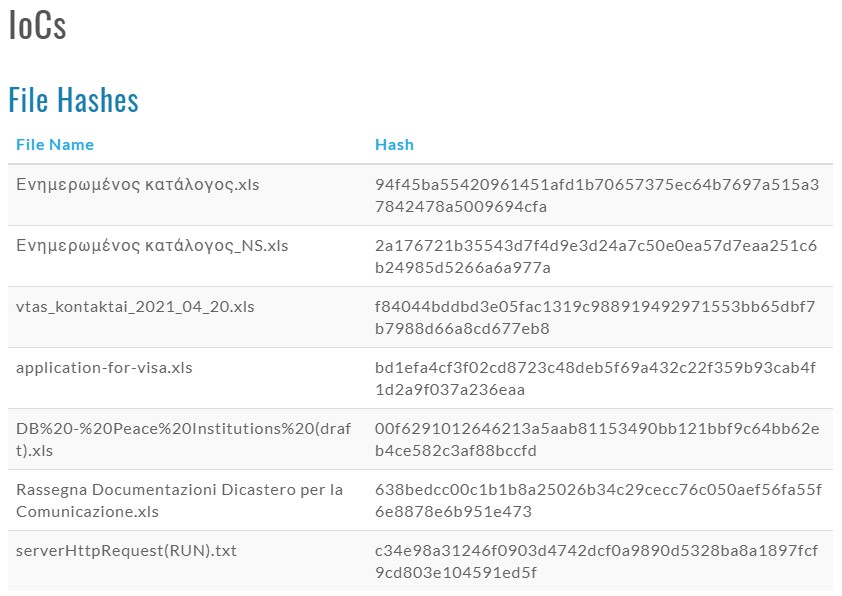
If you have received one of the following files, you have been approached by “Winter Vivern” actors. In this case, you are advised to delete the email immediately, do not download the attachment, and definitely do not open it. Also, keeping your Office suite macros disabled at all times unless you have a good reason to have them enabled is generally the preferable state.
The actors are trying their best to convince the recipients to “enable content,” as expected, and they make false claims about getting the proper functionality and content viewing ability if you do enable it. If the recipient is convinced, the macro will execute a PowerShell script that adds a scheduled task on Windows. This is to exfiltrate all system information to the C2 and then check at regular intervals for any new commands sent remotely. Possibly, there are additional payloads delivered, but DomainTools hasn’t sampled anything.
The domains that distribute these documents are “secure-daddy[.]com” and “securemanag[.]com”, both hosted on 3NT Solutions LLP. Most recently, the actors have added “centr-security[.]com,” which targets Ukrainian language speakers specifically.
It is also notable that the particular domain is spoofing the Council of European National Top-Level Domain Registars (CENTR). We have tested out all three, and they appear to have been reported, so they’re actively blocked by most internet security solutions. However, the actors could jump to other IPs and domains at any time, so beware.