‘NutriBullet.com’ is The Latest Web-Shop to Fall Victim to Magecart Group 8
- Another sign of Magecart Group 8 activity got published, and this time, it concerns NutriBullet.
- The famous blender maker has left its online shop on autopilot, as the malicious actors are loading skimmers at will.
- RiskIQ researchers are playing the role of the good Samaritan for the customers, taking down the exfiltration servers.
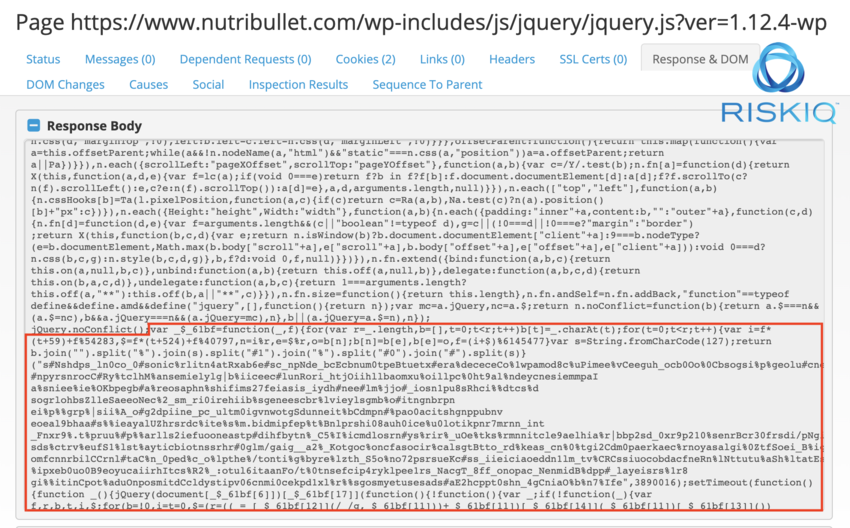
'NutriBullet.com' is the latest victim of the Magecart Group 8, one of the most active card skimming threat groups out there. Apparently, RiskIQ has discovered the JavaScript skimmer on the blender manufacturer's international website on February 20, 2020, and they immediately tried to warn the website administrators of the issue. After multiple attempts of contacting, NutriBullet remained unresponsive, so RiskIQ decided to take the matter onto their own hands. They reached to AbuseCH and ShadowServer and asked them to take down the attacker’s exfiltration domain, essentially putting an end to the flow of card details from the webshop to the Magecart Group 8.
On March 5, 2020, the threat group loaded a new skimmer on the NutriBullet website, and the researchers spotted the new activity and neutralized the infrastructure that was used for the data exfiltration almost immediately. Five days later, the actors tried again with yet another JavaScript skimmer, and RiskIQ responded positively to this incident too. During all this time, NutriBullet remains unresponsive and ignorant of what is happening on their platform, so you are advised to avoid buying anything from them until they finally realize and acknowledge the situation.
Source: RiskIQ
The skimming script that was used in this case by Group 8 is a well-known piece of code that the actors are using since at least 2018. It features variable-validation functions that help it ensure that it’s running on the right page. That would be the payment/checkout page, of course, as the whole point is to steal credit card data, names, user IDs, and bundle everything together. Before sending the data to the actor’s infrastructure, the script is applying encryption for obfuscating the network traffic and avoiding detection. The servers that tried to receive the strings of data from the three skimmers used in NutriBullet were the following:
- https://prodealscenter.com/tr/
- https://freshdepor.com/tr/
- https://swappastore.com/tr/
- https://coffemokko.com/tr/
- https://webanalyzer.net/tr/
NutriBullet is one of the most successful blender brands, selling appliances in the United States and Canada directly from their online shop. The $39.99 "Magic Bullet" is their trade-mark blender that has been replicated by many other brands, and continues to sell very well. Thus, this card-skimming group isn’t just randomly targeting the particular domain. Still, they know they are having good chances of stealing cards that belong to middle and upper-class individuals from the US and Canada.