Novel ToyMaker Initial Access Broker Collaborates with Cactus Ransomware Group
- Security researchers discovered a two-stage operation between the novel ToyMaker IAB and a Cactus ransomware affiliate.
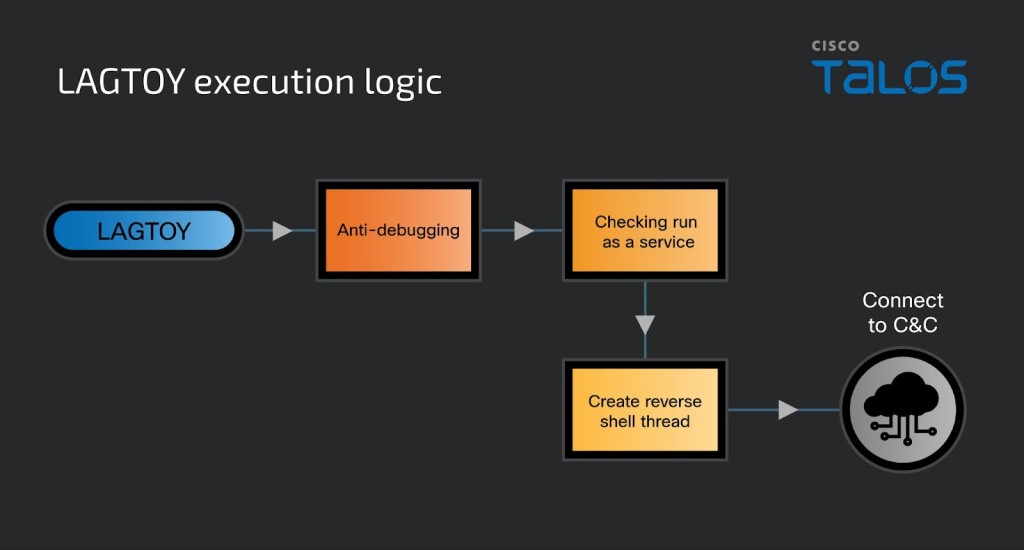
- LAGTOY is the centerpiece of ToyMaker’s operations, a backdoor designed for prolonged yet controlled access.
- The compromise begins with the IAB infiltrating the victim’s environment and extracting credentials.
Emerging threat actor dubbed ToyMaker, an initial access broker (IAB), is reportedly working alongside the Cactus ransomware group to facilitate double extortion attacks, marking another evolution in the ransomware-as-a-service (RaaS) ecosystem.
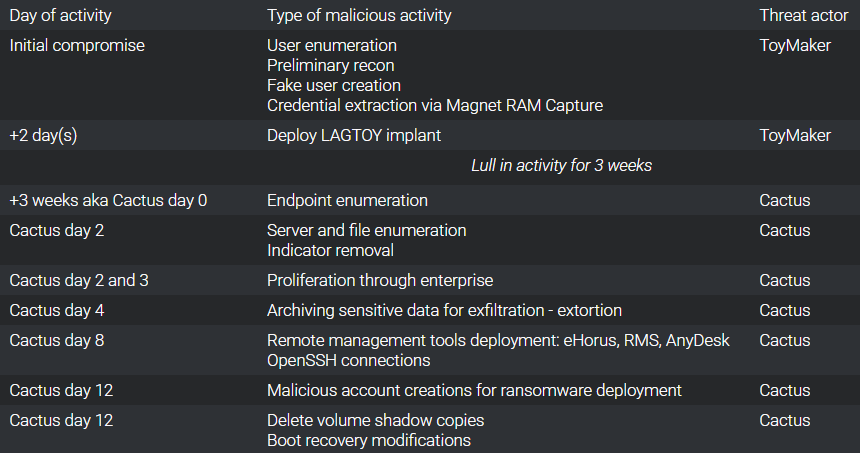
Cisco Talos Intelligence Group’s recent in-depth analysis of a cyberattack targeting critical infrastructure revealed a two-stage compromise, beginning with ToyMaker infiltrating the victim’s environment and extracting credentials.
ToyMaker's malicious toolkit centers around LAGTOY, a custom backdoor capable of reconnaissance, reverse shell commands, and persistent exploitation.
After initial access, ToyMaker hands over control to the Cactus ransomware affiliate to launch attacks, escalate privileges, and deploy ransomware payloads for data exfiltration and extortion.
The process, as documented by Cisco Talos, highlights how IABs like ToyMaker monetize their access without conducting significant data theft themselves, instead passing it off to collaborators who execute the secondary stages of the operation.
The ToyMaker stage includes initial compromise, credential theft, and deployment of LAGTOY, while the Cactus stage involves high-impact actions including data exfiltration, deploying remote administrative tools (eHorus, RMS, AnyDesk, OpenSSH connections), removing traces of activity, and launching ransomware campaigns.
LAGTOY features anti-debugging routines, time-based execution logic, and a command-and-control (C2) system for remote operation, primarily communicating over port 443. The malware’s primary functions include user creation, credential harvesting, and network reconnaissance, enabling attack handover to secondary actors.
LAGTOY also employs techniques such as creating fake user accounts, credential capture via Magnet RAM Capture, and employing Secure Copy Protocol (SCP) for data exfiltration. These tactics showcase the calculated, modular approach typical of financially motivated IABs.
Cisco Talos assesses with medium confidence that ToyMaker operates with no espionage-driven motives but rather as a financially motivated broker. By exploiting unpatched internet-facing servers, such actors procure high-value enterprise access, then resell it to ransomware operators like Cactus, streamlining the path to profit for both sides of the malicious operation.