Novel Android RAT Deployed via Smishing Steals Money Using Account Takeover
- A new RAT was seen infecting Android devices to initiate fraudulent money transfers.
- The malware is distributed via smishing and has account takeover capabilities.
- After stealing the funds, it even deletes all data that could be traced back to the malware.
A novel Remote Access Trojan (RAT) infects Android devices via smishing, employing Account Takeover (ATO) via a well-known technique called On Device Fraud (ODF), as per a recent report from Cleafy. Named ‘BingoMod’ by security researchers, the RAT initiates money transfers from the compromised devices and wipes the device remotely.
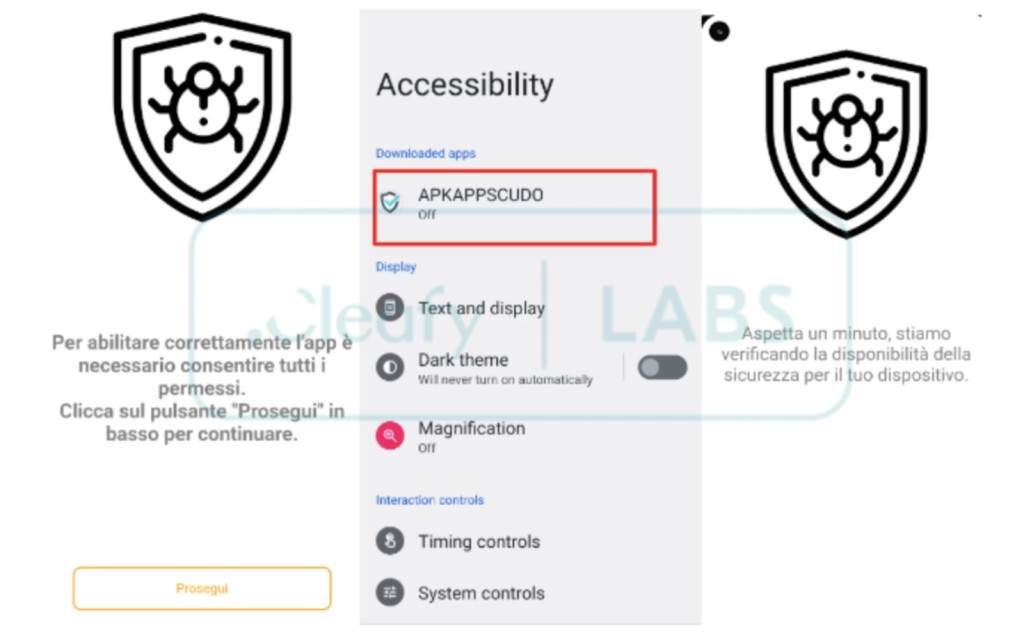
The RAT is distributed via social engineering campaigns, sending fake mobile text messages to lure people into downloading a malicious app that often pretends to be a legitimate antivirus solution.
The ODF technique has already been seen recently in other banking trojans, such as Medusa, Copybara, and Teabot. The malware can also use overlay attacks and fake notifications for phishing activities.
BingoMod displays two features typical of banking Trojans – key-logging and SMS interception – to exfiltrate sensitive user details such as login credentials or account balances and steal transaction authentication numbers (TANs) or one-time passwords (OTPs).
The malware provides around 40 remote control functions, the most relevant ones relating to real-time screen control. They use a VNC-like routine leveraging Android's Media Projection API, capturing screenshots of the victim's device screen at regular intervals and remotely controlling the infected device, clicking buttons, filling in forms, and navigating between apps.
The actors use separate communication channels for these: one socket-based for command transmission (in the case of VNC start/stop) and one HTTP-based for image transfer.
The malware uses security measures like hindering editing system settings, blocking actors-specified apps, and uninstalling arbitrary apps.
After successfully transferring stolen funds, hackers usually wipe the infected device remotely with a dedicated command and also directly from the device's system settings to remove any traces of suspicious activity.
According to the malware code comments, its developers speak English, Romanian, and Italian.
Recently, five campaigns were seen targeting Android users with trojanized apps in Egypt and Palestine. The threat actor was identified as the cyberespionage Arid Viper APT group.