Novel Security Researcher-Developed Tool Bypasses Google Chrome’s Cookie Encryption
- Google Chrome's cookie encryption system has met another issue, this time in the form of a publicly available bypassing tool.
- The tool developed by a cybersecurity researcher can decrypt cookie data stored in Chrome's Local State file.
- Newer methods even employ indirect decryption without directly interacting with Chrome's Elevation Service.
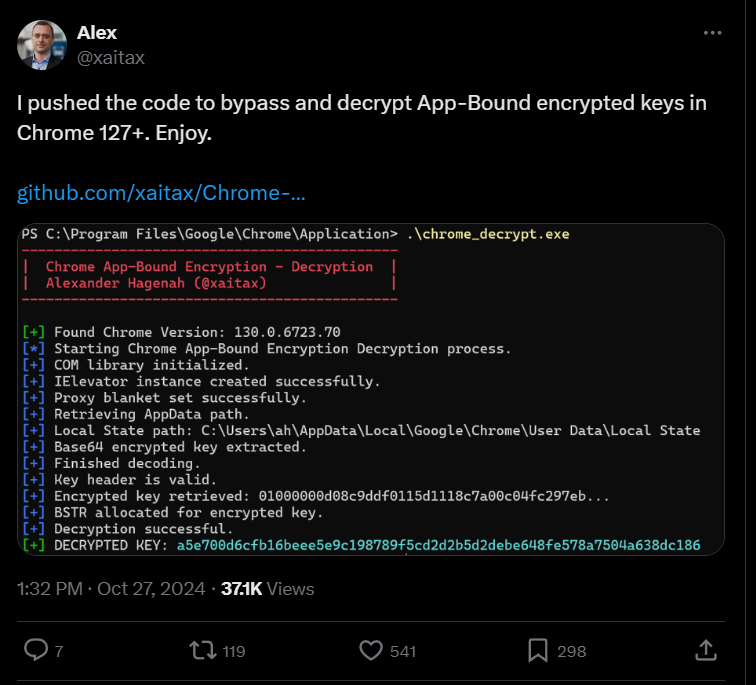
A new tool that bypasses Google Chrome's latest cookie encryption system was created by cybersecurity researcher Alexander Hagenah. The “Chrome App Bound Encryption Decryption” tool enables the extraction of saved credentials from the Chrome browser, posing potential security risks for users who rely on Chrome for storing sensitive data.
Google introduced its Application-Bound (App-Bound) encryption in July (Chrome 127) to bolster defenses against infostealer malware by encrypting cookies using a Windows service running with SYSTEM privileges.
This was intended to safeguard cookies and other sensitive data from unauthorized access, requiring malware to gain SYSTEM privileges to decrypt the information.
However, by September, various info-stealers had found workarounds to this protection, threatening the confidentiality of Chrome users' data. The new tool is publicly available on GitHub, allowing anyone to utilize Hagenah's method for decrypting cookie data stored in Chrome's Local State file.
The tool operates by copying an executable into the Google Chrome directory, a folder protected by administrator privileges. Many Windows users, particularly individuals, use accounts with these privileges, simplifying unauthorized access for malicious actors.
According to cybersecurity expert g0njxa, the tool illustrates methods that some infostealers have already surpassed. The tool's approach, similar to early bypass techniques used by malware like Lumma, utilizes Chrome's IElevator service through COM to decrypt cookies.
However, newer methods now employ indirect decryption without directly interacting with Chrome's Elevation Service, making them less detectable.
Google acknowledges the ongoing "cat and mouse" game with infostealer developers and emphasizes that requiring admin privileges is a step towards enhancing security. Despite these developments, the threat from information-stealing malware remains significant, with increasing attacks exploiting zero-day vulnerabilities and deceptive tactics.