Novel PE32 Ransomware Uses Telegram-Based C2, Exposes Bot Token and Group Chat ID in the Process
- The new PE32 Ransomware combines chaotic execution with poor security hygiene.
- Its key features include its use of the dual ransom model and leveraging Telegram as a C2 channel.
- PE32 exposes its Bot Token and Group Chat ID within its code, leaving its infrastructure open to exploitation.
A new ransomware strain, dubbed PE32, has emerged, adopting Telegram as its primary command-and-control (C2) channel. PE32 distinguishes itself largely through its operational simplicity rather than coding sophistication.
Among the highlights of its modus operandi are fast encryption, a basic approach, and high visibility behavior. Despite its amateur coding and lack of sophisticated evasive measures, PE32 has begun to cause damage by encrypting files and pressuring victims with dual-layered ransom demands.
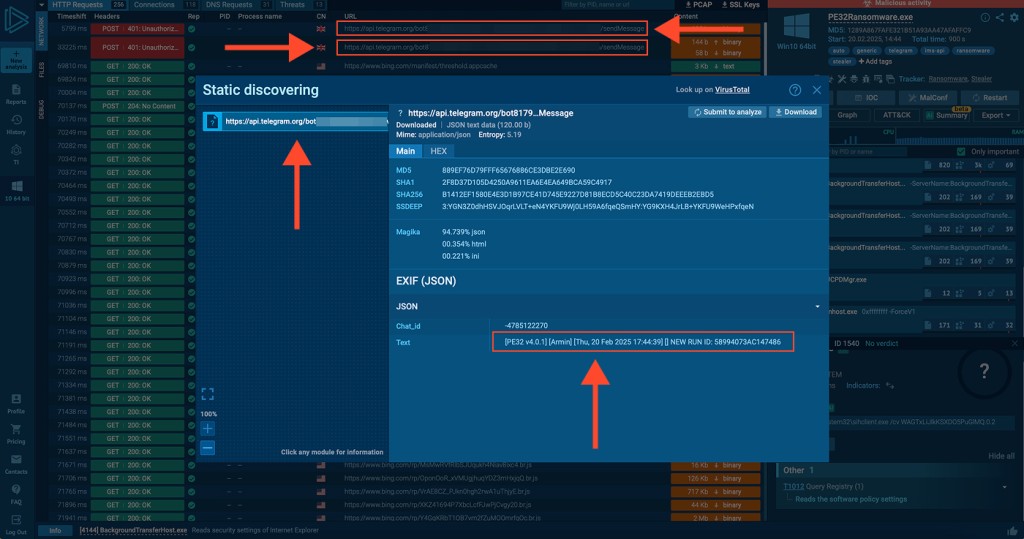
The cybercriminals demand one fee to unlock encrypted files and another to prevent data leaks and operate exclusively through Telegram bot communication, exposing bot tokens within its code and leaving its operations vulnerable to manipulation.
The approach lacks stealth measures, using exposed libraries and noisy execution, leading to easily detectable footprints, while no data exfiltration capabilities, reliance on common Windows libraries, and a lack of obfuscation make it amateurish yet effective in causing disruption.
While relying on Telegram for C2 activity, the malware exposes its Bot Token and Group Chat ID within its code, leaving its infrastructure open to exploitation. These flaws enable analysts to disrupt its operations by intercepting communications or flooding Telegram with bogus activity.
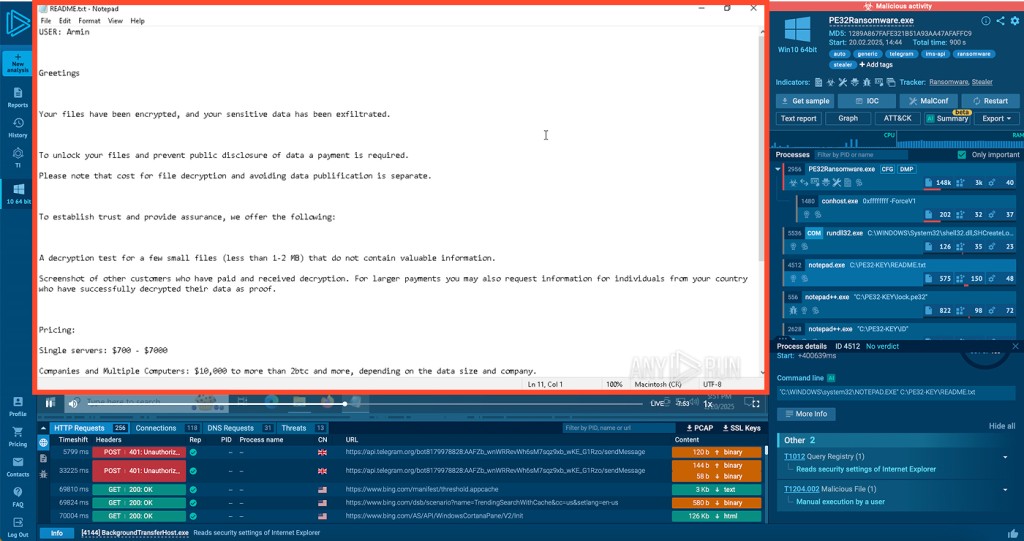
When executed, PE32 immediately prompts its operator to choose an encryption scope and proceeds to noisily encrypt visible directories, such as the desktop, to quickly lock access to files using the .pe32s extension.
Adding to the confusion, it creates a directory named "PE32-KEY" on the root drive for storing files related to its operations, including the ransom note, where payouts vary from $700 to $7,000 for individual machines or servers and $10,000 to 2 BTC (or more) for corporate targets.
Victims are instructed to follow up using Telegram or Gmail, reinforcing the malware's reliance on easily observable public communication systems. Its inability to select valuable files and chaotic execution further amplify operational disorder.