Novel EAGERBEE Variant Uses Sophisticated Backdoor Techniques to Target ISPs and Govts
- A new variant of the EAGERBEE malware was observed to display advanced stealth capabilities and backdoor techniques.
- This time, the targets are internet service providers and government entities in the Middle East.
- The malware is part of broader cyber espionage campaigns, including those conducted by a Chinese state-aligned cluster.
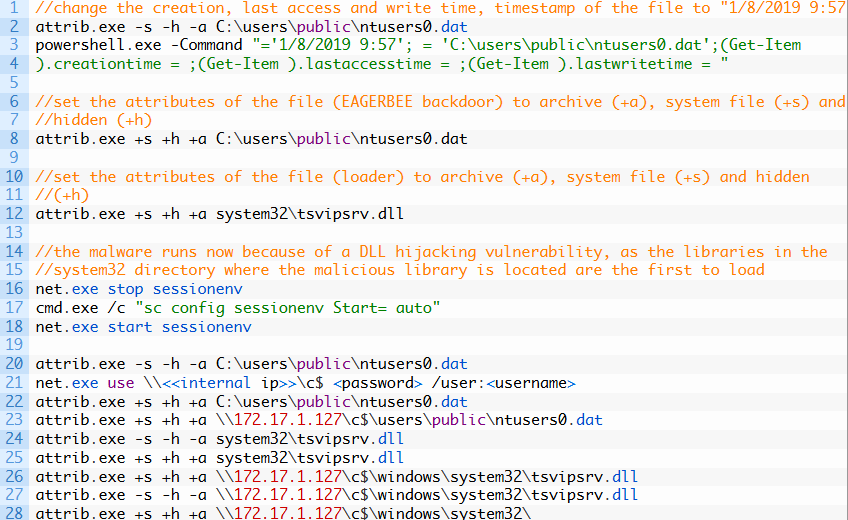
A newly detected variant of the EAGERBEE (aka Thumtais) malware framework has been uncovered, targeting internet service providers (ISPs) and government entities in the Middle East with advanced backdoor capabilities and memory-resident architecture that significantly bolsters its stealth capabilities.
The novel malware strain demonstrates a significant evolution in functionality, enabling it to deploy additional payloads, manage file systems, and execute command shells, according to researchers at Kaspersky, who attributed this malware framework with medium confidence to a threat actor known as CoughingDown.
Initially documented by Elastic Security Labs, EAGERBEE was linked to REF5961, a state-sponsored intrusion set featuring command-and-control (C2) capabilities and SSL encryption to deliver post-exploitation executables, with a focus on espionage.
Further analysis revealed EAGERBEE's involvement in broader cyber espionage campaigns, including those conducted by a Chinese state-aligned cluster identified as Cluster Alpha. This group leveraged EAGERBEE as part of a campaign, codenamed Crimson Palace, that targeted high-profile government organizations in Southeast Asia to exfiltrate sensitive political and military secrets.
Cluster Alpha's operations reportedly overlap with other Chinese-linked threat actors such as BackdoorDiplomacy, REF5961, Worok, and TA428. Notably, BackdoorDiplomacy exhibits tactical parallels with CloudComputating (aka Faking Dragon), a group associated with QSC—a modular malware targeting the South Asian telecom industry.
EAGERBEE's evolution includes a modular plugin-based architecture that operates primarily in memory, making it more challenging to detect with traditional endpoint security tools. Its injector DLL component activates a backdoor module that gathers system information and exfiltrates it to a remote server, establishing communication through a TCP socket.
Subsequent operations rely on the Plugin Orchestrator, which performs tasks such as reporting system information, harvesting details about running processes, receiving and injecting plugins into memory, unloading or removing plugins from the memory list, or checking whether specific plugins are loaded.
Each plugin supports functionalities, including file operations, process management, remote connectivity, system service oversight, and network connection monitoring. Additionally, EAGERBEE obscures its activity by injecting malicious code into legitimate processes.
The malware framework has been observed targeting several organizations in East Asia. Notably, two victims were compromised using the ProxyLogon vulnerability (CVE-2021-26855). This vulnerability enabled attackers to deploy web shells and execute commands on compromised servers, ultimately leading to the deployment of the EAGERBEE backdoor.