Novel ‘DoubleClickjacking’ Attack Aims at Website Compromise and Account Takeover
- A new variation of ‘double-click’ attacks compromise websites and take over accounts with minimal user interaction.
- Users are shown an OAuth authorization dialog or account settings confirmation page that contains hidden harmful elements.
- Due to its ability to avoid detection, Salesforce, Slack, Shopify, crypto wallets, and VPNs are vulnerable.
A newly discovered variation of the infamous clickjacking technique, dubbed DoubleClickjacking, can sidestep existing website security measures. This sophisticated attack allows threat actors to take over user accounts and execute unauthorized actions with minimal detection.
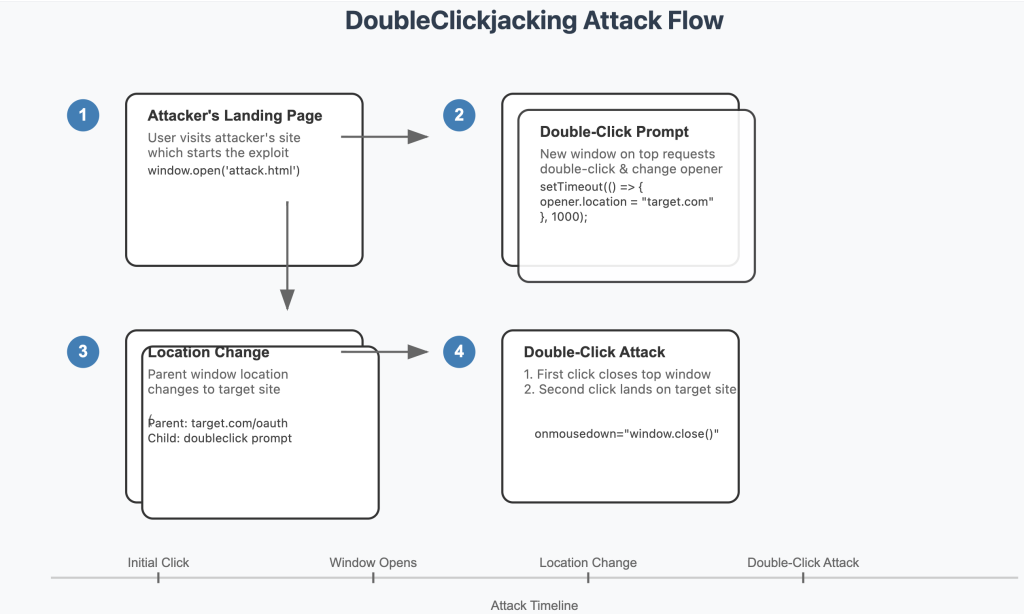
Security researchers, including those from cybersecurity firm PAULOS, have demonstrated how this attack unfolds. The attacker creates a malicious webpage featuring a seemingly innocent element, such as a “Double-click to verify” button.
The first click triggers a script to manipulate the browser window, replacing or closing the current content and replacing it with a sensitive page, such as an OAuth authorization dialog or account settings confirmation page.
The second click lands on the newly loaded, hidden sensitive page behind the initial prompt, authorizing harmful actions without the user’s awareness.
Once the sequence is complete, attackers gain access to sensitive permissions or achieve unauthorized actions on behalf of the victim, such as account takeovers, app authorizations, or even financial transactions.
DoubleClickjacking builds on the decade-old concept of traditional clickjacking, where unsuspecting users are duped into clicking on hidden or disguised elements, often triggering harmful actions.
This malicious method requires users to perform two clicks, and attackers exploit timing discrepancies between user inputs, manipulating browser behavior to execute unauthorized actions.
This variation of clickjacking is uniquely concerning due to its ability to bypass traditional security mechanisms, such as X-Frame-Options headers, Content Security Policies (CSP), and SameSite cookies. Also, it requires minimal user interaction, with just two simple clicks needed.
Tests indicate major websites, including Salesforce, Slack, and Shopify, are vulnerable to DoubleClickjacking. Beyond websites, browser extensions like crypto wallets and VPNs are also at risk, allowing attackers to authorize transactions or disable critical security features.
If you are a developer, protect your website from DoubleClickjacking: "Implement the Protective Library on Sensitive Pages: Any page handling OAuth scope verification, payment confirmations, or other high-privilege actions should include the defensive script until browsers provide solutions."