Novel ‘Confucius’ APT Android Spyware Discovered by Researchers
- Researchers have discovered two new spyware tools deployed by the ‘Confucius’ APT.
- The group was careless enough to expose their data exfiltration databases online.
- Both malware appear to be evolutions of commercial surveillance tools.
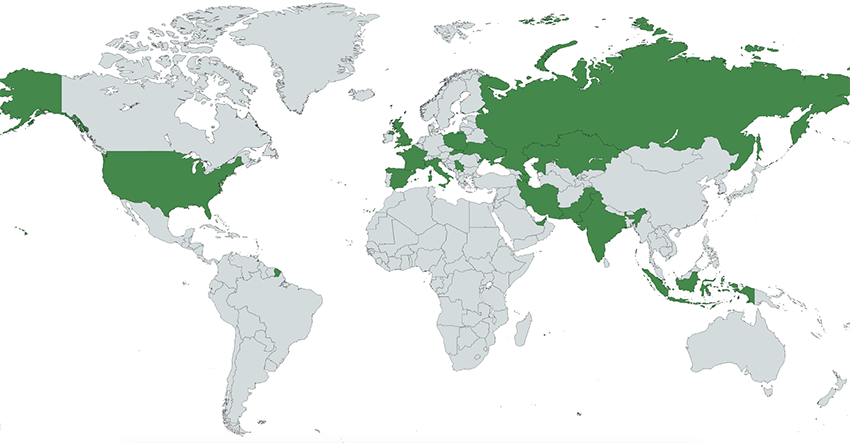
Researchers of the Lookout Threat Intelligence team have discovered two new Android spyware samples, namely “Hornbill” and “SunBird,” that apparently belong to the ‘Confucius’ APT group. This is a pro-India actor who has been active since 2013 and which, according to the report, is most probably state-sponsored.
As such, it focuses on cyber-espionage operations, mainly against Pakistan and various other South Asian targets. The group has been linked with desktop malware in the past, but since 2017, they have started going mobile too.
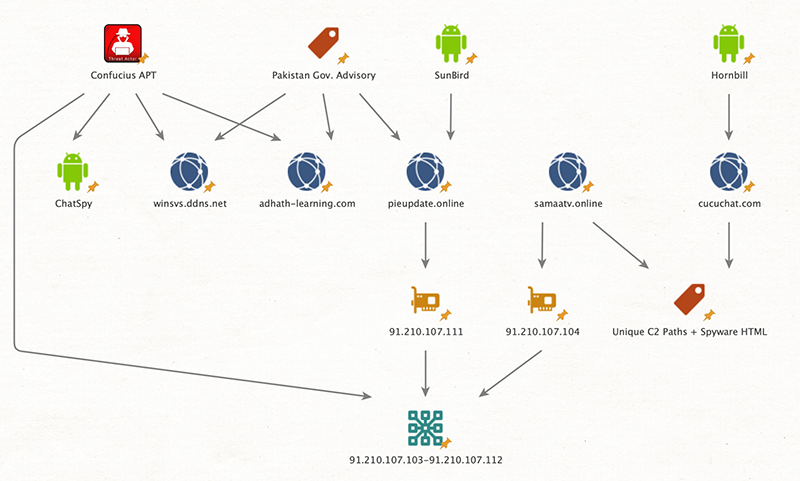
The Lookout report details how the actors are actually disguising their spyware tools as applications that are of special interest to Pakistanis, like “Kashmir News” and “Quran Majeed.” Apart from the specific targeting, there are also apps made specifically to pose as system components so that the users will leave them alone, like the entirely fictional “Google Security Framework.” Also, Hornbill samples often impersonate chat platforms like “Fruit Chat,” “Cucu Chat,” and “Kako Chat.”
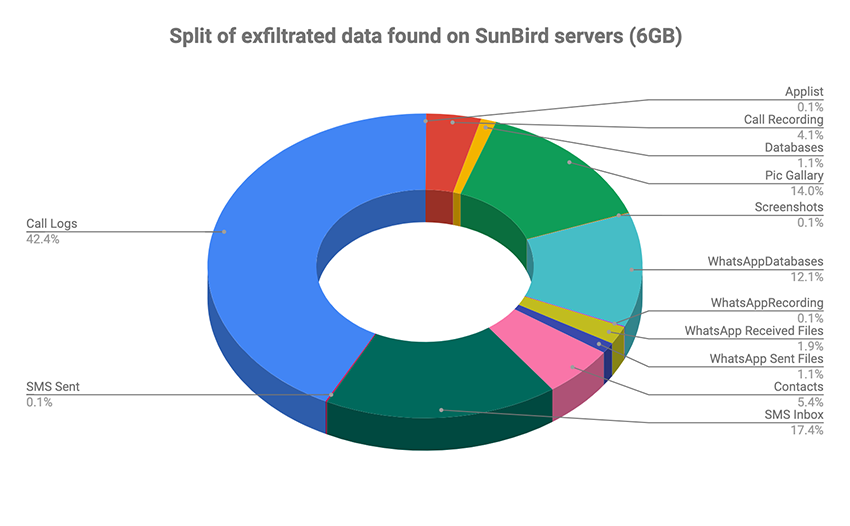
The two malware tools are quite similar in terms of capabilities, but they have some differentiating points. Both can extract call logs, contact lists, device ID details, geolocation data, images stored on the SD card, and WhatsApp voice notes. They can also gain admin privileges, take screenshots, take photos with the camera, record audio through the microphone, record calls, and scrape WhatsApp messages.
In addition to these, SunBird is also a RAT (remote access trojan) tool and can exfiltrate additional data like:
- List of installed applications
- Browser history
- Calendar information
- BlackBerry Messenger (BBM) audio files, documents, and images
- WhatsApp Audio files, documents, databases, voice notes, and images
- Content sent and received via an IMO instant messaging application
Also, it can perform the following additional actions:
- Download attacker-specified content from FTP shares
- Run arbitrary commands as root, if possible
- Scrape BBM messages and contacts via accessibility services
- Scrape BBM notifications via accessibility services
The Hornbill spyware has evolved from the commercial tools ‘MobileSpy’ made by the now-defunct Retina-X. Somehow, Confucius got their hands on the source code of the tool, as they also did with ‘BuzzOut,’ which appears to be the basis for SunBird.
The researchers have analyzed over 18GB of exfiltrated data that they were able to access thanks to a misconfiguration of six databases, indicative of extreme carelessness from the ‘Confucius’ group. Based on that, they were able to figure out who’s being targeted, confirming entities like the Pakistan Atomic Energy Commission, individuals with numerous contacts in the Pakistan Air Force (PAF), as well as officers responsible for electoral rolls (Booth Level Officers) located in the Pulwama district of Kashmir.
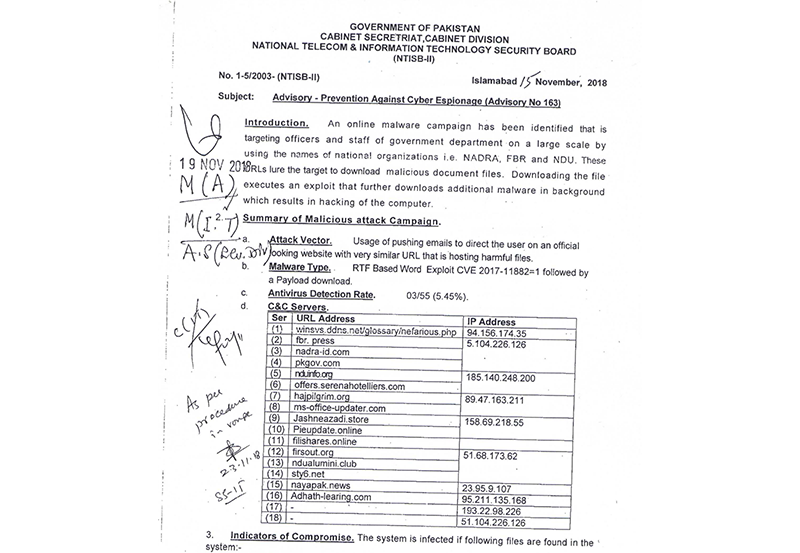
The attribution to Confucius is considered to be beyond doubt for the researchers, as there are C2 infrastructure overlaps with past operations, methodology similarities, and IP address evidence that has already been identified by the Pakistani intelligence agency and has been included in relevant advisories published way back in 2018.