Novel MacOS-Based Banshee Infostealer Targets Crypto Wallets, Browsers & Their Extensions
- A new info-stealer targets macOS and tries to harvest data from the compromised machines.
- It shows password phishing techniques and focuses on the crypto wallet, system, and browser data.
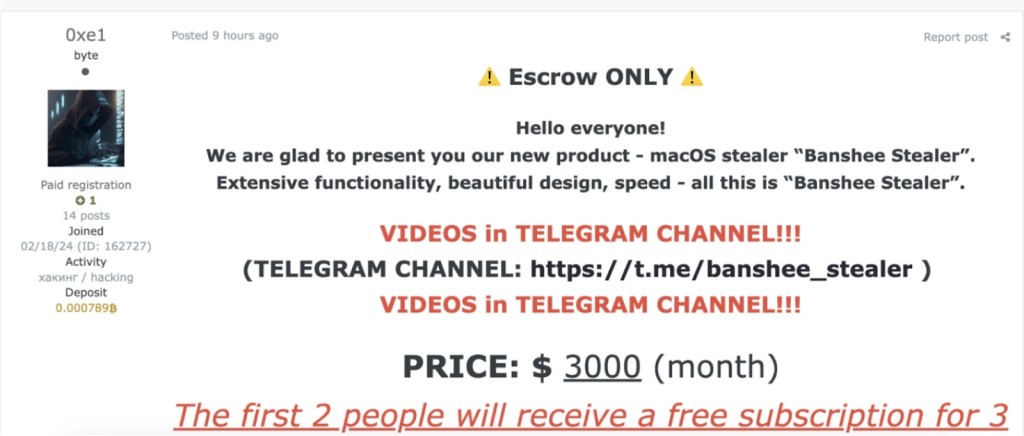
- The new Banshee Stealer is sold on the Dark Web as Ransomware-as-a-Service for a notably steep price.
The new Banshee Stealer malware works on macOS x86_64 and ARM64 environments and targets system and browser data and cryptocurrency wallets, the latest Elastic Security Labs report says. It also preys on a wide range of browsers and around 100 browser extensions.
Reportedly developed by Russian threat actors, Banshee Stealer Ransomware-as-a-Service (RaaS) was introduced on a Dark Web forum this month for a $3,000 monthly subscription. The malware can execute tasks such as anti-debugging measures, language checks, data collection, and exfiltration.
It harvests system information and data from cryptocurrency wallets like Exodus, Electrum, Coinomi, Guarda, Wasabi Wallet, Atomic, and Ledger, and various Web browsers, such as Chrome, Firefox, Brave, Edge, Vivaldi, Yandex, Opera, and OperaGX.
It also exfiltrates data from approximately 100 browser plugins and can perform password phishing as well. An Osascript prompt phishes the victim’s password, invoking the need to update the system settings to launch the app.
The new info stealer relies on basic techniques to evade detection and parses the user-preferred canonicalized language to avoid infecting systems where Russian is the primary language. Even though Banshee Stealer doesn’t employ sophisticated obfuscation or have an overly complex, it displays dangerous capabilities when it comes to harvesting sensitive user data.
Recently, an SMS stealer campaign targeting Android devices was observed in 113 countries around the world, including India, Russia, Brazil, Mexico, the U.S., and more. The threat actors used automated Telegram bots and fake ads for legitimate app stores to distribute over 107,000 malware samples, intercepting users’ one-time passwords coming from over 600 services.
Also, cybercriminals increasingly use YouTube lures such as ads for crypto giveaways and videos that appear to be tutorials for popular software that include a link to a website for downloads, which hide various info-stealing malware.