Novel Arcane Stealer Threatens YouTube and Discord Communities, Targets VPNs, Crypto Wallets
- A new, sophisticated stealer is distributed via YouTube and Discord links containing malicious archives.
- Arcane harvests logins, passwords, credit card data, tokens, and other credentials from various Chromium and Gecko-based browsers.
- However, it also targets VPNs, emails, messaging apps, crypto wallets, gaming clients and services, and others.
YouTube videos and Discord channels are leveraged to distribute a new infostealer called Arcane Stealer disguised as game cheats or tools. It collects a vast amount of sensitive data from users, targeting various applications and services across gaming, VPNs, and messaging platforms.
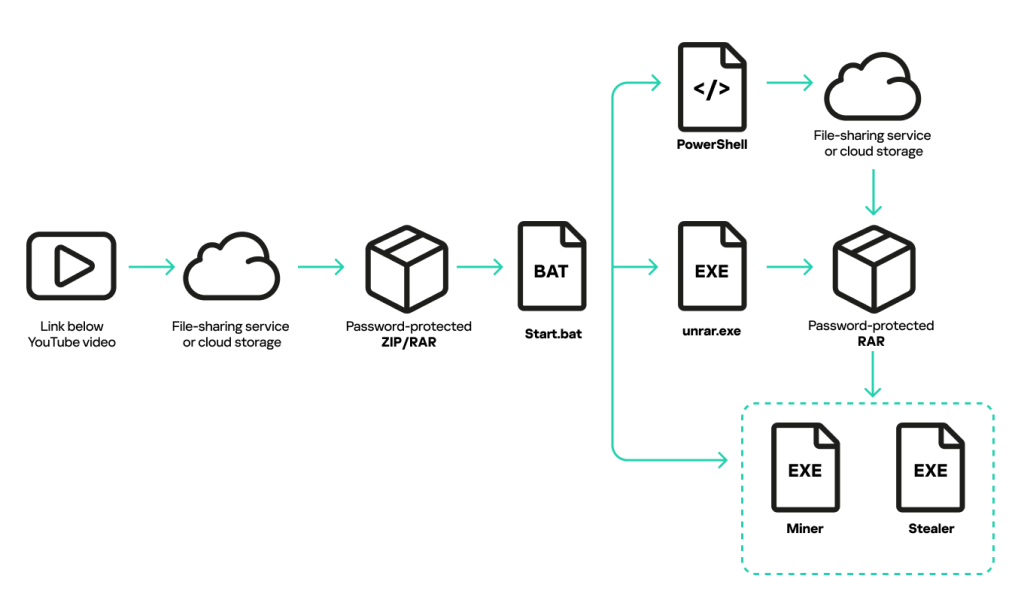
Kaspersky security researchers have been observing an infostealer campaign that uses YouTube videos to promote downloadable game cheats. These videos include links to password-protected archives.
Once downloaded and unpacked, this sophisticated malware asks unsuspecting users to execute a batch file that triggers the download and activation of the malware while simultaneously disabling SmartScreen protection on their systems.
The archive contains two executables – a miner and a stealer. Before late 2024, the stealer was a Phemedrone Trojan variant named VGS by the attackers. A new, frequently updated Arcane Stealer then replaced VGS in the same campaign, borrowing much from other stealers.
Further distribution efforts have included ArcanaLoader, a tool promoted heavily through Discord, which advertises popular cheats and cracks but secretly delivers the Arcane Stealer.
The Arcane Stealer harvests a broad range of data, including but not limited to:
- VPN clients: OpenVPN, Mullvad, NordVPN, IPVanish, Surfshark, Proton, hidemy.name, PIA, CyberGhost, ExpressVPN
- Network clients and utilities: ngrok, Playit, Cyberduck, FileZilla, DynDNS
- Messaging apps: ICQ, Tox, Skype, Pidgin, Signal, Element, Discord, Telegram, Jabber, Viber
- Email clients: Outlook
- Gaming clients and services: Riot Client, Epic, Steam, Ubisoft Connect (ex-Uplay), Roblox, Battle.net, various Minecraft clients
- Crypto wallets: Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, Atomic, Guarda, Coinomi
Notably, the Arcane Stealer uses advanced techniques like exploiting Chrome's debugging port and DPAPI (Data Protection API) to extract critical data, including browser encryption keys.
Though the malware has global potential, the campaign primarily targets Russian-speaking users based on its telemetry data, the language of communication on associated Discord servers, and the audience of the gaming cheat videos.