
North Korean State-Sponsored APT45 and Play Ransomware Launch a Collaborative Cyberattack
- The North Korean APT45 threat actor and Play Ransomware were observed working together in a cyberattack.
- Privilege escalation, uninstalling EDR sensors, and harvesting browser history, credentials, and credit card data were part of the attack.
- The state-backed gang gained initial access through a compromised user account.
North Korean state-sponsored actors, known as Jumpy Pisces, also referred to as Andariel, APT45, DarkSeoul, have been implicated in a cyber attack involving the notorious Play ransomware in an activity observed from May to September 2024.
This marks the first recorded collaboration between APT45 and an underground ransomware network. This collaboration underscores the continued financial motivations of North Korean cyber operations.
Palo Alto Networks' Unit 42 report indicates that APT45 may have collaborated with Play, a ransomware operation that has impacted approximately 300 organizations since October 2023.
The incident reveals APT45 gained initial access through a compromised user account in May 2024, utilizing the Sliver command-and-control (C2) framework and a backdoor called Dtrack.
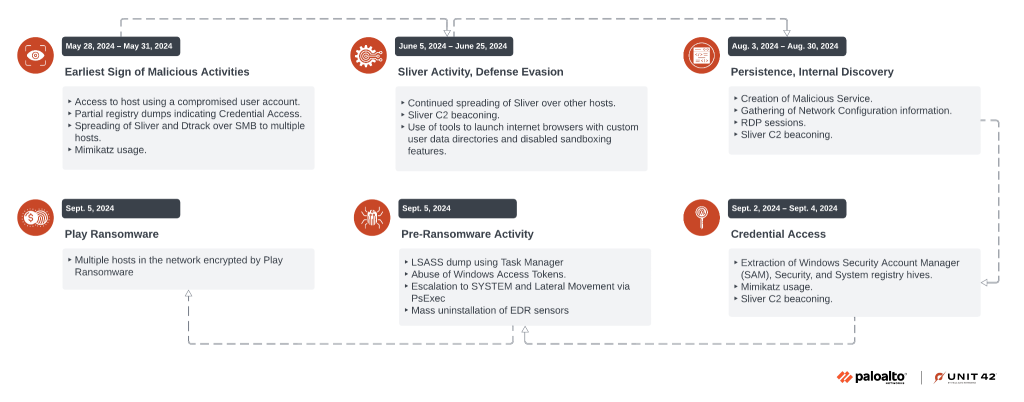
The operation involved credential harvesting, privilege escalation, and uninstallation of endpoint detection and response (EDR) sensors—all typical pre-ransomware activities. Additionally, a trojanized binary capable of harvesting browser history and credit card information was utilized.
Communication with the Sliver C2 server, a hallmark of the intrusion, persisted until just before the ransomware deployment, raising questions about the nature of the collaboration. It remains unclear whether APT45 has officially aligned with Play ransomware or merely acted as an initial access broker (IAB).
Active since 2009, APT45 is affiliated with North Korea's Reconnaissance General Bureau (RGB) and has previously deployed ransomware strains SHATTEREDGLASS and Maui. Lately, APT45 has been actively targeting critical infrastructure and military operations located in the U.S., trying to steal nuclear and military secrets from government facilities and agencies.
Recently, FBI warned that North Korean threat actors increasingly employ sophisticated social engineering tactics, impersonating prominent people or entities via fake websites as their main targets are DeFi, crypto companies, and connected entities.












