North Korean Spyware ‘KoSpy’ Attributed to APT37 Targets Android Devices
- Security researchers discovered a new Android spyware they linked to North Korea-aligned threat actor APT37.
- KoSpy can collect and transmit sensitive data, such as location, media, and SMS content.
- The hackers falsely promote KoSpy as legitimate utility apps like File Manager, Software Update Utility, and Kakao Security.
A novel Android spyware tool dubbed "KoSpy" has been discovered and linked to North Korea's advanced persistent threat (APT) group APT37, also known as North Korea-aligned threat actor ScarCruft or APT-C-28.
This spyware, first detected in March 2022, continues to pose a threat, with new samples surfacing as recently as March 2024, security researchers from Lookout say.
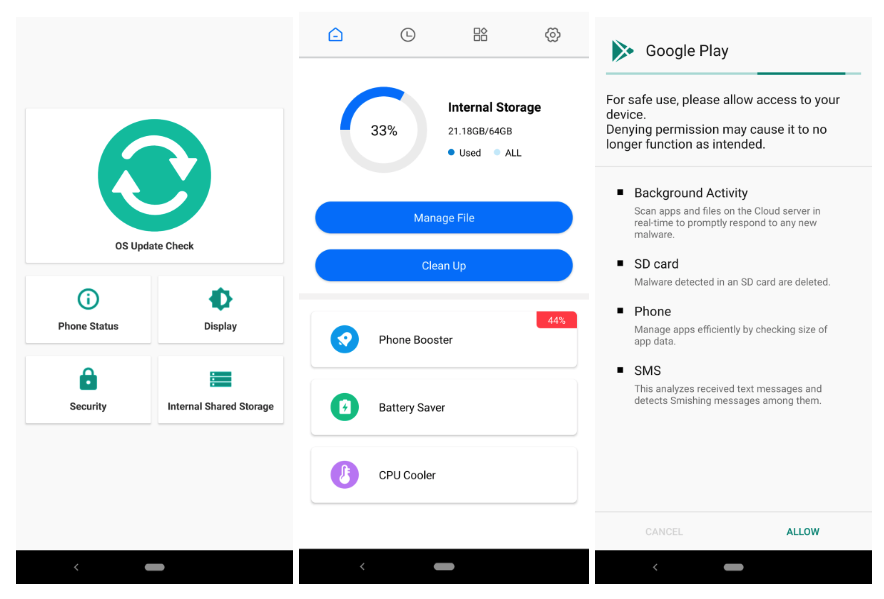
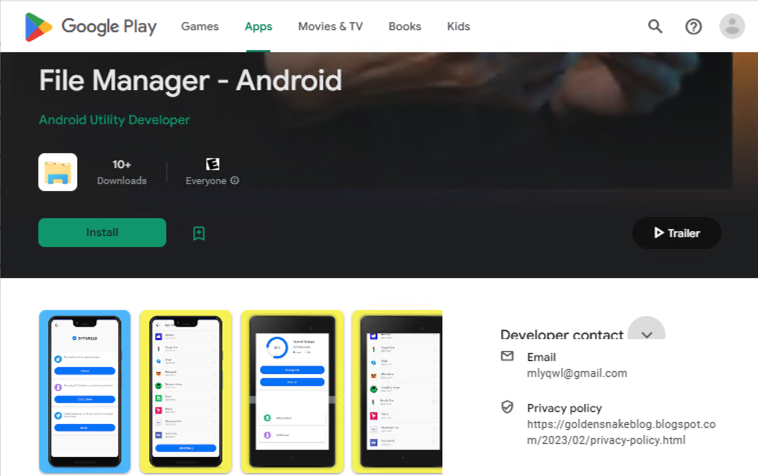
KoSpy masquerades as legitimate utility apps, including Phone Manager, Smart Manager, File Manager, Software Update Utility, and Kakao Security, and appears designed to target Korean and English-speaking users.
Once installed, the spyware allows attackers to collect SMS texts, call logs, device location, local files, and keystrokes. Attackers can also take photos with the cameras, capture screenshots, or record the screen and audio. It employs dynamically loaded plugins to extend its malicious functionality, making it highly adaptable.
KoSpy has been distributed through the Google Play Store and third-party marketplaces like Apkpure. While Google has removed the malicious apps and deactivated associated Firebase projects, they had already been downloaded numerous times before being taken down.
KoSpy's sophisticated two-stage command-and-control (C2) infrastructure includes an “on”/”off” switch and the C2 server address that retrieves initial configurations from a Firebase cloud database.
Lookout researchers attribute KoSpy to APT37 with "medium confidence." Yet, links to the North Korean group APT43 (a.k.a. Thallium, Kimsuky) highlight a shared infrastructure and overlapping tactics.
APT37 has been active since 2012 and is known for conducting cyberespionage campaigns primarily targeting South Korea.
KoSpy's C2 servers have been tied to previously identified malicious infrastructure linked to APT37. For example, some domains KoSpy uses resolve to IP addresses in South Korea that have hosted suspicious domains associated with earlier North Korean malware campaigns, such as Konni and Kimsuky.